Remove wazuh-slack active response script from next Wazuh version
#16645
Labels
feed/active response
Active response scripts (not the module)
level/task
module/active response
type/enhancement/usability
Description
The Integrator daemon allows Wazuh to connect to external APIs and alerting tools such as Slack, PagerDuty, VirusTotal, and Shuffle.
The integration with Slack uses Incoming Webhooks and allows posting Wazuh alerts into a Slack channel using the following sample configuration in
/var/ossec/etc/ossec.conf:This Integration uses the optional filters fields to determine which alerts should be sent to the external platforms. Only the alerts that meet the filter conditions are sent. If no filters are specified, all alerts are sent.
In the same time, there is also a wazuh-slack active response which is available only for Linux/Unix endpoints and require additional parameters or specific use cases when forwarding alerts to a Slack channel.
This issue aims to remove the limited
wazuh-slackactive response script from next Wazuh versions and ensure that users request to the Slack Integration to forward Wazuh alerts into a Slack channel.Current usage of
wazuh-slackTo use the current
wazuh-slackactive response, follow the steps below:webhook_urlfor the Slack workspace where alerts would be sent by using the steps here./var/ossec/etc/ossec.conf:This configuration limits the execution of the active response to when a file creation alert is triggered. `<WEBHOOK_URL> is the webhook URL for the Slack workspace.
4. Restart the Wazuh manager to apply the configuration changes:
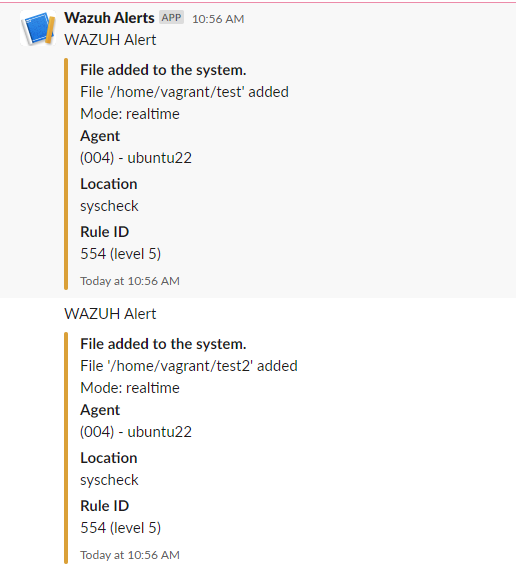
/var/ossec/etc/ossec.conf:Result of the active response
Slack alerts
General notes
The text was updated successfully, but these errors were encountered: