Building AWS Infrastructure with Infrastructure as Code (Terraform) 🚀
- AWS IAM User and policies attached - Refer: click here
- AWS CLI installed and configured - Refer: click here
After completion of the configuration continue on code editor with terraform.
Tasks:
Basic structure:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.16"
}
}
required_version = ">= 1.2.0"
}
provider "aws" {
region = "us-east-1"
}
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "main"
}
}
aws_vpc will create a VPC with specified cidr block and with tag name as main.
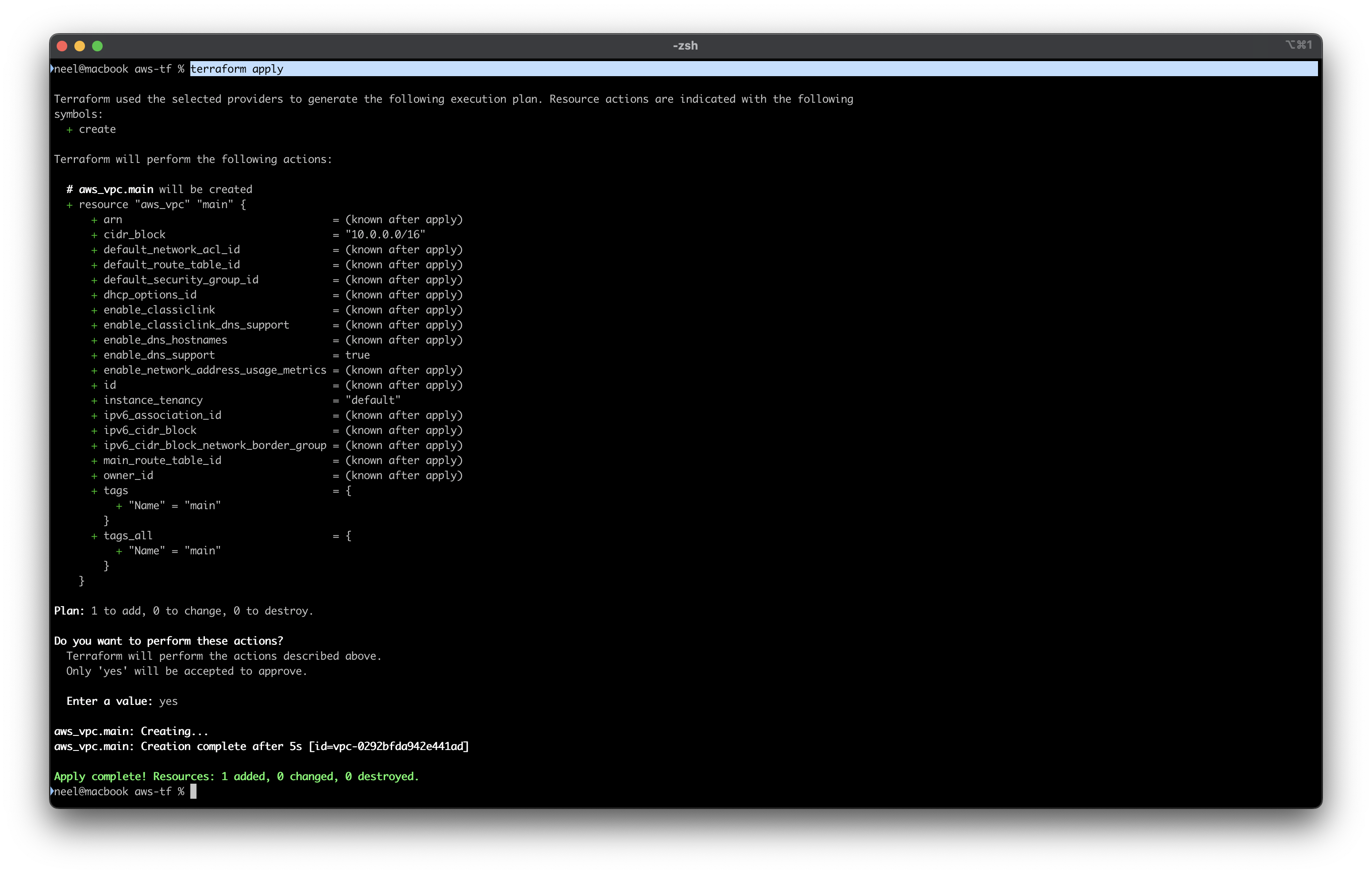
Run terraform init and then terraform apply then verify the creation of VPC in cosole.
The VPC with name main has been created!
Write below code to create aws subnet in the vpc that we just created.
resource "aws_subnet" "public_subnet" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.1.0/24"
tags = {
Name = "Public Subnet"
}
}
After adding code, run terraform apply and verify subnet in cosole.
Check "Public Subnet" is created successfully.
Write below code to create aws subnet in the vpc that we just created.
resource "aws_subnet" "Private_subnet" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.2.0/24"
tags = {
Name = "Private Subnet"
}
}
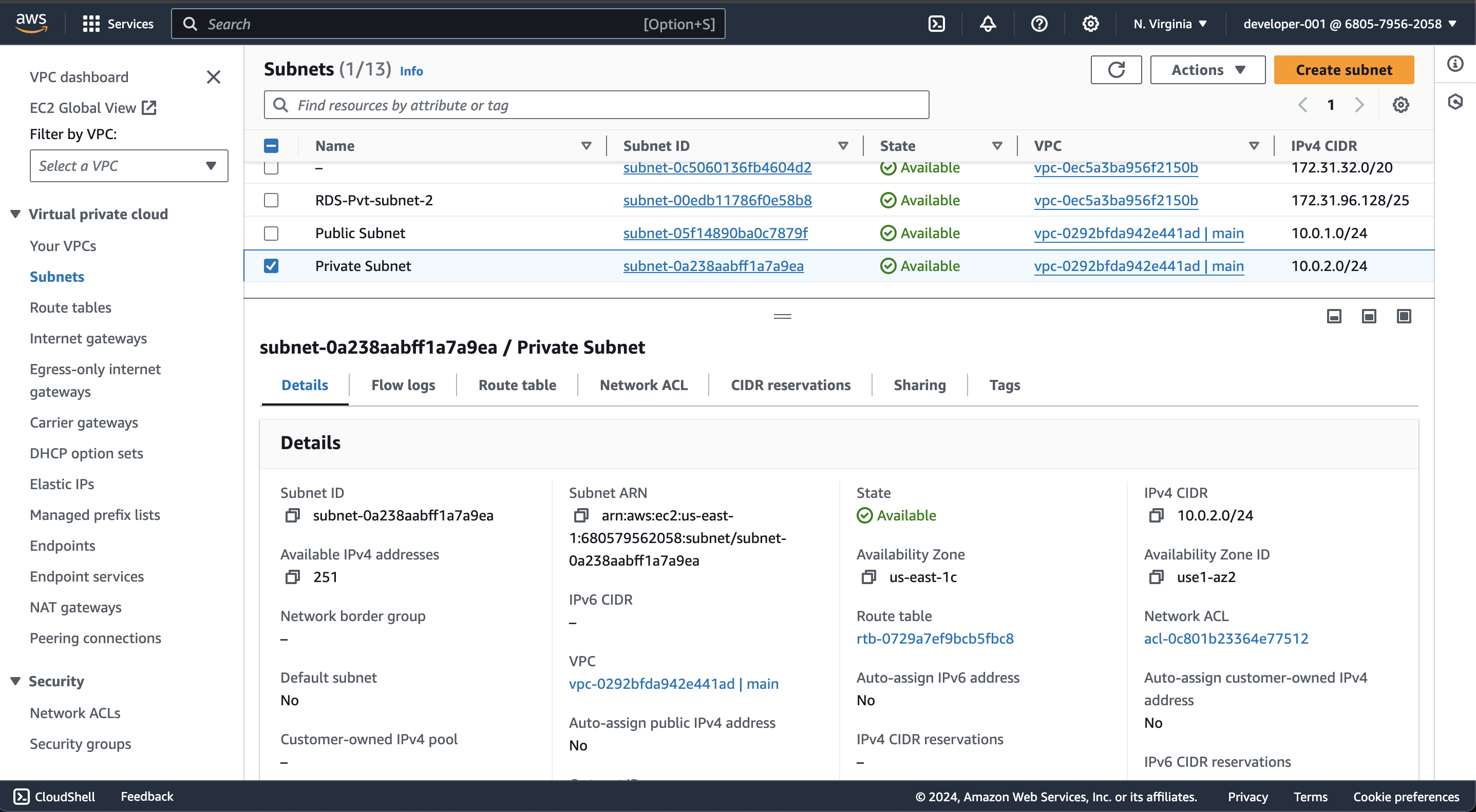
After adding code, run terraform apply and verify subnet in cosole.
Check "Private Subnet" is created successfully.
resource "aws_internet_gateway" "igw" {
vpc_id = aws_vpc.main.id
tags = {
"Name" = "Internet GateWay"
}
}
aws_internet_gateway will create an internet gateway and will be under VPC main as vpc_id has been assigned of main VPC.
After adding code, run terraform apply and verify internet gateway in cosole.
5: Create a route table for the public subnet and associate it with the public subnet. This route table should have a route to the Internet Gateway.
Create a route table for public subnet
resource "aws_route_table" "public" {
vpc_id = aws_vpc.main.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw.id
}
tags = {
Name = "Route Table"
}
}
aws_route_table will create a table under vpc main. The route will sends all the traffic with specified cidr to the internet gateway.
Then associate route table with public subnet.
resource "aws_route_table_association" "public" {
subnet_id = aws_subnet.public_subnet.id
route_table_id = aws_route_table.public.id
}
aws_route_table_association will associate the route table to the public subnet.
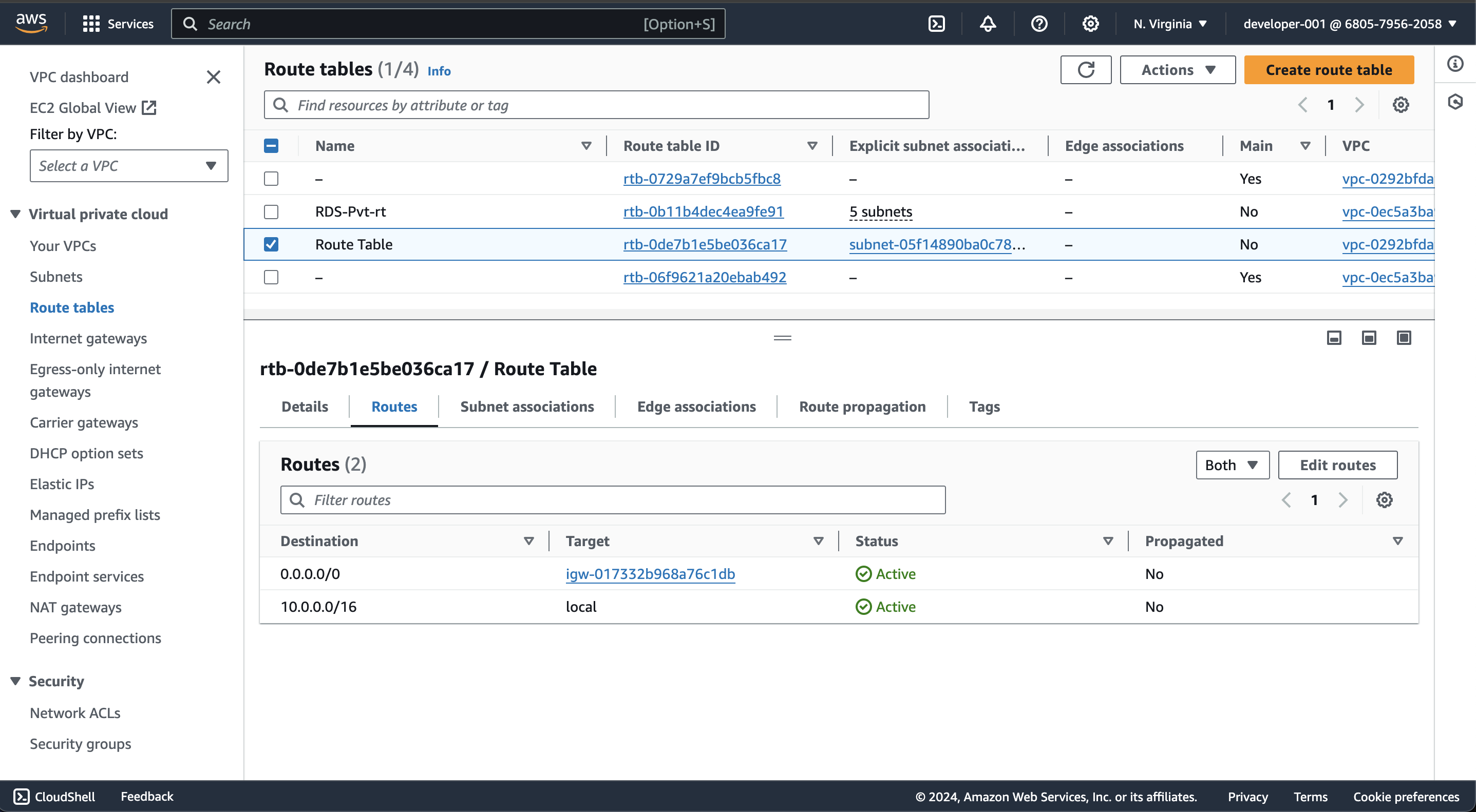
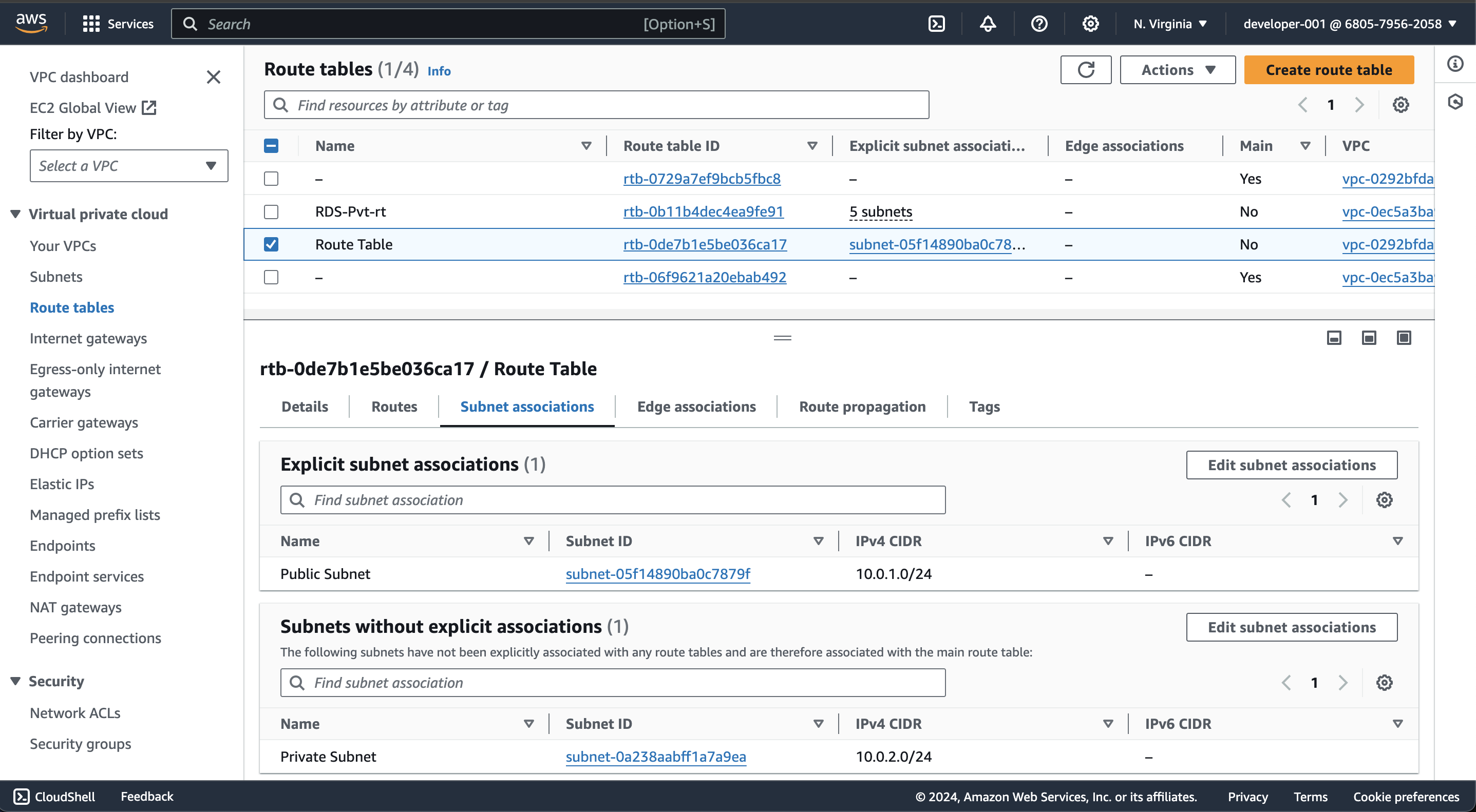
After adding code, run terraform apply and verify route table in cosole.
In Route tables, new route table is successfully created.
Route table routes with internet gateway.
Route table is associated with public subnet using terraform.
- AMI
- Instance type: t2.micro
- Security group: Allow SSH access from anywhere
- User data: Use a shell script to install Apache and host a simple website
- Create an Elastic IP and associate it with the EC2 instance.
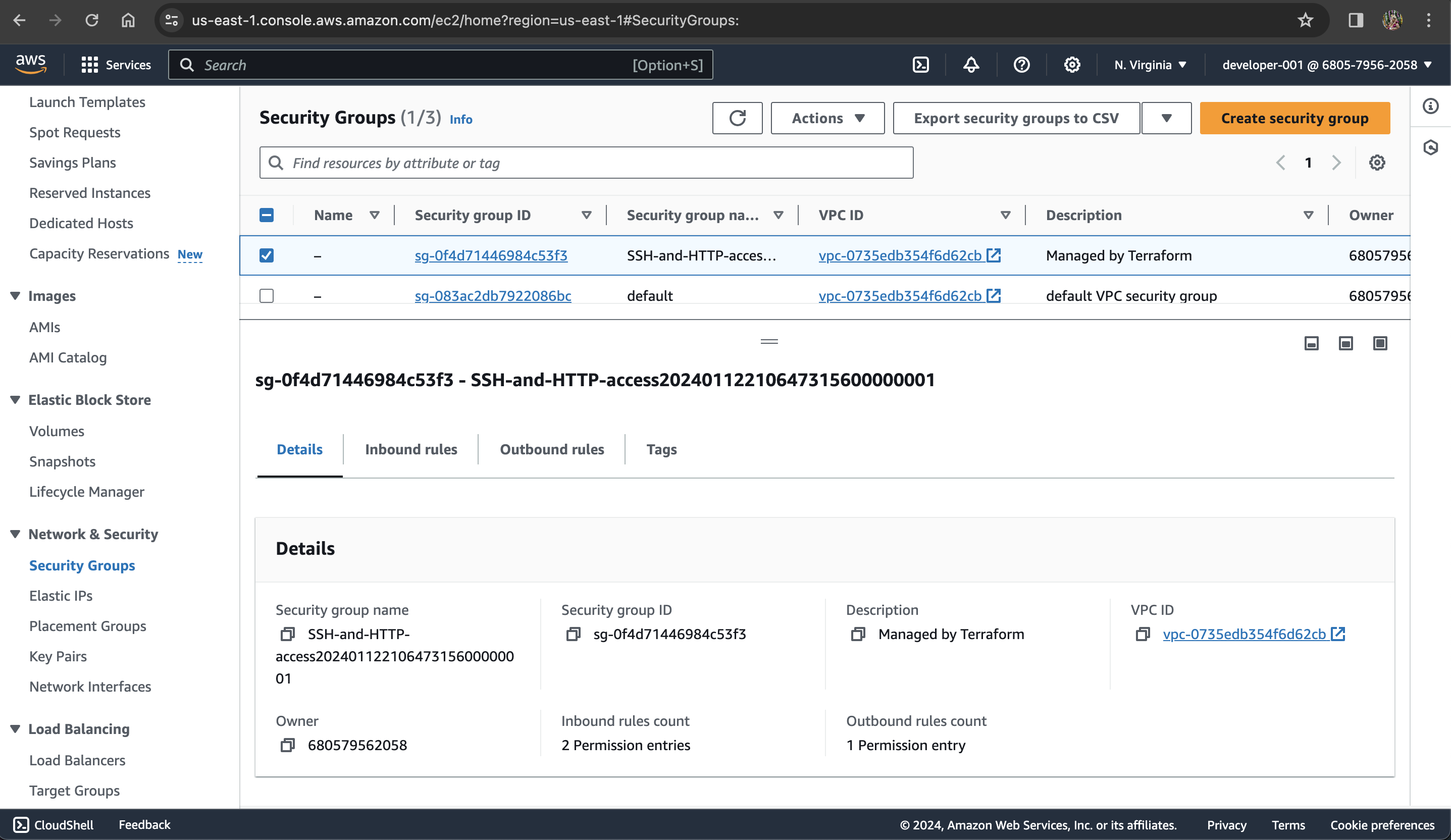
First, create a security group.
resource "aws_security_group" "ssh_access" {
name_prefix = "SSH-and-HTTP-access"
vpc_id = aws_vpc.main.id
ingress {
description = "HTTP"
from_port = 80
to_port = 80
cidr_blocks = ["0.0.0.0/0"]
protocol = "tcp"
}
ingress {
description = "SSH"
from_port = 22
to_port = 22
cidr_blocks = ["0.0.0.0/0"]
protocol = "tcp"
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
Second, EC2 instance.
resource "aws_instance" "web_server" {
ami = "ami-0005e0cfe09cc9050" # Amazon Linux
instance_type = "t2.micro"
key_name = "my-linux-key"
subnet_id = aws_subnet.public_subnet.id
vpc_security_group_ids = [aws_security_group.ssh_access.id]
tags = {
Name = "Web Server"
}
user_data = <<EOF
yum update -y
yum install -y httpd.x86_64
systemctl start httpd.service
systemctl enable httpd.service
echo '<div style="text-align: center;font-family: arial;color: red;"><h1>Welcome to my website <br />New instance created by Neel - Your DevOps Guy</h1></div>' > /var/www/html/index.html
sudo systemctl restart httpd
EOF
}
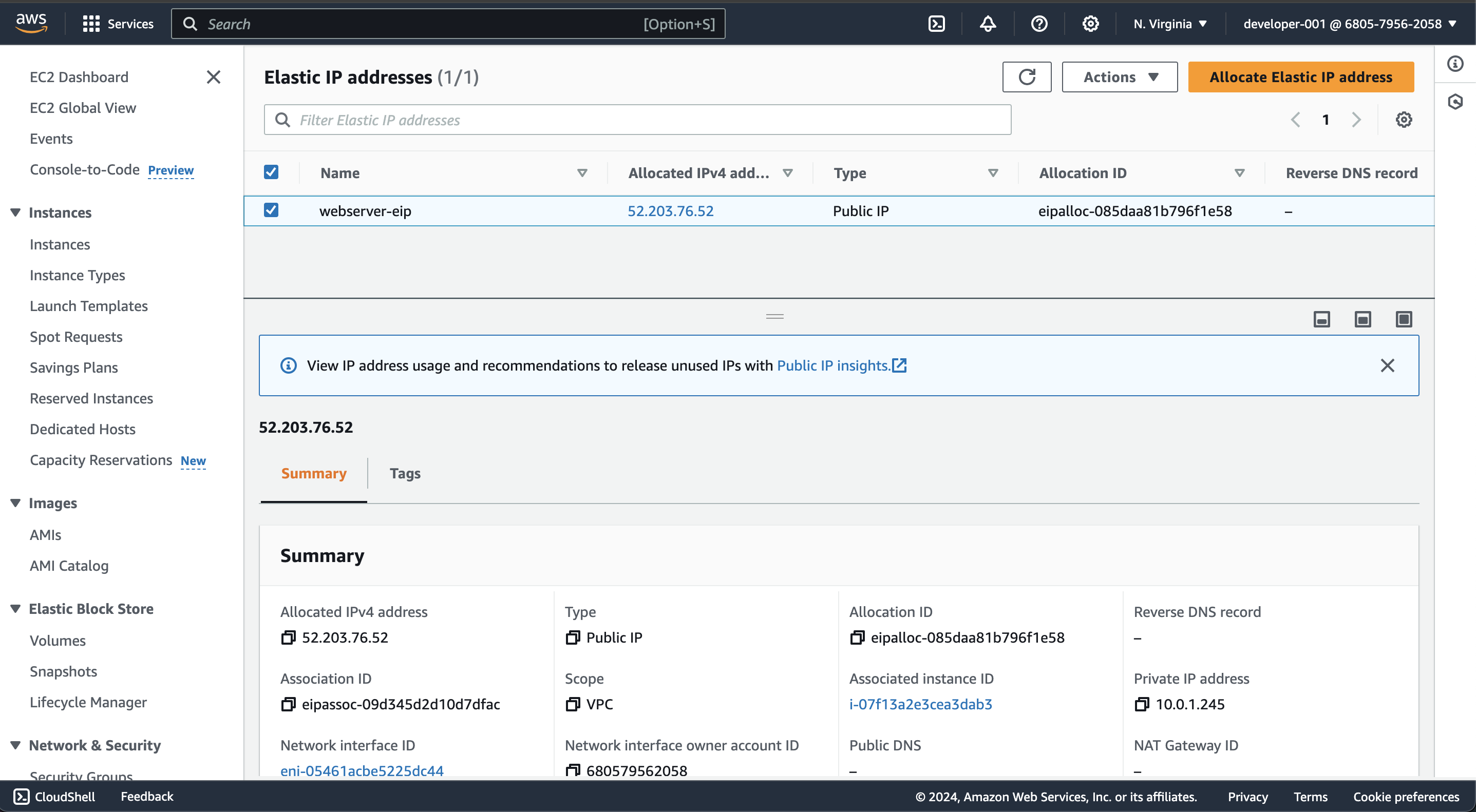
Then create an elastic ip and associat it with instance.
resource "aws_eip" "elastic_ip" {
instance = aws_instance.web_server.id
tags = {
Name = "webserver-eip"
}
}
For displaying IP address of your instance in your CLI, write below code:
output "getIP" {
value = aws_instance.web_server.public_ip
}
After adding code, run terraform apply and verify instance in cosole.
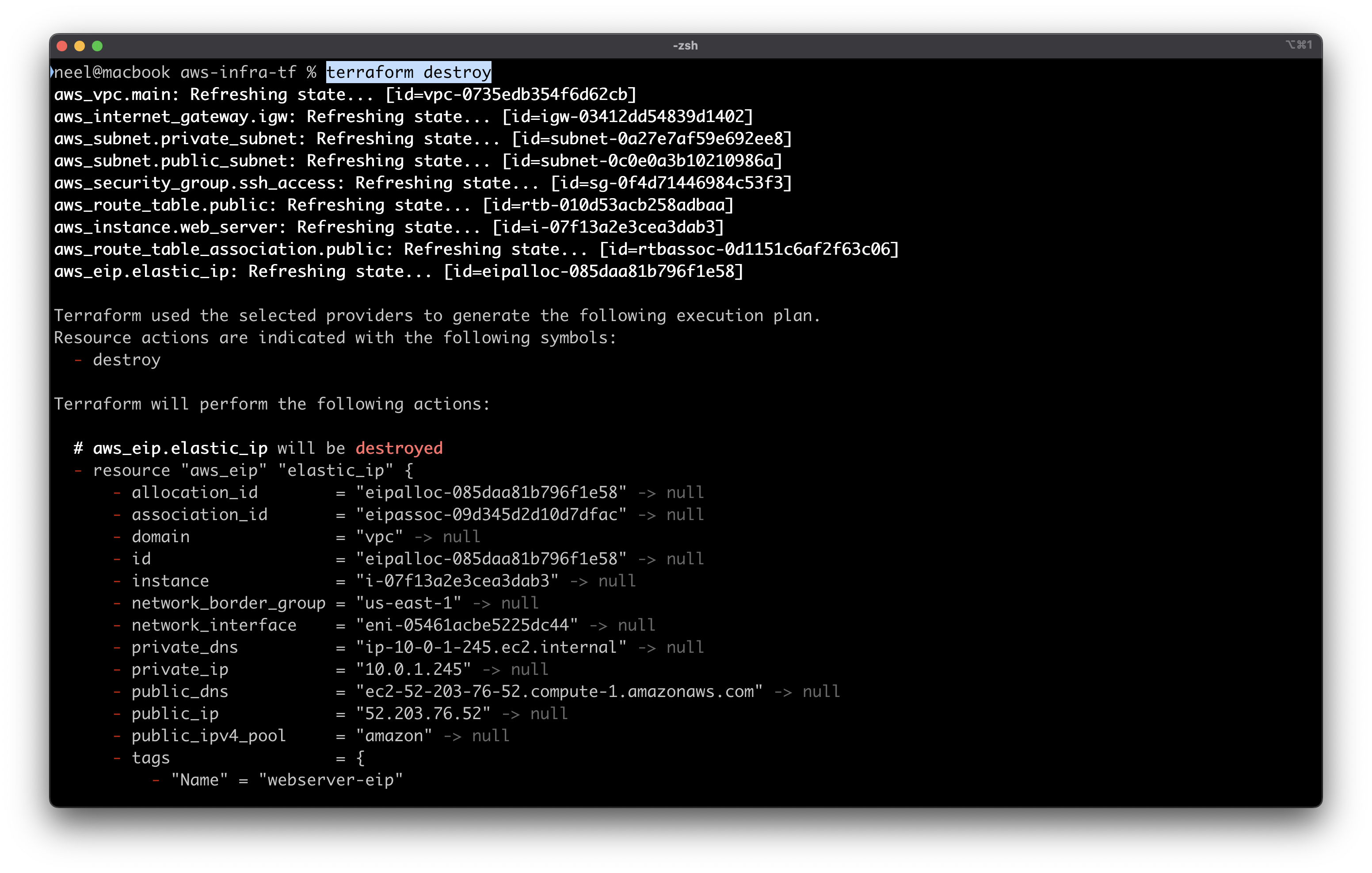
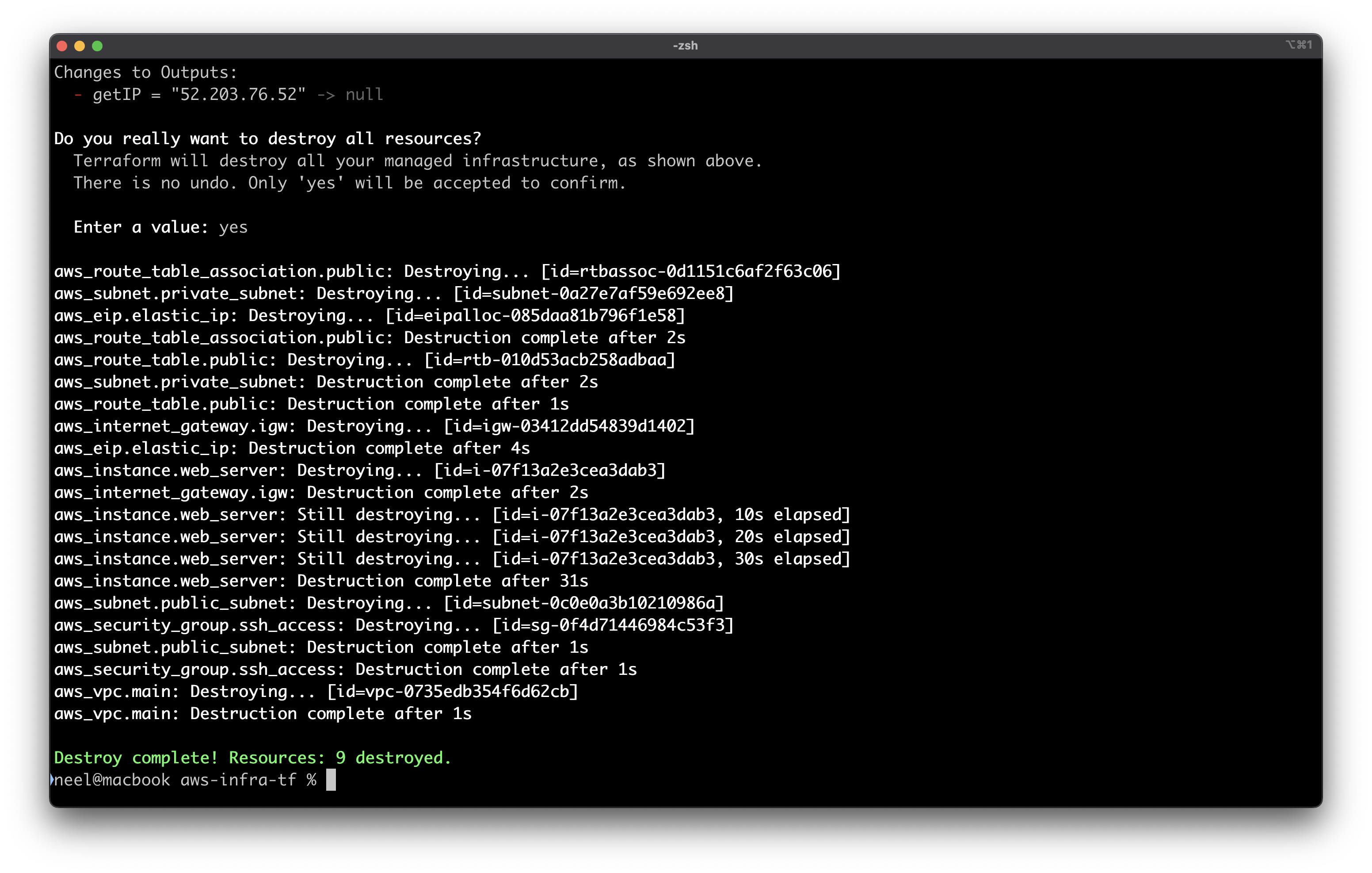
You can delete everything with terraform destroy
Thank you for reading!