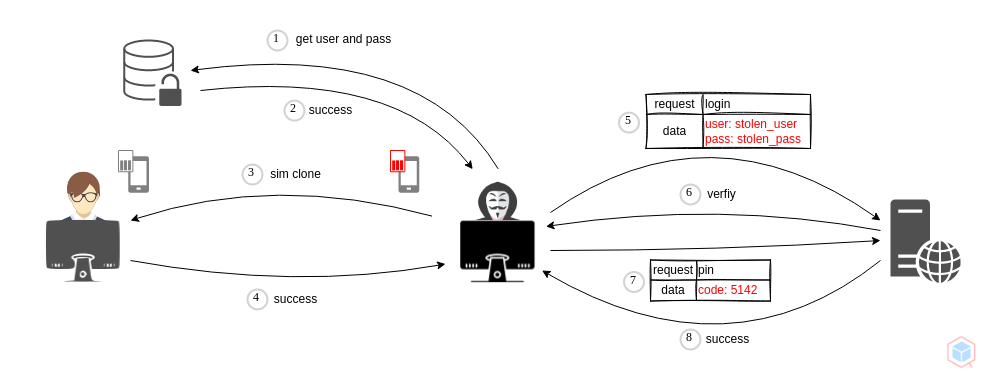
An adversary may utilize a sim swapping attack for defeating 2fa authentication.
- Adversary steals the username and password pair for website
- Adversary compromises the victim's sim card and clone it
- Adversary logs in with the stolen username and password
- Adversary receives a pin code on the compromised phone and uses it for verification.
High
- gain unauthorized access
- use more factors
58a84977-90e1-4156-a555-8568e83115d0
- howtogeek