-
Notifications
You must be signed in to change notification settings - Fork 2.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Terraform-module provider unable to parse some git url #15467
Comments
|
Hi there, Help us by making a minimal reproduction repository. Before we can start work on your issue we first need to know exactly what's causing the current behavior. A minimal reproduction helps us with this. To get started, please read our guide on creating a minimal reproduction to understand what is needed. We may close the issue if you (or someone else) have not provided a minimal reproduction within two weeks. If you need more time, or are stuck, please ask for help or more time in a comment. Good luck, The Renovate team |
|
If I specify the url using this format it works: |
|
Hi after this change, the regex matched the problematic URL successfully. |
|
For authentication to gitlab terraform modules, using https, I use host rules. I'm using renovate runner on gitlab, so it has the variables used, but you can replace these with the hard coded url and a private token that have access to the repo with modules "hostRules": [
{
"hostType": "terraform-module",
"matchHost": "$CI_SERVER_HOST",
"token": "$CI_JOB_TOKEN"
}
], |
|
I think when it's a git URL we can't be sure of what type of host it is, even though "if the host name contains gitlab then it's probably gitlab" is a sound guess. Do you plan to treat these as |
|
Yes, Azure URLs are treated as |
How are you running Renovate?
Self-hosted
If you're self-hosting Renovate, tell us what version of Renovate you run.
32.41.2
Please select which platform you are using if self-hosting.
GitLab self-hosted
If you're self-hosting Renovate, tell us what version of the platform you run.
14.9.4
Was this something which used to work for you, and then stopped?
I never saw this working
Describe the bug
Hello,
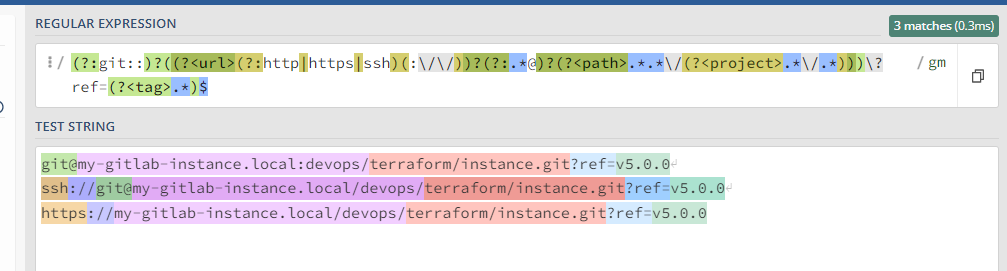
I'm trying to make terraform module updates using renovate on our self hosted gitlab instance. Actually, renovate reports 'invalid-version' for this kind of git url:
If I switch to
https://my-gitlab-instance.local/devops/terraform/instance.git?ref=v5.0.0it works but renovate cannot authenticate properly.This is already working for instance for the ansible-galaxy so I think that this should also be supported here.
The problem is the regex here.
Best,
Jerome
Relevant debug logs
Logs
Have you created a minimal reproduction repository?
No reproduction repository
The text was updated successfully, but these errors were encountered: