-
Notifications
You must be signed in to change notification settings - Fork 30
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Inquiring about SecureBIO's Test Vector Certificate #22
Comments
|
Are you setting the IntermediateCA1 and IntermediateCA2 parameters to the test CA certs as well? The test certs should chain up to Microsoft ECC Root Certificate Authority 2017. We're still using these certs for internal testing without issue. We don't have bioiso event logs. If you use feedback hub to take a recording under "Security & Privacy/Windows Hello Fingerprint", and share the feedback ID, we can look at the traces. |
|
Thank you for reply this thread. If an incorrect certificate is inserted, an error code is E_INVALIDARG (0x80070057) and I sent feedback via feedback hub. ( https://aka.ms/AA9bn4s ) |
|
Thanks for filing that. That helped narrow things down a bit. I was able to confirm it doesn't have to do with the expiration, and I see the same details viewing the certificate on my machine (where our tests pass with an these certs). There's a few possibilities for why this code can be returned that I'll have to ask some team members about. Given that we haven't seen issues with these certificates though, I think there could be some formatting issues with the secure connection buffer. Can you dump a buffer so we can check the contents? |
|
The certs from the logging don't match the test certs from the wiki exactly. Which certs do the sizes in these logs refer to? The first set of sizes is correct, but the second set matches the incorrect certs. Model Cert:
CA1 Cert:
CA 2 Cert:
|
|
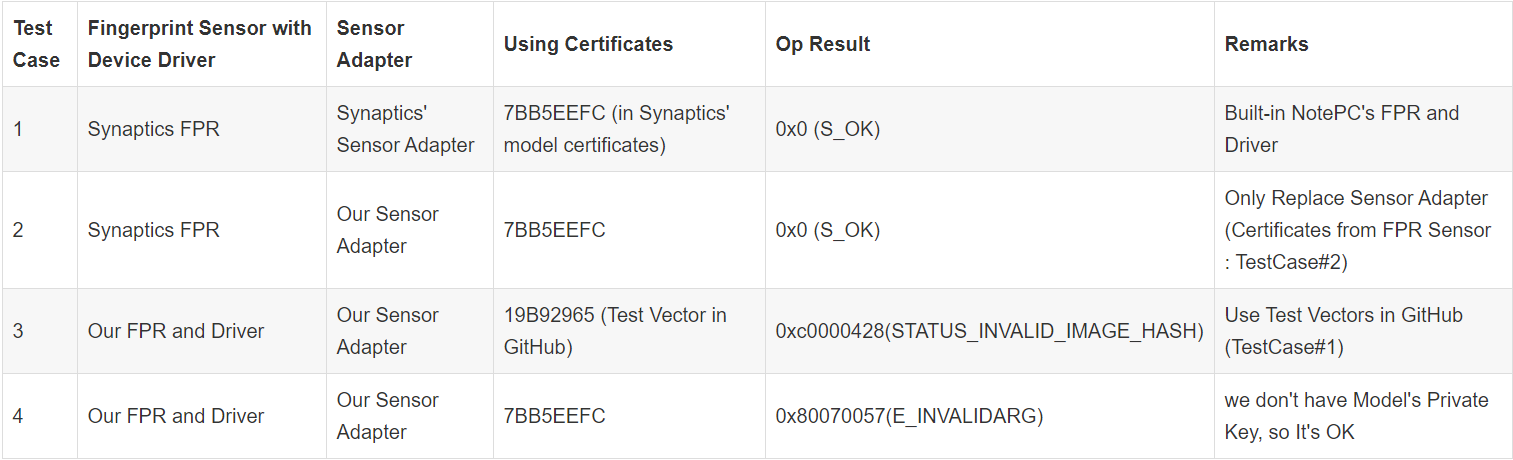
Sorry, There seems to be a problem with the attached previous log. Also, the log cases I included last time are as follows. Case 1. Our driver using Test Vector (SDCP_ConnectSecure_Log.txt)
Case 2. The built-in driver (commercial driver) for the notebook replaces and using our SensorAdapter,
|
|
Hello, I tested under the following environments. Test Steps:
In addition, even if Device Driver and IOCTL are not handled, it is possible to check if Secure Connection is properly established in Event Viewer by inserting only SDCP Test Code and Certificate in SensorAdapterConnectSecure function of SensorAdapter. I’d appreciate it if you could check what certificate is valid, again. |
|
Hello As a result of verifying the certificates and functions since the last answer, After fixing the problem of our device, when we put the values of the test vector, but, When I change the Test Vector to the actual value(h_r, h_pk, pk_f, sk_f) it still doesn't work. 0x8007001f
I attached host and device logs and Screenshot of Event Viewer. and In sdcpcli_hash_claim, it is supposed to put the actual certificate instead of g_model_pub_key. Always Thank you for everything. |
|
Glad to see we fixed the certificate issue. For sdcpcli_hash_claim, you should use the whole model cert instead of the public key. The ERROR_GEN_FAILURE isn't coming from the bio code, so I'd need to look at logs again to get a clue. Let's try using the model cert in sdcpcli_hash_claim to see if that resolves the error. If not, take feedback again and I can try to narrow down where the error is coming from. |
|
Hello, and I tested three methods like below,
It occured some discrepancy though I thought there wouldn't no problem with the function because the test vector were same. Additional Information about testing Synaptics Driver.
*Those were not same between the code of Github and the mac value from Synaptics Driver with using a fixed Host Public Key (and private Key) & Random value The test code used on below and the log output from the Synaptics FP sensor are attatched like below. Synaptics_log.txt Best Regards. |
|
I think the problem is in the master key generation in the example code. We should be using the host public key, and firmware private key instead of the other way around. Let me see if I can dig up that private key, since I don't see it in the example code. |
|
Hello, Synaptics TestCode Example was not processed on the code of device but just on code of Host. Because the value from Device(Synaptics FP Sensor) is only s_m, s_d, cert_m, r_d, pk_f, pk_d, h_f, I cannot know the private key of firmware. Q1. When I excute s_m, s_d, cert_m, r_d, pk_f, pk_d, h_f calculated from Synaptics FP Sensor on GitHub's code, So would you please to confirm how the MAC value is put out with the attached log value? In this case, It seems this problem derived from an error or omission at the calculation of master secret or Claim Hash :H(c) on GitHub's code. Q2. Why is the error code 0x8007001F come out though I implemented the driver of Github (cert_m of Test Vector) Q3. Additionally would you let me know how to get the Real Certificate (with Certificate's Private Key) applied on our FP sensor? Thank you. |
|
Would you have any idea about this matter? |
|
Sorry to get back late, I've had a really busy week.
|
|
Hello,
As you know it is possible to operate a driver corrected with non-signed if the Windows Test Mode (bcdedit /set TESTSIGNING ON) is activated. What we can recognize from those values is just the Device Random(r_d), Claim (cert_m, pk_d, pk_f, h_f, s_m, s_d), Mac, Thus what I am just guessing is whether the formula of calculating Claim Hash or generating Master Secret through the Key Agreement is wrong or not.(Please see green) We cannot calculate the Key Agreement(Master Secret) because the Host Random and the Host Public is transferred from Bio Trustlet on the original Windows Biometrics routine.
I need your help about how to get an efficient way to the log.
It just means about the certificate of our commercial FP Sensor. |
|
Agreed, it's likely a discrepancy in one or more of those factors. I can run those values through our test code to see, but I probably won't be able to get to it for a bit. For the logs, just take a recording through feedback hub again (use feedback hub to take a recording under "Security & Privacy/Windows Hello Fingerprint", and share the feedback ID, we can look at the traces) I'll have to engage with my PMs for getting that cert. Are you on the Microsoft partner portal? If so, we can open a work item to track that. |
|
Hello.
Thanks to your hospitality, I will look forward to waiting your reply.
Reuploaded once again through the feedback hub.
Yes we are already registered on the Microsoft Partner Portal. |
|
Sorry for the confusion. Yes, please open a feedback. If should give you an ID number we can find it by. |
|
You're welcome. |
|
Would you share any update? |
|
We got the collaborate item and it's assigned to the correct people. As for testing, I haven't had a chance. Earliest I would be able to would be the week after next. |


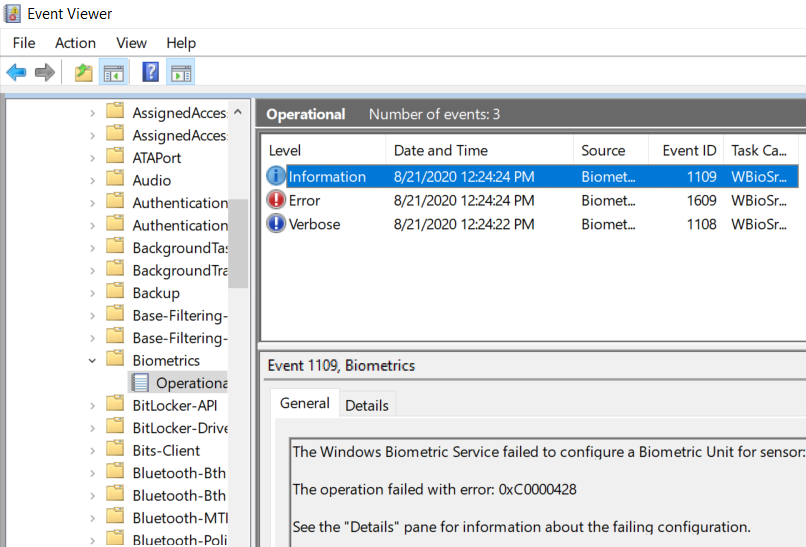








While developing the SecureBIO Driver by referring to SecureDeviceConnectionProtocol on GitHub,
I'm sending you an email with any questions about the Test Vector you have posted on GitHub.
Here is our status of developing Fingerprint Driver with SecureBiometrics.
When our sensor and driver are connected to the T14s, the creation of the Biometric Unit is normal, but the following error is displayed in the Event Viewer at the actual ConnectSecure stage and does not work.
"The Windows Biometric Service secure component failed to establish a secure connection with sensor. Error Code : 0xc0000428"
https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-erref/596a1078-e883-4972-9bbc-49e60bebca55
0xc0000428 STATUS_INVALID_IMAGE_HASH : The hash for image %hs cannot be found in the system catalogs. The image is likely corrupt or the victim of tampering.
Q1. Can I use the Test Vector (Certificate / Secret Key) on GitHub for development?
When checked in Event Viewer, the certificate is displayed as invalid.
Also, if TestVector has expired, I would like to get a new TestVector Certificate and Private Key.
Q2. Is there a way to check the Event Log related to BioISO (Bio Trustlet)?
Q3. If possible, I would like to know the contact point for SDCP development.
The text was updated successfully, but these errors were encountered: