This article will guide you through the process to configure permissions to your Azure environment to do ARM tenant level deployments.
Note: The steps below requires you to use an identity that is local to the Azure AD, and not Guest user account due to known restrictions.
Enterprise-Scale reference implementation requires permission at tenant root scope "/" to be able to configure Management Group and create/move subscription. In order to grant permission at tenant root scope "/", users in "AAD Global Administrators" group can temporarily elevate access, to manage all Azure resources in the directory.
Once UAA role is enabled, User Access Administrator can grant other users and service principles within organization to deploy/manage Enterprise-Scale reference implementation by granting "Owner" permission at tenant root scope "/".
Once permission is granted to other users and service principles, you can safely disable "User Access Administrator" permission for the "AAD Global Administrator" users. For more information please follow this article elevated account permissions
1.1 Sign in to the Azure portal or the Azure Active Directory admin center as a Global Administrator. If you are using Azure AD Privileged Identity Management, activate your Global Administrator role assignment.
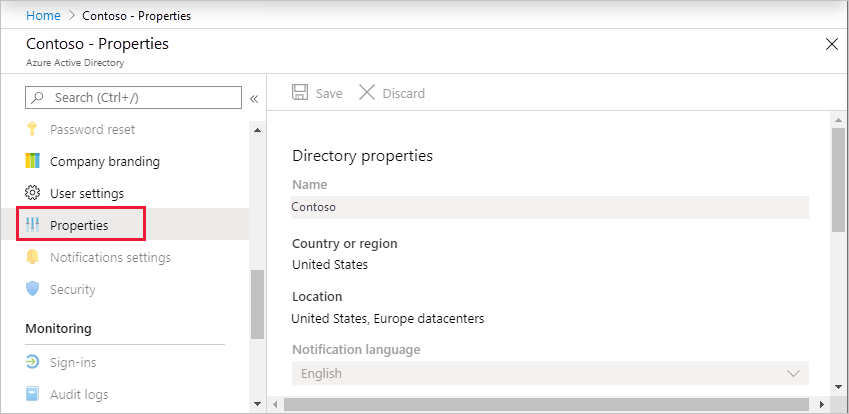
1.2 Open Azure Active Directory.
1.3 Under Manage, select Properties.
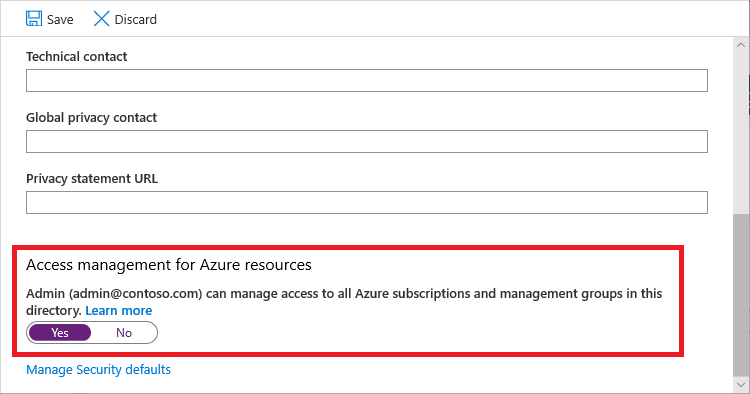
1.4 Under Access management for Azure resources, set the toggle to Yes.
Please ensure you are logged in as a user with UAA role enabled in AAD tenant and logged in user is not a guest user.
Bash
az role assignment create --scope '/' --role 'Owner' --assignee-object-id $(az ad user show -o tsv --query objectId --id '<replace-me>@<my-aad-domain.com>')PowerShell
#get object Id of the user
$user = Get-AzADUser -UserPrincipalName '<replace-me>@<my-aad-domain.com>'
#Assign Owner role to Tenant root scope ("/") as a User Access Administrator
New-AzRoleAssignment -Scope '/' -RoleDefinitionName 'Owner' -ObjectId $user.IdPlease note, it may take up to 15-30 minutes for permission to propagate at tenant root scope. It is highly recommended that you log out and log back in.
Please proceed with deploying reference implementation.