-
Notifications
You must be signed in to change notification settings - Fork 280
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Use WAS-DEFAULT-HOSTNAME HttpHeader to get slot name #1368
Comments
|
Other references: microsoft/ApplicationInsights-dotnet-server#872, microsoft/ApplicationInsights-dotnet-server#871, microsoft/ApplicationInsights-dotnet-server#314 |
|
We need to think about worker roles and telemetry reported in background threads. |
|
|
How would this work for something using IHostedService? Would telemetry from it just use the cloud role name from the last HTTP request, assuming it would be cached? I know it won't be a common case but it could be a strange corner case and possibly complicated further with percentage based traffic allocations. |
|
Pushing it to the next milestone as this is a relatively big change and we don't have the bandwidth to take it in this cycle. |
|
Update: There is no update yet on how to get this on webjobs or background jobs, so they'll continue to rely on the env variable. |
I stumbled upon this issue in our web apps as well. What is the status of this issue? At least we can get it right for the web apps, and create a seperate issue for the webjobs? |
We have this fixed already for web apps, as they can rely on hostname header. For webjobs, there is no request or header, so not sure how to fix it there. So its unfixed for WebJobs and there are no clear guidance on how to fix it as well. (We can close this and open a new issue just to track this for webjobs) |
Maybe using the newly announced Event Grid events the environment variable can be updated, it might solve the issue as defined in this Issue:
|
Looks promising. One of the thing we are trying to avoid is SDKs having deep knowledge about all the Azure platforms - and instead have all Azure environments expose the information is a standardized way, so SDKs don't have to have specialized solution for each compute platform. (There was not enough bandwidth to pursue this, so I expect this issue to be unresolved for short-term) |
|
@Expecho If you use the EventGrid approach to solve you issue, please post back the approach/sample code, so other customers can leverage it, until SDK itself gets this capability (which will take some time) |
To be honest, we do not use webjobs so that part is not affecting us. So I won't probably use the EventGrid approach myself but it could be interesting for future readers of this issue. If we do have the need we will post a sample. |
|
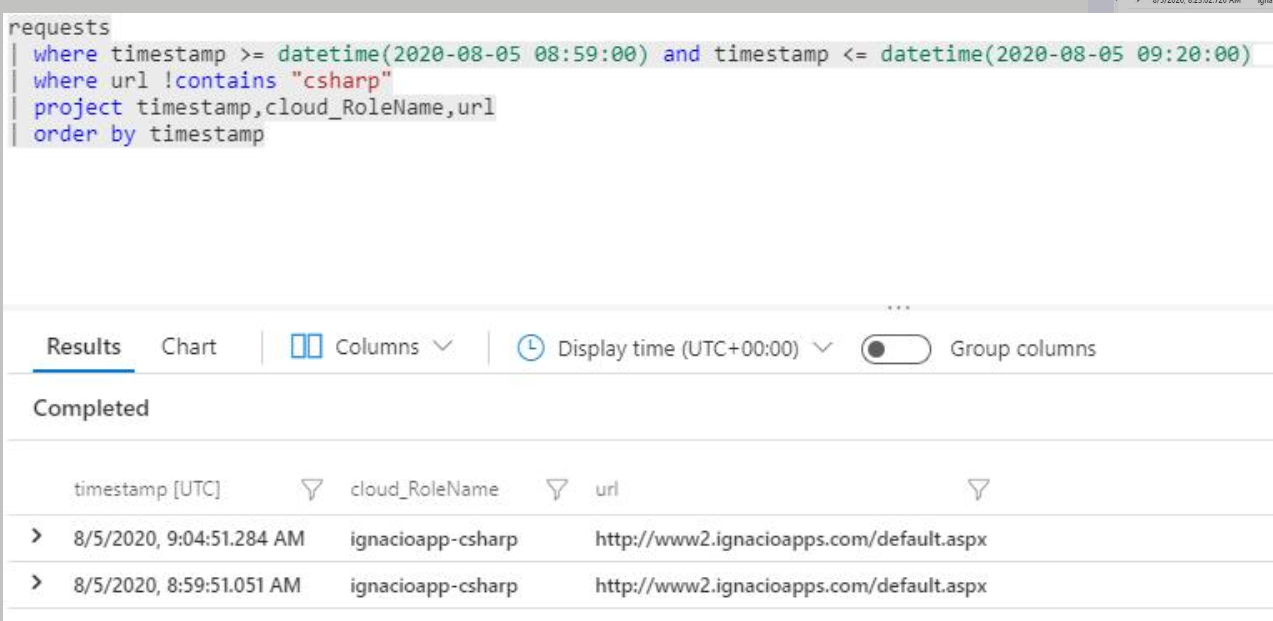
Hi all. I was wondering if this issue was actually resolved for App Services. Let me explain my situation: I have two slots, the production and another called csharp in my App Service called ignacio app. I have Agent Based App Insights so it is running these versions: When I run this query the following happens: So as you can see, the URL remains the same (www2.ignacioapps.com) but the Cloud role name changed. I restarted the App Service (which is also implicitly done by the swap). Can you guys confirm this is the expected behaviour? I see in previous comments that the issue was fixed for webapps, but it seems that the Agent based App Insights client is old. In which version exactly the issue has been fixed? |
|
Its fixed in 2.12 version of the SDK. |
|
Hi Cijo,
I am actually using Asp.NET in Agent Based. It seems that I am using 2.8.6.
Regards,
Ignacio Alvarez Arenas
AZURE CLOUD ENGINEER
Azure CXP
+353 (1) 2797590
igalvare@microsoft.com<mailto:igalvare@microsoft.com>
[Microsoft]
From: Cijo Thomas <notifications@github.com>
Sent: Wednesday 12 August 2020 15:23
To: microsoft/ApplicationInsights-dotnet <ApplicationInsights-dotnet@noreply.github.com>
Cc: Ignacio Alvarez Arenas <igalvare@microsoft.com>; Comment <comment@noreply.github.com>
Subject: Re: [microsoft/ApplicationInsights-dotnet] Use WAS-DEFAULT-HOSTNAME HttpHeader to get slot name (#1368)
Its fixed in 2.12 version of the SDK.
Are you using Asp.Net or Asp.Net Core in agent based enablement?
—
You are receiving this because you commented.
Reply to this email directly, view it on GitHub<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FApplicationInsights-dotnet%2Fissues%2F1368%23issuecomment-672902358&data=02%7C01%7Cigalvare%40microsoft.com%7C90ece4982f8040ee794e08d83ecb438e%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637328390024715697&sdata=PExEOqiJvNKD1Tt7Z3Q024RWByglBSg%2FII%2BNM9lVGkI%3D&reserved=0>, or unsubscribe<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fnotifications%2Funsubscribe-auth%2FAOVGDHDA6PLNMRC5XMQEWZDSAKQVRANCNFSM4JVQCVDA&data=02%7C01%7Cigalvare%40microsoft.com%7C90ece4982f8040ee794e08d83ecb438e%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637328390024725694&sdata=o7cfUyZGqrMUitG4v%2Bu1Pkg40mtVW95N%2FOWlRjfwGqE%3D&reserved=0>.
|
|
@IgnacioAlvarezArenas Asp.Net agent is on an old version of SDK. You need to use SDK based approach to benefit from this. |
|
Asp.Net Core agent is somewhat new. I don't know exact version, but I think its newer than 2.12 so you will be fine in Asp.Net core. |
|
Thanks for the clarification Cijo, really helpful! |


Issue
Currently we use the WEBSITE_HOSTNAME to determine the App Service slot the code is deployed to.
This environment variable is passed in upon process creation by the App Service sandbox and is not updated. This requires a reboot of the App Service to get the correct value.
Result
The result of this is telemetry will have an incorrect
cloud_RoleNameuntil this happens which can skew customer metrics.Proposal
The proposed fix is to read the
WAS-DEFAULT-HOSTNAMEhttp header instead which is sent by the App Service front end (ARR) servers and will always have the correct app service host name.The text was updated successfully, but these errors were encountered: