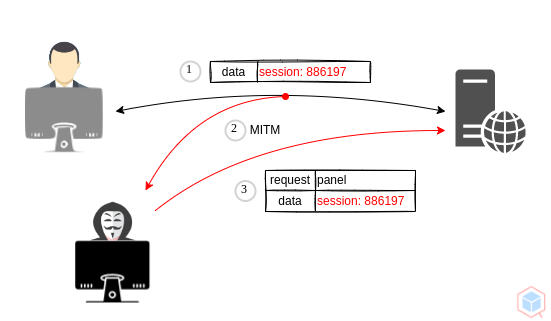
A threat actor may access the user's account using a stolen or leaked valid (existing) session identifier.
- Threat actor sniffs network traffic and gets a session identifier
- Threat actor uses the same session identifier to gain unauthorized access to a victim's account
Vary
- Gain unauthorized access
- Identity confirmation
- Regenerate session ids at authentication
- Timeout and replace old session ids
- Store ids in HTTP cookies
3693c458-c1b8-439f-8f0b-c3620c1c0129