-
-
Notifications
You must be signed in to change notification settings - Fork 112
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
UDP:1194 split tunnel didn't work in Tunnelblick until I routed all IPv4 traffic through the VPN #19
Comments
|
Upon reviewing your server.conf file and client.ovpn files, it appears you are attempting to set up a Split Tunnel VPN where only your DNS requests are sent over the encrypted VPN connection. This does not encrypt all of your Internet traffic, and only sends enough to the VPN server to achieve ad blocking. Your files are perfect as they are. The default setting in Tunnelblick to Route all IPv4 traffic through the VPN should be unchecked. It could become costly to send all of your traffic over the VPN Tunnel, so we are only sending the DNS traffic there with these configurations. Please keep it unchecked, this is the desired configuration for this reason. When you surf the Internet, you will be exposing your true IP address, and not the IP Address of your VPN Server. So why are the ads not being blocked / wrong DNS servers being used when you connect using these settings and configuration files? It is because at some point you manually configured DNS Servers on your Wireless and/or Wired Network Adapters. Open System Preferences | Network and click on the Network Adapter on the left column. Click the Advanced... button at the bottom right, and select the DNS Tab. Use the As far as the side question goes, you can toy around with removing the As far as the 2 options you have tried, I'm afraid you've lost me. Perhaps we can try and resolve that in a separate issue. If the instructions to remove manually configured DNS Servers on your Network Adapters does not resolve this issue, please let me know what version of macOS and Tunnelblick you are using. If this does resolve your issue, feel free to close this issue out. |
|
I haven't explicitly changed my DNS configuration, and within the DNS tab, there's nothing I'm able to remove, however, it does appear as though my internet company uses 10.0.1.1 as it is grayed out in the DNS server section, and my cable provider's domain is grayed out in the Search Domains area as well. FWIW, full tunnel does work on my iOS and OSX for me at the moment. re: the options, I've tried, I'm lost as well. I was essentially just throwing stuff at the wall to see what might stick. |
|
I am assuming your IP Address is assigned dynamically (via DHCP) and is not static. Open System Preferences | Network and click on the Network Adapter on the left column. Make note of the DNS Server that appears here. I suspect it will be your ISPs provided DNS Server, which you said is 10.0.1.1. (The value for the DNS Server should be grayed out text if it was acquired via DHCP.) Then use Tunnelblick to establish a Split Tunnel VPN Connection to your server. When the VPN connects, Tunnelblick should have updated the DNS Server to read 10.8.0.1. Do you see this change happening? (I am hoping the answer to this question is Yes.) If the answer to the question above is not yes - an ugly solution is to set 10.8.0.1 as your DNS Server manually, so it is the very first DNS Server that is queried. If your VPN is not connected, then this DNS Server will be unreachable, and it will default to the next DNS Server in the list. |
|
Tried getting it running all this weekend, but no go... My IP address is assigned dynamically via DHCP, yes, but 10.0.1.1 is the DNS LAN address created through the Airport Extreme router - not the ones(2) my ISP has assigned. Those can be seen greyed out in my Airport Utility settings under the Internet tab. They also appear as the two DNS servers on the Airport Utility main page when I click Internet.
Yes, both the DNS Servers and Search Domains change to 10.8.0.1 and 'openvpn' respectively. I've also tried a few other things with mixed results - either not being able to connect at all, or being able to connect but my IP still remains unchanged. Added '10.8.0.1' ONLY via System Preferences | Network | Advanced | DNS tab Added '10.8.0.1' and '10.0.1.1' in that order Added '10.1.1.1' and '10.8.0.1' in that order |
|
Wanted to follow up here; are you able to try the Wireguard + Pi-Hole solution? |
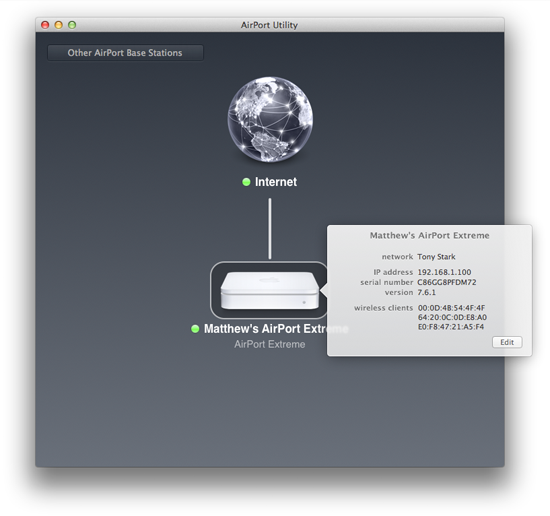
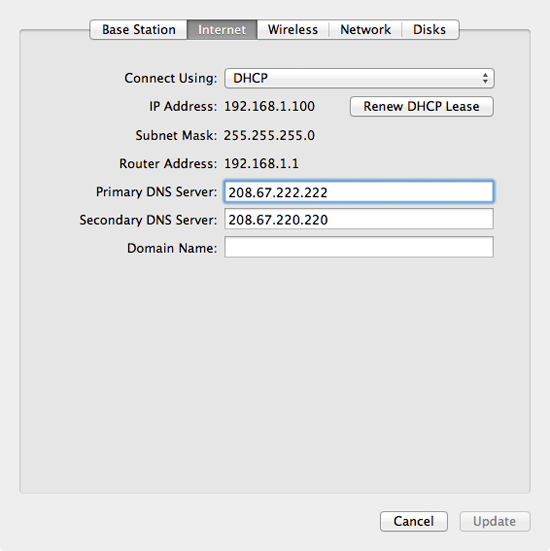


I just wanted to mention, by default, the configuration settings tab in Tunnelblick has Route all IPv4 traffic through the VPN unchecked. As a result, the following warning appears shortly after trying to connect:
Selecting the option and attempting to reconnect seems to have fixed the issue and is the only way I've been able to get it working using the following server/client config file setup:
server.conf
client.ovpn
Can you confirm that I haven't done anything "wrong" by selecting that option?
Side Question:
The push "block-outside-dns" line in server.conf causes a warning/error, apparently because the line is for Windows computers. Outside of commenting out the line entirely(which I don't want to do), is something I can add to my non-windows client .ovpn files that would get rid of the warning altogether? I've tried both of the following options, with no luck and keep getting a "files or directories don't exist" even though '/etc/openvpn/update-resolv-conf' is on my VM.
and
If my side question is too far out of the scope of the original issue, I can submit a new one.
Thanks
The text was updated successfully, but these errors were encountered: