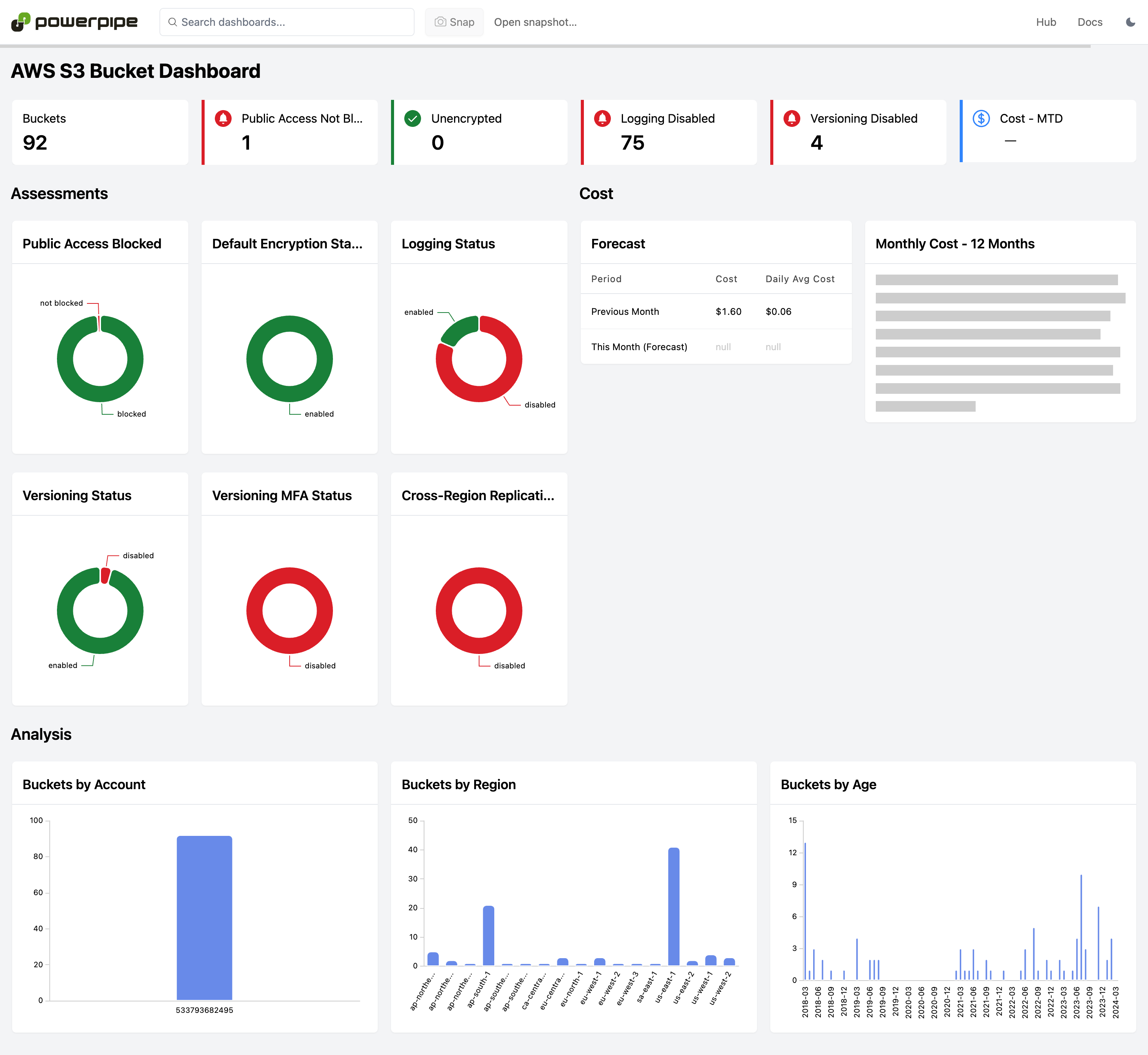
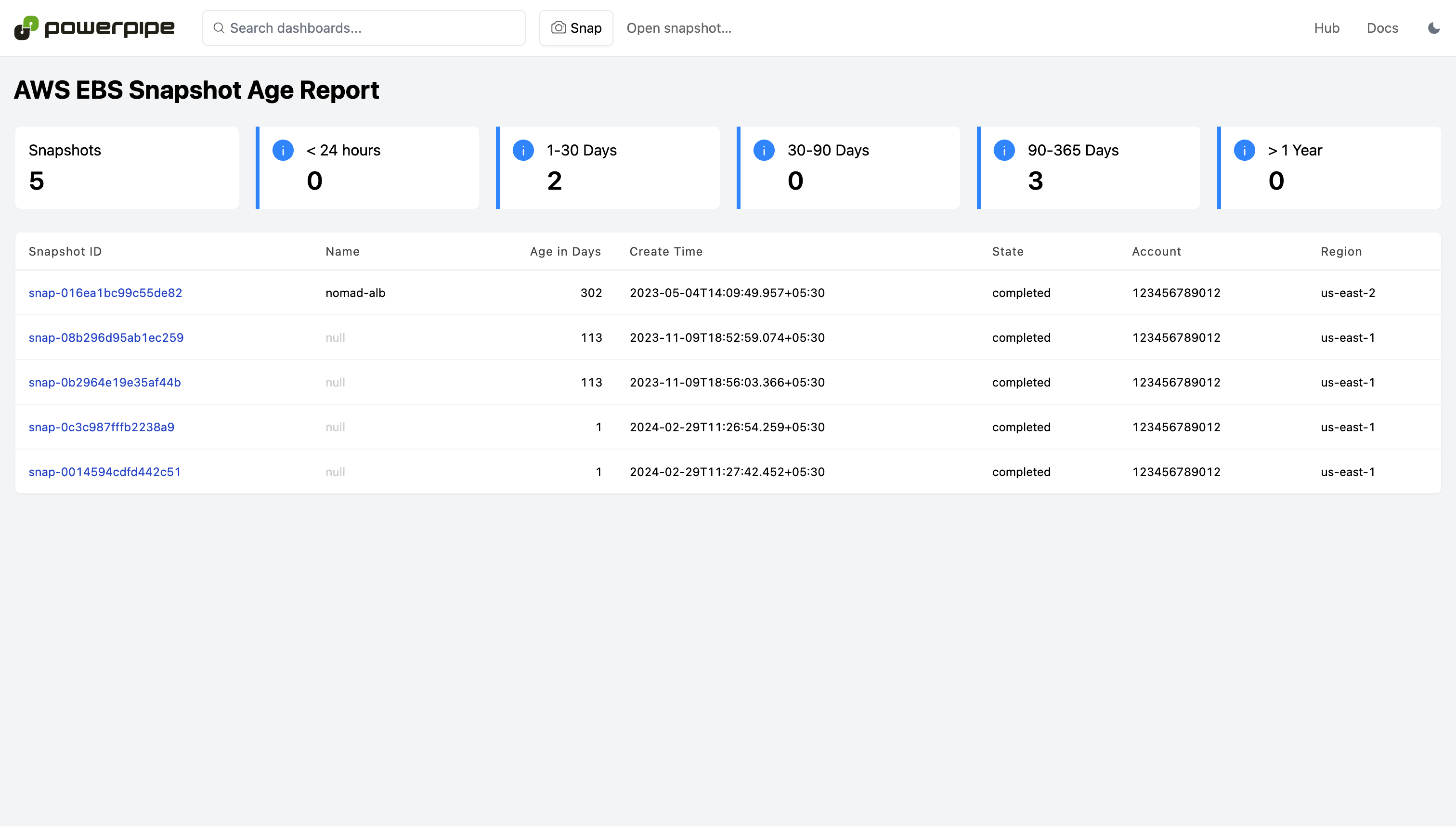
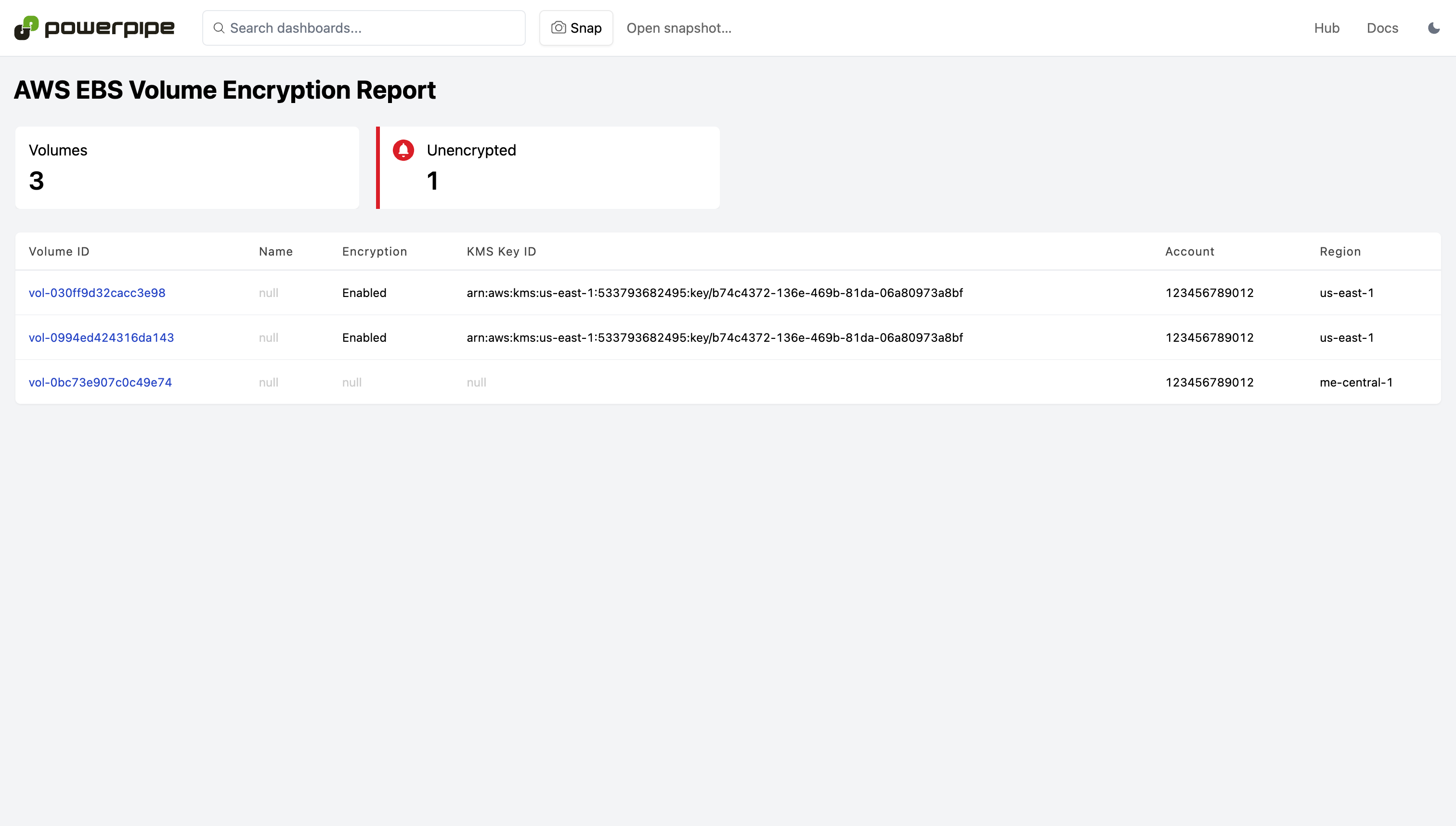
DevOps professionals use the AWS insights mod to visualize cloud intelligence and security metrics using interactive dashboards. Report on AWS resource configuration, visualize relationships, and aggregate metrics to better understand your cloud infrastructure. The dashboards are specified using a "low code" HCL format (similar to Terraform). Making it easy to inspect, modify and compose new dashboards to meet specific compliance and security objectives for your organization.
Resource type Dashboards have interactive elements that can answer questions like:
- How many of this resource type do I have?
- Counts by accounts and regions?
- Cost of these resources over time.
- Percentage of resources that are configured in specific ways (e.g. encryption on?)
- How old are my resources?
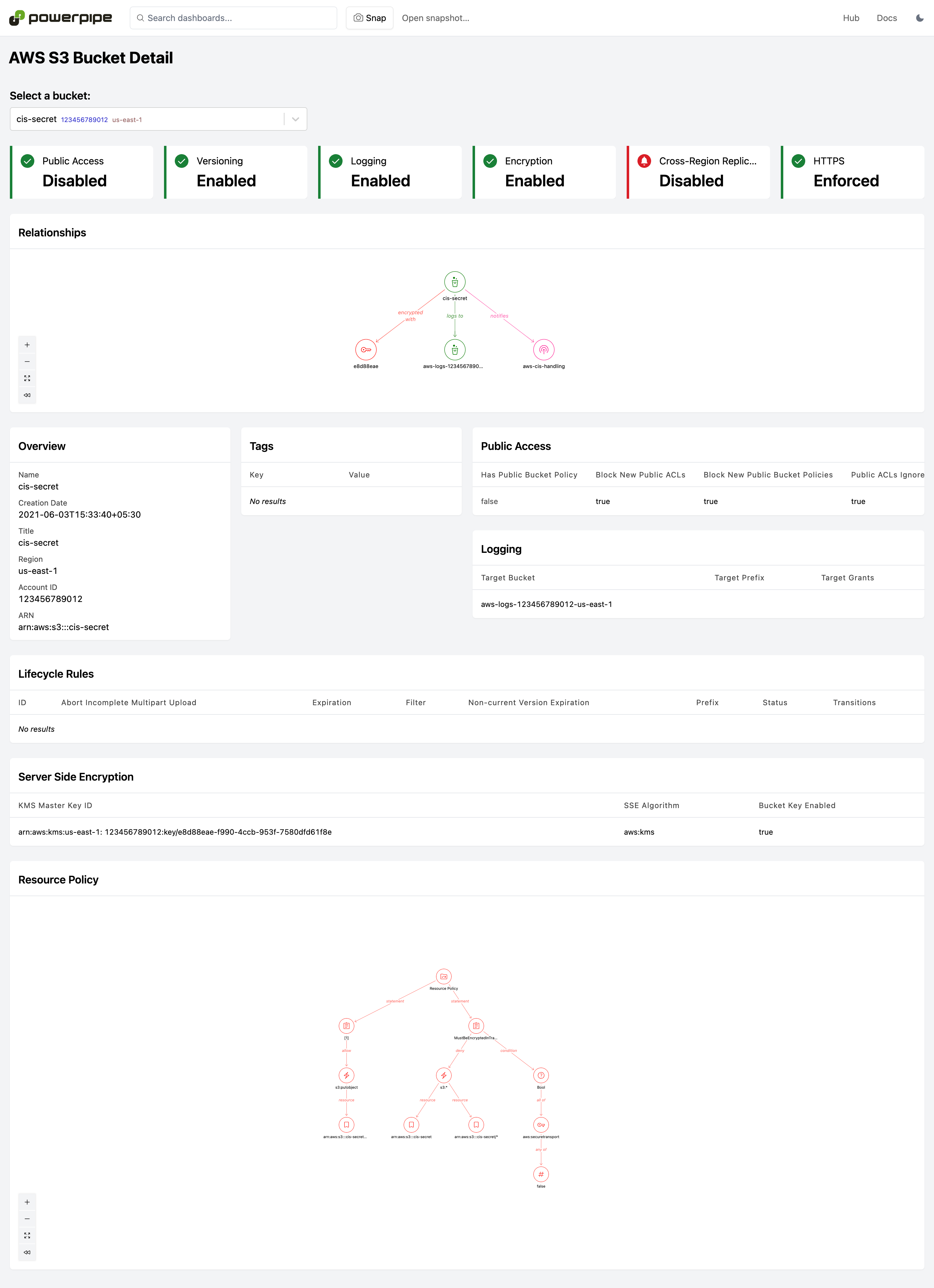
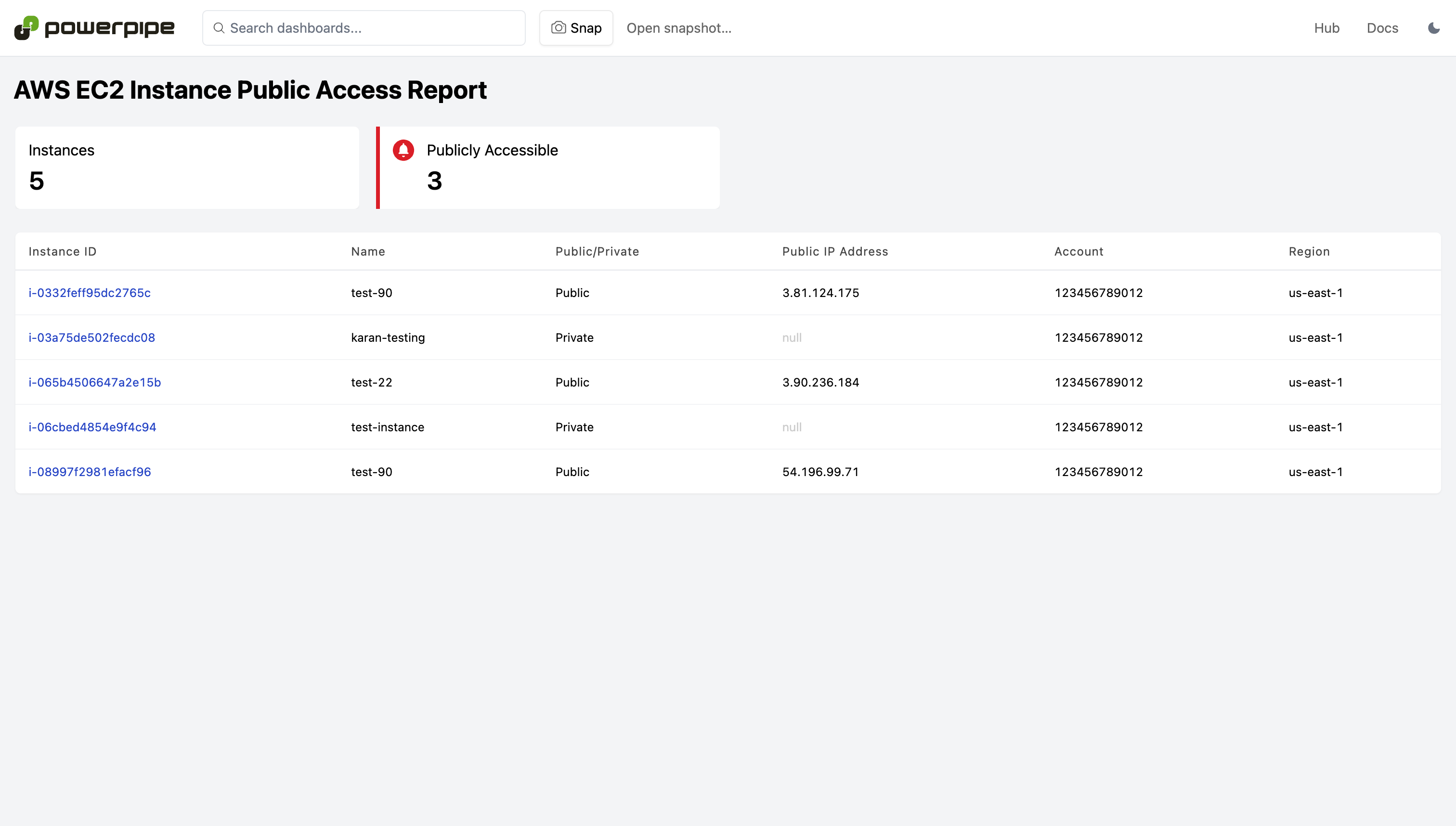
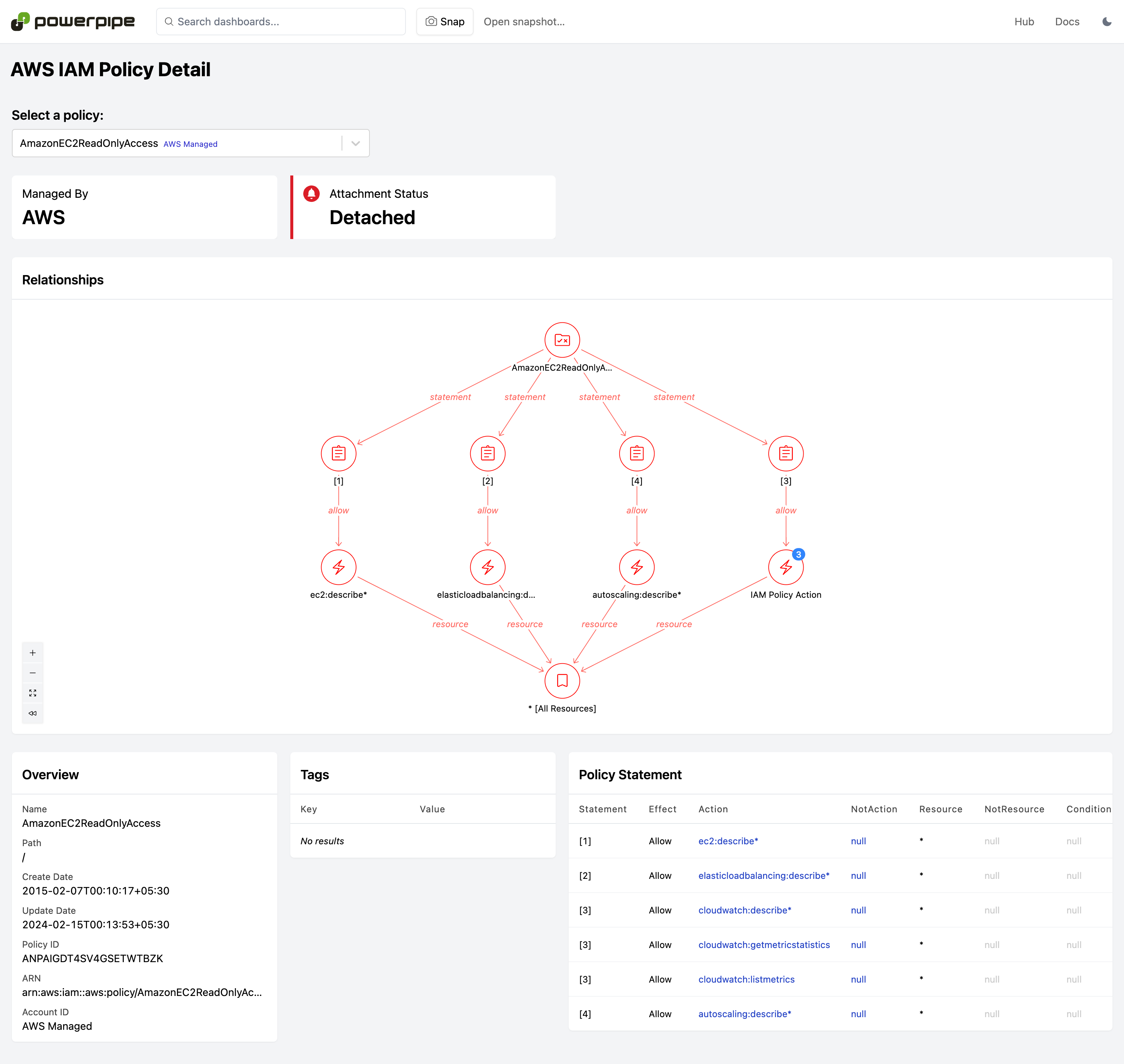
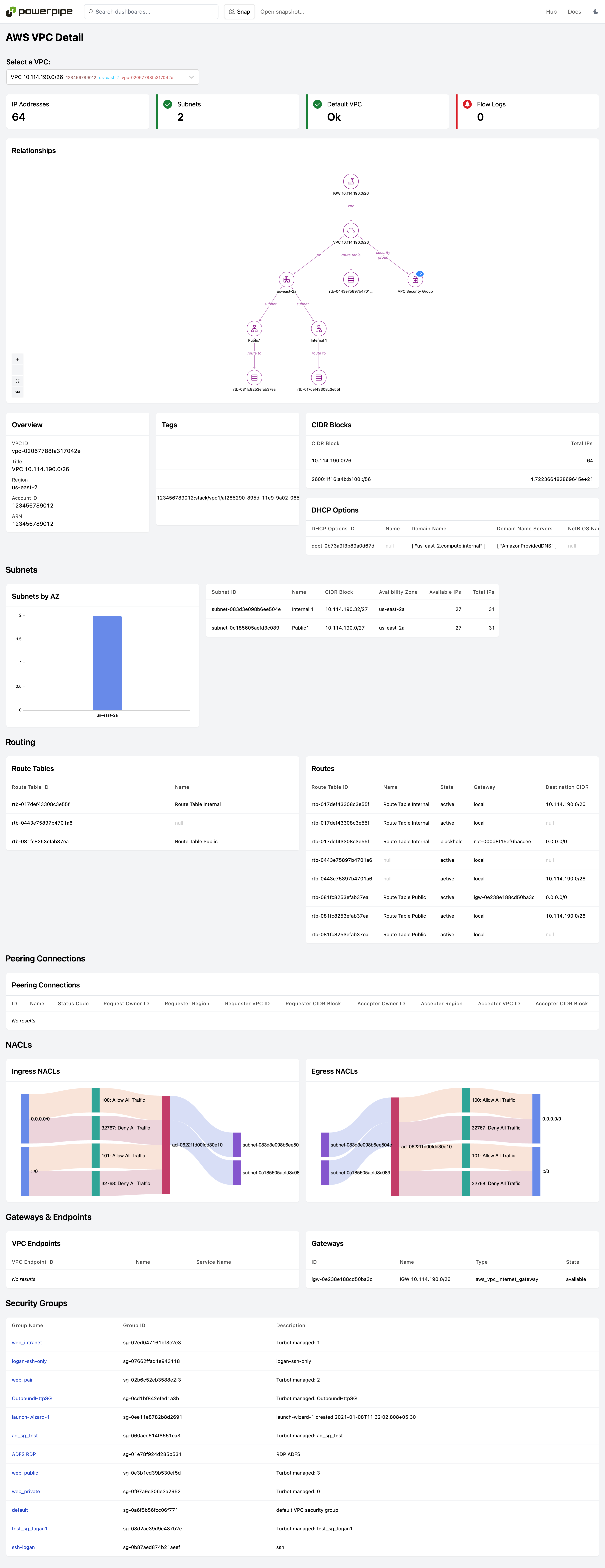
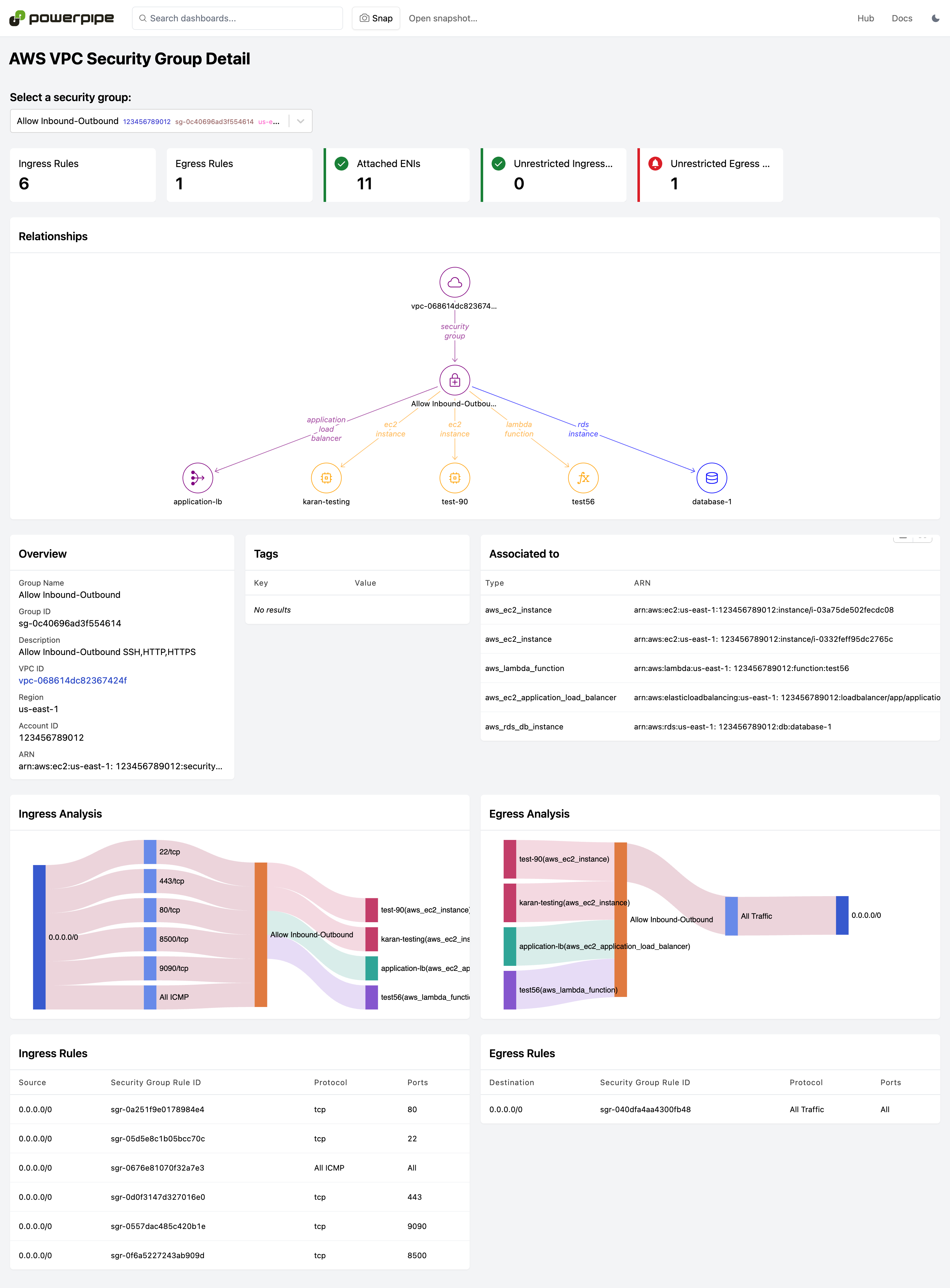
Resource detail reports can be reached by drilling down from dashboards or manually selecting the resource name. They drill into a specific resource and can answer detailed configuration questions and provide a visualization of relationships to other resources. Use these to answer deep questions:
- What are the relationships between this resource and others?
- Is this resource publicly accessible?
- Is encryption enabled and what keys are used for encryption?
- Is versioning enabled?
- What networking ingress and egress rules are associated with this resource.
Dashboards are available for 30+ services, including CloudTrail, EC2, IAM, RDS, S3, VPC, and more!
Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
brew install turbot/tap/powerpipeThis mod also requires Steampipe with the AWS plugin as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
brew install turbot/tap/steampipe
steampipe plugin install awsSteampipe will automatically use your default AWS credentials. Optionally, you can setup multiple accounts or customize AWS credentials.
Finally, install the mod:
mkdir dashboards
cd dashboards
powerpipe mod init
powerpipe mod install github.com/turbot/steampipe-mod-aws-insightsStart Steampipe as the data source:
steampipe service startStart the dashboard server:
powerpipe serverBrowse and view your dashboards at http://localhost:9033.
This repository is published under the Apache 2.0 license. Please see our code of conduct. We look forward to collaborating with you!
Steampipe and Powerpipe are products produced from this open source software, exclusively by Turbot HQ, Inc. They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our Open Source FAQ.
Want to help but don't know where to start? Pick up one of the help wanted issues: