-
-
Notifications
You must be signed in to change notification settings - Fork 877
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Ver:2.0.30 Net/SSH2.php _get_binary_packet() and _filter() call each other recursively. #1644
Comments
|
Sorry about the delay - I'm not sure how this slipped past my radar. Anyway, can you post the SSH logs? You can get them by doing Thanks! |
|
please find the log. i have to remove some areas as the log contained file data I suppose. |
|
I'm not seeing a whole lot in those log that I can do anything with. A few things I'm wondering:
You can enable logging in PuTTY by going to putty.exe, selecting the Logging category and checking "SSH packets". Then go back to the Session category, type in a session name (say phpseclib) under "Saved Sessions" and hit the Save button. Once that's done, go to a command prompt and type in the following: That said, here is the result of my analysis of your logs:
That's when the server starts sending a bunch of NET_SSH2_MSG_IGNORE packets and then the server tries to initiate a key re-exchange. Normally, the logs would have the SSH identifier in them but either you manually cut it out or else the logs were so big that that part of them was removed to clear up space for newer packets. |
|
Does terrafrost@992a6f2 / https://github.com/terrafrost/phpseclib/commits/3.0-kex-fix fix the issue for you? |
|
Are you using the branch or did you manually apply the changes to 3.0.8? I ask because the line numbers aren't lining up with the branch. Like line 1616 doesn't throw an exception: Also, what can often be more helpful be more are the SSH logs, which you can get by doing The problem with stack traces is that they don't tell me too much about what packets were sent before or after. I mean, they're good to have, but it's also good to have the SSH logs as well. Thanks! |
|
Also, what does That's relevant because some SSH servers can have bugs. eg. https://the.earth.li/~sgtatham/putty/0.75/htmldoc/Chapter4.html#S4.26.2 I suspect that bug isn't relevant in your case but there could still be other bugs. |
|
I made another commit that might help: Same branch. |
|
sorry I manually apply the changes to 3.0.8. now using terrafrost/phpseclib:dev-3.0-kex-fix works perfectly! thank you! 👍 |
|
Using version 3.0.8 I also cannot getSeverIdentification() Connecting with another lib I got this: |
|
I really really wish you would provide the SSH2 logs. I asked for them before and was able to figure things out with them but it would have made it easier if you had provided them. As a reminder you can get them by doing Anyway, I'm not able to reproduce that issue: $ssh = new SSH2('127.0.0.1', 22);
echo $ssh->getServerIdentification();That works fine for me. So does this: $ssh = new SFTP('127.0.0.1', 22);
$ssh->login('username', 'password');
echo $ssh->getServerIdentification();That worked fine for me too. The fact that SSH2.php:1347 is called makes me think that you're calling The SSH2 logs would help me put the stack trace into context. Thanks! |
|
Hi @terrafrost, I sent the logs per e-mail and here what i did: version 3.0.8 fail with Expected SSH_MSG_KEXINIT Second try: fail with RuntimeException invalid_size |
|
I replied to your email. Thanks! |
|
Closing due to inactivity |
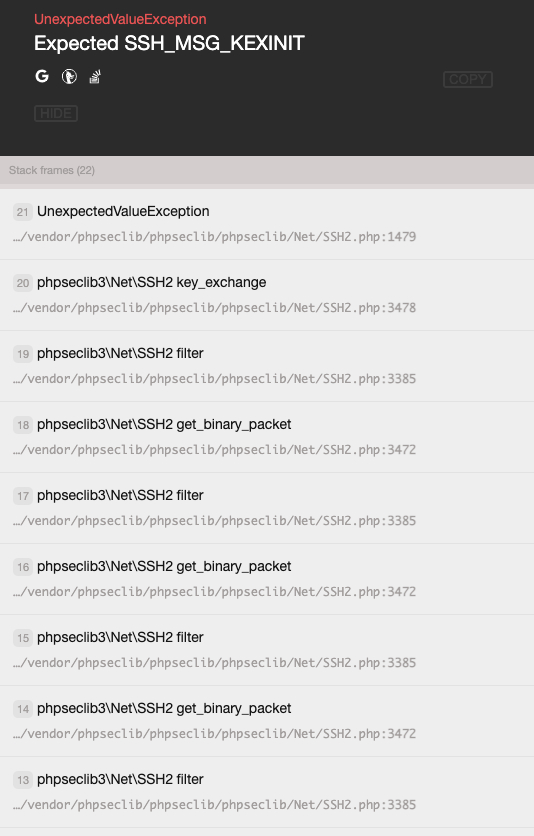

I have a Laravel 6 app which users SFTP to write content. once in a while the i'm getting the below error.
here we can see the function _get_binary_packet() and _filter() call each other recursively.
The SFTP file write task is inside a Background Job which is managed using Redis que.
After this error the subsequent Sftp put requests are not working.
I need to restart the laravel queue for the system to start working again. But the error popups after some time.
Machine : Ubuntu Linux 20.04
Apache : 2.4.46
php : 7.4.12
redis : 5.0.7
The text was updated successfully, but these errors were encountered: