New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
JWT not working on Android #744
Comments
|
Hello!
The reqbin site or Anyway, from the JJWT documentation's Features section: RSASSA-PSS algorithms are only available on JDK >= 11 natively. If not on JDK >= 11, you can add BouncyCastle to the runtime classpath, and that will support RSASSA-PSS algorithms. What JDK were you using in IntelliJ? Did you enable BouncyCastle or SpongyCastle in Android? I hope that helps! Please let us know! |
|
Just now, changed Android Studio jdk from 11.0.10 to 11.0.12 and the error is same as on jdk 11.0.10 - Caused by: io.jsonwebtoken.security.SignatureException: Unavailable RSA Signature algorithm 'RSASSA-PSS'. |
|
added bcprov-ext-jdk18on-171.jar (BouncyCastle last jar - implementation files('libs/bcprov-ext-jdk18on-171.jar') as a library in Android Studio, 2022-06-05 17:24:36.890 3053-3053/com.eyehail.smallproject E/AndroidRuntime: FATAL EXCEPTION: main |
|
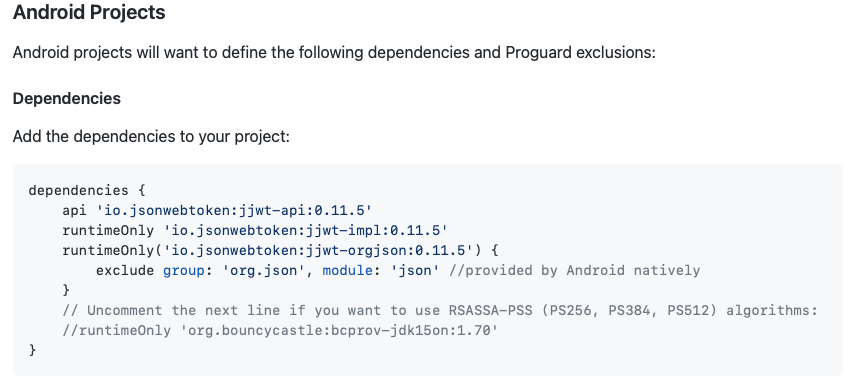
You may not have the correct dependency. Our documentation shows: // Uncomment the next line if you want to use RSASSA-PSS (PS256, PS384, PS512) algorithms:
//'org.bouncycastle:bcprov-jdk15on:1.70', |
|
From our Android documentation: Try the |
|
Out of curiosity, what if you explicitly registered the BouncyCastle provider in your code first, before using JJWT? For example: Provider provider = new org.bouncycastle.jce.provider.BouncyCastleProvider();
Security.addProvider(provider);Does that fix it? If not, is there a sample project you could provide for us to test with? I am unable to reproduce the problem. |
doesn't fix.. sample project on Android - https://github.com/t0in4/small_project the same working project IntelliJ - https://github.com/t0in4/simple_project_intellij |
|
It looks like current versions of Android do not support RSASSA-PSS Similar to what @lhazlewood mentioned, you would need to add a Provider that has that capability. It looks like we can narrow things down to the call of I'd suggest trying the following in your environment: java.security.Signature.getInstance("RSASSA-PSS")I'd expect the above to fail with the same exception: Provider provider = new org.bouncycastle.jce.provider.BouncyCastleProvider();
Security.addProvider(provider);
java.security.Signature.getInstance("RSASSA-PSS", "BC");
// and/or
java.security.Signature.getInstance("RSASSA-PSS", Security.getProvider("BC"));Does this work? |
|
Hello! |
|
I think Android might ship with their own old/deprecated BC provider. Try removing that and adding yours: public class MyApplication extends Application {
static {
Security.removeProvider("BC");
Security.addProvider(new new org.bouncycastle.jce.provider.BouncyCastleProvider());
}
} |
|
Hello! |
|
@t0in4 possibly. If we have narrowed it down to a You might bet better insight into the problem on an Android-specific forum or Stack Overflow. It sounds like you are only attempting to use All that said, I DO think we should to document your findings on this issue in the JJWT readme if you can get a definitive answer on what is going on here. Potentially also add some sort of nice error message. |
|
I don't know what the issue is either - lots of answers on StackOverflow say BouncyCastle works just fine with Android, especially for anything after 2018 that I could find. My last suggestion of removing the provider and then manually adding it back in seems to work for others on Android. I would definitely ask on StackOverflow.com and see if anyone with more Android expertise can help. If you or anyone else reading this finds a solution, please do reply and let us know what it is so we can add it to the JJWT documentation. We would be grateful! 🙏 |
|
Thank you, I am very appreciated for your responses. Just now, i check one more time - and i got an output without errors but token still cannot validated by yandex service https://github.com/t0in4/small_project/tree/working_but_with_jwt_validation_fails Becouse, the same code, but written in IntelliJ is working and pass JWT signature validation from yandex side https://github.com/t0in4/simple_project_intellij
No, i try to use yandex translate service - and yandex iam_token is expires in 12 hours (and in official documentation, they recomend to gain new iam_token every hour), so i need to call it often from application. Thank you one more time! |
Yes, something is weird here. Please do ask on |
|
Ok, i will try to ask on StackOverflow. |
|
Please let us know if you find a solution! |
|
I am ask on StackOverflow direct link is |
|
Your StackOverflow post indicates that, after registering BouncyCastle, a JWT is created on Android without any exceptions/problems, but yandex cannot validate it. So I'm curious - have you tried the following tests?
If both of those work successfully, the problem is with yandex, not with Android. |
|
Thank you! They are not same The order of representation of the payload data is not same. In token from IntelliJ Idea the "aud" is first and "iss" is second, in token from Android Studio the "iss" is first and "aud" is second. |
|
The order doesn't matter for JWT claims (headers or payloads). It's basically a hashmap of key/value pairs, so the order could change. As long as the content is the same you would be all set. |
|
Thank you! |
|
Yandex support says that i have to add parameter to header - "type": "JWT", |
|
Hey @t0in4! Fun Fact: There is an official registry of additional JWT claims names: https://www.iana.org/assignments/jwt/jwt.xhtml |
|
If Yandex requires the |
|
changed to "typ" - error is same { |
|
Is the receiving end configured with the correct key? |
|
Hello! |
|
Sorry, @t0in4 I think I missed some part of the thread. |
|
As you both told to me the solution is: Above code annihilate the error "no such algorithm: RSASSA-PSS for provider BC" And the checking both tokens give a same output on site https://jwt.io But when i making POST request to get a iam_token - the IntelliJ Idea's token return a iam_token, but the Android Studio's token return an error "JWT signature validation fails". The orders of payload is not equal - data is equal but order of representation is not. |
|
Ahh cool! I think I read one of your previous posts incorrectly! Thanks for clarifying! Here is what I would recommend. Jwts.parserBuilder()
... // your settings
.build()
.parse(jwtTokenString);Once you have that working, use the token string created by your Android app. |
|
Thank you! // decoded output of token from IntelliJ Idea // encoded token from Android Studio // error when decoding token from Android Studio Process finished with exit code 1` Whole code of decoder on https://github.com/t0in4/decode_android_JJWT/tree/master |
|
I issued a PR to your sample project here: https://github.com/t0in4/small_project/pull/1/files This PR enables the BouncyCastle provider correctly, whereby the JWT PS* algorithms will work correctly. Note the However, the most important change was the following added to the main application class (how Kotlin does a companion object {
init {
Security.removeProvider("BC") // remove the legacy Android-specific 'BC' provider
Security.addProvider(BouncyCastleProvider()) // add the real BC provider
}
}This should be all that is necessary to resolve this. If so, please confirm. I'd like to close this issue ;) |
|
Cool! Code is amazing! Thank you! Yes, JJWT error is solved. Thank you all one more time. I'm very appreciated. Thank you sirs. |







Describe the bug
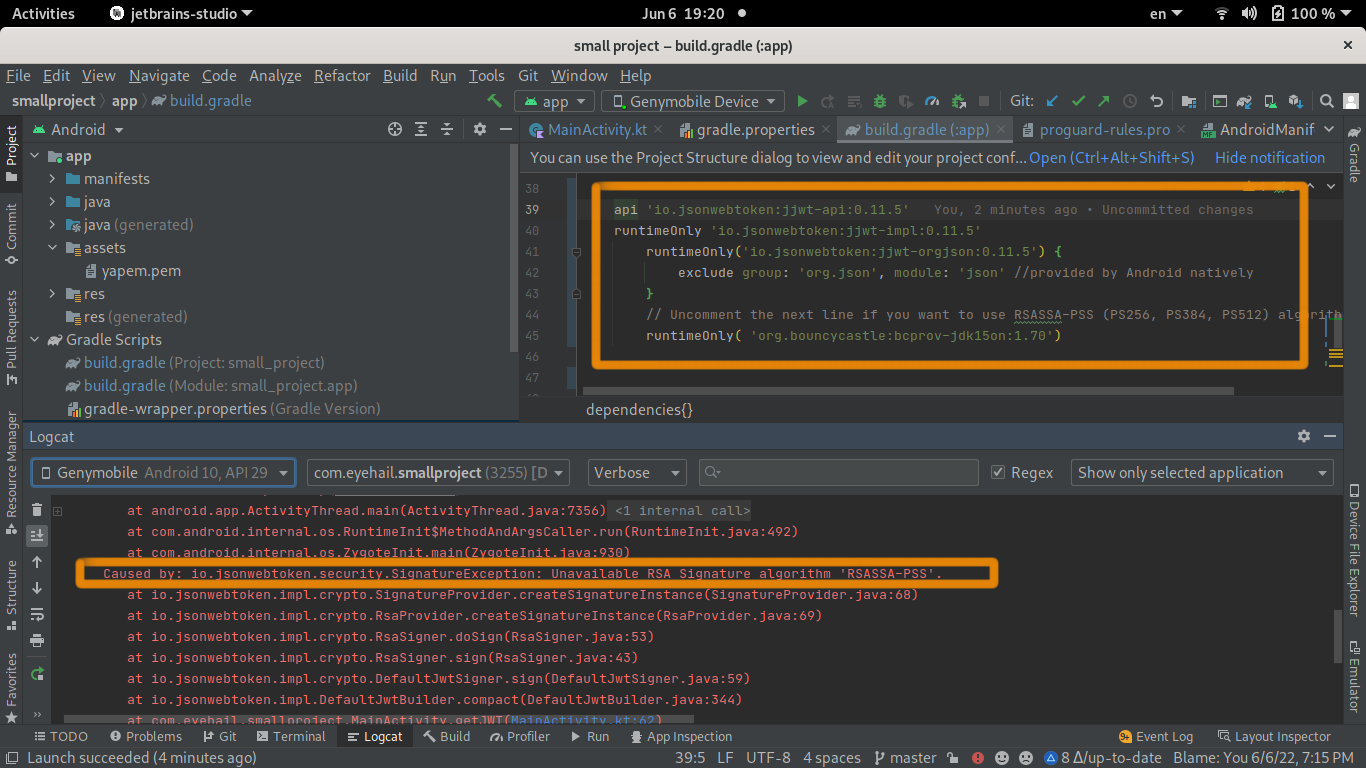
Code on Android it gives an error - Caused by: io.jsonwebtoken.security.SignatureException: Unavailable RSA Signature algorithm 'RSASSA-PSS'. code on Android
But same code in IntelliJ Idea console return a valid JWT token. code on IntelliJ Idea
Sometimes, when i launch first time after reload an Android code, it return a JWT token but when i check it - it is not valid token. (service return )
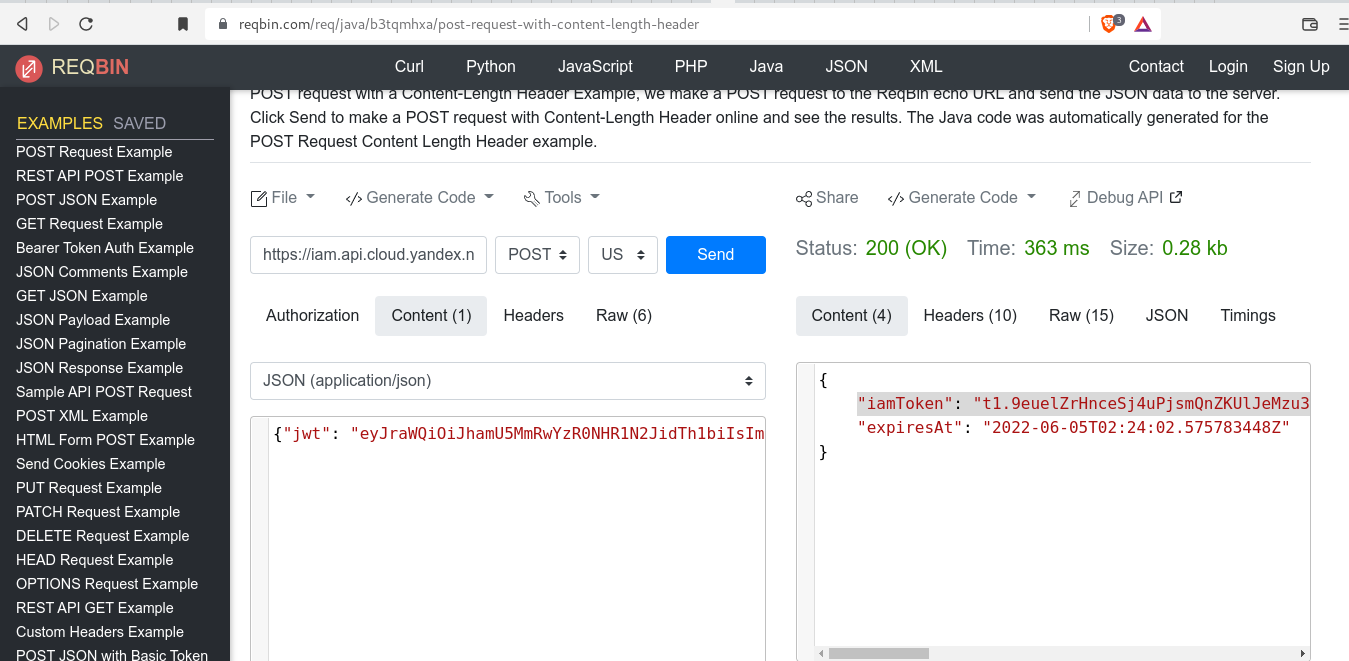
I check the correctness of token by free service https://reqbin.com/
To Reproduce
Steps to reproduce the behavior after gain a JWT token from Android:
Expected behavior
When i check JWT token from IntelliJ Idea console
the reqbin site return a message "iamToken": "t1.9euelZrHnceSj4uPjsmQnZKUlJeMzu3rnpWalpWPzsaSysbGjMeekIzJiY3l8_d9KRJr-e9nezht_d3z9z1YD2v572d7OG39zef1656VmsbNm4-cy4vLi4rInZ2Kx4qR7_0.WrOA-radhm9TNJvaoBcccf3-qku_KvPHpxQ9Livfdjb8DUonpXcGZ6KFB1xCIvn8iMRclFAl1kbrUrKfZ60LDw"
Screenshots
If applicable, add screenshots to help explain your problem.
IntelliJ Idea valid token

Android Studio non valid token

Android Studio error

Server Answers
The text was updated successfully, but these errors were encountered: