在《How to disable conntrack protocol parsing in the linux kernel?》中有
There are a few ways to set module parameters, both temporary and persistent.
- Persistent changes
The change will take effect as soon as the module is loaded, whether it is done manually or automatically at boot. If the module is already loaded, you must either reboot, or unload it and load it, which may or may not be possible if it has unremovable dependencies. To do this, create a file, such as
/etc/modprobe.d/no_conntrack_helper.conf, with the following contents:options nf_conntrack nf_conntrack_helper=0
- Temporary changes (
modprobe)This requires the module be unloaded before you run the command. The changes will disappear when the module is unloaded or when the system reboots. You can change specific parameters by passing them as arguments to the
modprobeutility when loading the module. Load the module as root:modprobe nf_conntrack nf_conntrack_helper=0
- Temporary changes (
sysfs)Some modules can have their parameters modified even after the module has been loaded. This can be done by writing to a special file in
sysfs. I do not know if the specific parameter you want to change can be modified at runtime, but if it is, you would want to run the following command as root:echo 0 > /sys/module/nf_conntrack/parameters/nf_conntrack_helper
在 ubuntu 上为 /proc/sys/net/netfilter/nf_conntrack_helper ;
在《Secure use of iptables and connection tracking helpers》中有
Disable helper by default
- Principle
Once a helper is loaded, it will treat packets for a given port and all IP addresses. As explained before, this is not optimal and is even a security risk. A better solution is to load the module helper and deactivate their parsing by default. Each helper we need to use is then set by using a call to the CT target.
- Method
Since Linux 3.5, it is possible to desactivate the automatic conntrack helper assignment. This can be done when loading the
nf_conntrackmodulemodprobe nf_conntrack nf_conntrack_helper=0This can also be done after the module is loading by using a
/procentryecho 0 > /proc/sys/net/netfilter/nf_conntrack_helperPlease note that flows that already got a helper will keep using it even if automatic helper assignment has been disabled.
在《How can I disable connection tracking (conntrack) in IPTables?》中有(2014年6月27日,有点过时)
环境
Red hat Enterprise Linux (RHEL)
问题
- The system is dropping packets due to the nf_conntrack table being filled.
- It is not necessary to perform NAT on this system.
- How can conntrack be disabled?
决议
IPTables provides a special target, NOTRACK, which is part of the raw table:
raw:
This table is used mainly for configuring exemptions from connection tracking in combination with the NOTRACK target. It registers at the netfilter hooks with higher priority and is thus called before ip_conntrack, or any other IP tables. It provides the following built-in chains: PREROUTING (for packets arriving via any network interface) OUTPUT (for packets generated by local processes)
This makes it possible to disable connection tracking for connections matching a specific criteria. Taking as an example a very busy DNS server/s (such as a tier-1 ISP DNS infrastructure), the following procedure will disable connection tracking for all DNS connections made to/from the system:
- Add NOTRACK rules in the
rawtable for both TCP and UDP, port 53, incoming and outgoing (since DNS servers can work as recursive and query other DNS servers on behalf of clients).iptables -t raw -A PREROUTING -p tcp --dport 53 -j NOTRACK iptables -t raw -A PREROUTING -p udp --dport 53 -j NOTRACK iptables -t raw -A PREROUTING -p tcp --sport 53 -j NOTRACK iptables -t raw -A PREROUTING -p udp --sport 53 -j NOTRACK iptables -t raw -A OUTPUT -p tcp --sport 53 -j NOTRACK iptables -t raw -A OUTPUT -p udp --sport 53 -j NOTRACK iptables -t raw -A OUTPUT -p tcp --dport 53 -j NOTRACK iptables -t raw -A OUTPUT -p udp --dport 53 -j NOTRACK
- Save the new IPTables rules, to make them persistent:
service iptables save
- Restart IPTables to confirm the rules are in place. Note that the raw table must be specified since by default the filter table is shown.
service iptables restart iptables -L -t raw
- Once this has been done, there are two ways to test this. Either monitor the following files:
watch -n1 cat /proc/sys/net/ipv4/netfilter/ip_conntrack_count watch -n1 cat /proc/net/ip_conntrack
- Or monitor the current rules in the raw table, showing the amount of packets matched by each rule:
iptables -nvL -t raw
- Perform connections again and see if either conntrack does not rise or packets are matched in the NOTRACK rules.
根源
It is not possible to disable conntrack globally, as IPTables is tightly coupled with it. Instead, conntrack must be disabled for specific connections based on normal IPTables rule processing (e.g. address, port, protocol, etc).
- "ip_conntrack: table full, dropping packet." seen in
/var/log/messagesmeans that Packet drops on this system for connections usingip_conntrackornf_conntrack.- To change the default value of
ip_conntrack_max, modify the default value for hashsize.- The default
ip_conntrack_maxwill become 8 times for RHEL5.- the default
nf_conntrack_maxwill be 4 times for RHEL6/7.- The
ip_conntrackmodule uses a portion of the system memory to track connections called a connection tracking table. The size of this table is set when theip_conntrackmodule is loaded, and is usually determined automatically by a hash of the installed system RAM.- To check the number of packets dropped on each CPU by conntrack overflowing, check
/proc/net/stat/nf_conntrackstatearly_drop.
在《nf_conntrack 超限问题》中有
注意:
- nf_conntrack 跟 NAT 有关,用来跟踪连接条目;
- 任何调用 iptables NAT 功能的操作都会触发 nf_conntrack 模块被 load ;
执行如下命令
root@ip-172-31-6-140:~# iptables -L -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
root@ip-172-31-6-140:~#
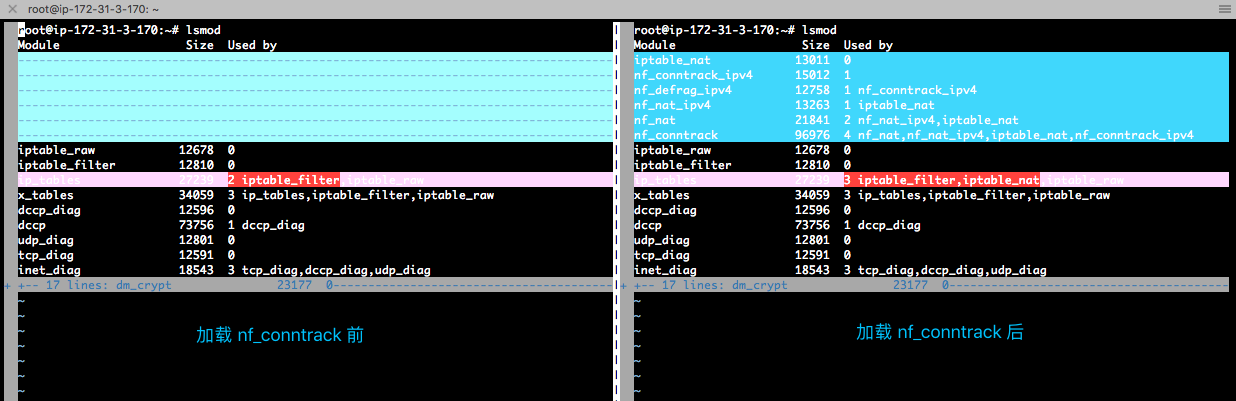
会导致 nat 功能被启用,之后会自动加载 NAT 相关内核模块
同时会出现如下内核参数
root@ip-172-31-6-140:~# sysctl -a|grep conn
net.core.somaxconn = 128
net.netfilter.nf_conntrack_acct = 0
net.netfilter.nf_conntrack_buckets = 16384
net.netfilter.nf_conntrack_checksum = 1
net.netfilter.nf_conntrack_count = 12289
net.netfilter.nf_conntrack_events = 1
net.netfilter.nf_conntrack_events_retry_timeout = 15
net.netfilter.nf_conntrack_expect_max = 256
net.netfilter.nf_conntrack_generic_timeout = 600
net.netfilter.nf_conntrack_helper = 1
net.netfilter.nf_conntrack_icmp_timeout = 30
net.netfilter.nf_conntrack_log_invalid = 0
net.netfilter.nf_conntrack_max = 65536
net.netfilter.nf_conntrack_tcp_be_liberal = 0
net.netfilter.nf_conntrack_tcp_loose = 1
net.netfilter.nf_conntrack_tcp_max_retrans = 3
net.netfilter.nf_conntrack_tcp_timeout_close = 10
net.netfilter.nf_conntrack_tcp_timeout_close_wait = 60
net.netfilter.nf_conntrack_tcp_timeout_established = 432000
net.netfilter.nf_conntrack_tcp_timeout_fin_wait = 120
net.netfilter.nf_conntrack_tcp_timeout_last_ack = 30
net.netfilter.nf_conntrack_tcp_timeout_max_retrans = 300
net.netfilter.nf_conntrack_tcp_timeout_syn_recv = 60
net.netfilter.nf_conntrack_tcp_timeout_syn_sent = 120
net.netfilter.nf_conntrack_tcp_timeout_time_wait = 120
net.netfilter.nf_conntrack_tcp_timeout_unacknowledged = 300
net.netfilter.nf_conntrack_timestamp = 0
net.netfilter.nf_conntrack_udp_timeout = 30
net.netfilter.nf_conntrack_udp_timeout_stream = 180
net.nf_conntrack_max = 65536
root@ip-172-31-6-140:~#
移除上述自动加载的内核模块的命令
modprobe -r iptable_nat nf_nat_ipv4 nf_conntrack_ipv4 nf_defrag_ipv4 nf_nat nf_conntrack
移除前后对比图