You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
I have a root and intermediate CA in CentOS, with OpenSSL 1.0.2k-fips. I also set up a OCSP responder in the intermediate CA, to respond the status of issued certificates. I also have a Windows 2012 R2 server with Remote Desktop Services enabled. I issued a certificate for it using my OpenSSL intermediate CA.
When I use OpenSSL tools to check the status of the certificate, it returns with Response verify OK, certificate good.
$ openssl ocsp -CAfile chain.mydomain.crt.pem -url http://myfqdn-ocsp-responder:8888 -resp_no_certs -issuer int.mydomain.crt.pem -cert server.mydomain.crt.pem
Response verify OK
server.mydomain.crt.pem: good
This Update: Oct 10 16:44:50 2018 GMT
When I use the RDP connection (either the RDP file itself or the RemoteApp webaccess, I get A revocation check could not be performed for the certificate error, although it lets me go through and continue. The Certificate has the OCSP information correctly, though.
But that´s really annoying for the users and I wanted to get rid of this error. In the OCSP responder server I get a couple of Invalid request errors and the log.tx has Responder Error: malformedrequest (1) message.
The OCSP responder was started with: # openssl ocsp -index ../index.txt -port 8888 -rsigner certs/ocspserver.mydomain.crt.pem -rkey private/ocspserver.mydomain.key.pem -CA ../certs/int.mydomain.crt.pem -text -ignore_err -out log.txt&
On the OCSP responder I captured the traffic, and to my surprise it seems OpenSSL and MS RDP check the certificate status in very different ways:
For OpenSSL checking:
OCSP Request is sent, it has inside the hashAlgorithm, issuerNameHash, issuerKeyHash and serialNumber.
It receives back a OCSP Response with responseStatus: successful (0)
Wireshark capture image: request
Wireshark capture image: response
For MS RDP checking:
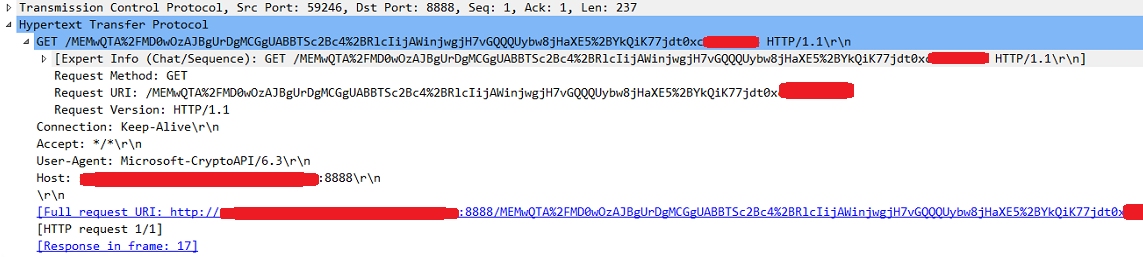
After the regular 3way handshake, the server sends an HTTP GET where the User-Agent is Microsoft-CryptoAPI/6.3 and the Full request URI is http://ocspserver.mydomain:8888/<a bunch of apparently random characters>
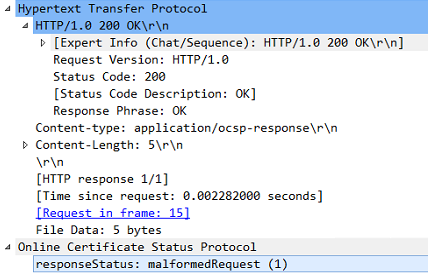
To that the OCSP responds with an OCSP Response packet with responseStatus: malformedRequest (1)
Following that event the server establishes a new 3way handshake, and now sends a OCSP Request, very similar to the one sent by OpenSSL. The OCSP responder responds with a OCSP Response with responseStatus: successful (0). That back and fourth is done 3 times.
Wireshark capture back and fourth image
Wireshark 1st request: server -> OCSP responder (HTTP GET)
Wireshark 1st response: OCSP responder -> server (OCSP)
Wireshark 2nd request: server -> OCSP responder (OCSP)
Wireshark 2nd response: OCSP responder -> server (OCSP)
Apparently the second request by MS RDP, which gets a successful response, is ignored.
Does anyone know why this is happening?
Thank you,
The text was updated successfully, but these errors were encountered:
Here is my scenario:
I have a root and intermediate CA in CentOS, with OpenSSL 1.0.2k-fips. I also set up a OCSP responder in the intermediate CA, to respond the status of issued certificates. I also have a Windows 2012 R2 server with Remote Desktop Services enabled. I issued a certificate for it using my OpenSSL intermediate CA.
When I use OpenSSL tools to check the status of the certificate, it returns with
Response verify OK,certificate good.When I use the RDP connection (either the RDP file itself or the RemoteApp webaccess, I get
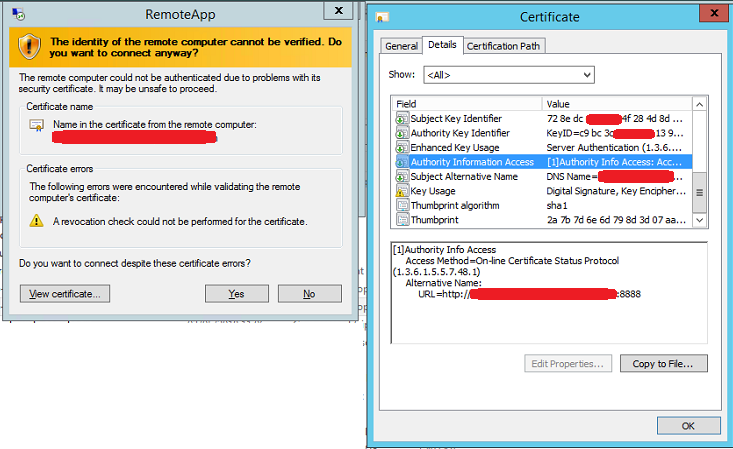
A revocation check could not be performed for the certificateerror, although it lets me go through and continue. The Certificate has the OCSP information correctly, though.But that´s really annoying for the users and I wanted to get rid of this error. In the OCSP responder server I get a couple of
Invalid requesterrors and the log.tx hasResponder Error: malformedrequest (1)message.The OCSP responder was started with:
# openssl ocsp -index ../index.txt -port 8888 -rsigner certs/ocspserver.mydomain.crt.pem -rkey private/ocspserver.mydomain.key.pem -CA ../certs/int.mydomain.crt.pem -text -ignore_err -out log.txt&On the OCSP responder I captured the traffic, and to my surprise it seems OpenSSL and MS RDP check the certificate status in very different ways:
For OpenSSL checking:

OCSP Request is sent, it has inside the
hashAlgorithm,issuerNameHash,issuerKeyHashandserialNumber.It receives back a OCSP Response with
responseStatus: successful (0)Wireshark capture image: request
Wireshark capture image: response

For MS RDP checking:
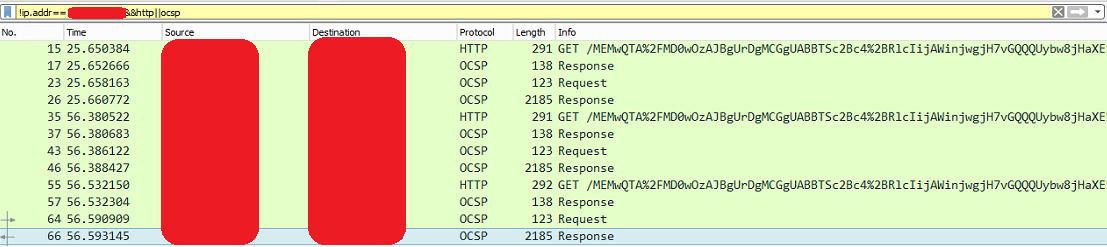
After the regular 3way handshake, the server sends an HTTP GET where the
User-AgentisMicrosoft-CryptoAPI/6.3and the Full request URI ishttp://ocspserver.mydomain:8888/<a bunch of apparently random characters>To that the OCSP responds with an OCSP Response packet with
responseStatus: malformedRequest (1)Following that event the server establishes a new 3way handshake, and now sends a OCSP Request, very similar to the one sent by OpenSSL. The OCSP responder responds with a OCSP Response with
responseStatus: successful (0). That back and fourth is done 3 times.Wireshark capture back and fourth image
Wireshark 1st request: server -> OCSP responder (HTTP GET)
Wireshark 1st response: OCSP responder -> server (OCSP)
Wireshark 2nd request: server -> OCSP responder (OCSP)
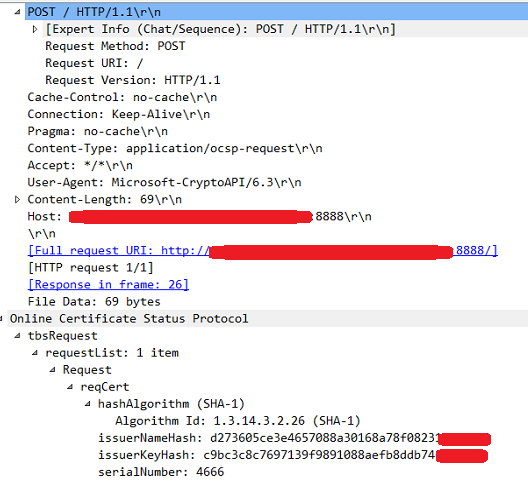
Wireshark 2nd response: OCSP responder -> server (OCSP)

Apparently the second request by MS RDP, which gets a successful response, is ignored.
Does anyone know why this is happening?
Thank you,
The text was updated successfully, but these errors were encountered: