HTTP Switchboard as NoScript
You can configure HTTP Switchboard in such a way as to make it behaves close to how NoScript for Firefox works.
Here is how the matrix would look like:
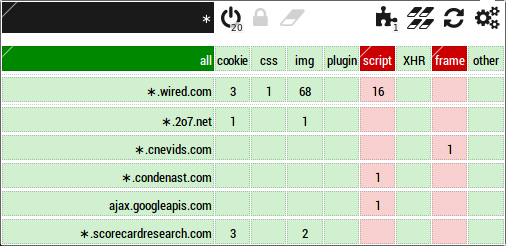
I created a backup file which can be restored (from the About tab) in order to make HTTPSB behave close to how NoScript works:
NoScript comes with a preset list of hostnames for which javascript is allowed, this list has been included in the above setup file as ubiquitously whitelisted hostnames. In order for this whitelist to work properly, "strict blocking" is disabled in the above setup file.
Remember: Restoring data from a full backup file will overwrite all your settings!
Not really. I supposed the erroneous impression stems from all the cells in the matrix. It does not require more management. If a user wants to allow one script from one page, one click is sufficient with HTTP Switchboard, just like NoScript. Admittedly though, if a user wants to allow one or more scripts permanently, an extra click is required, to tell HTTPSB to persist the whitelisted cells in the matrix, since by design, all permissions are temporary -- with the benefit that as opposed to NoScript, there is no need to duplicate every hostname in the menu (one for temporary permission, one for permanent permission.)
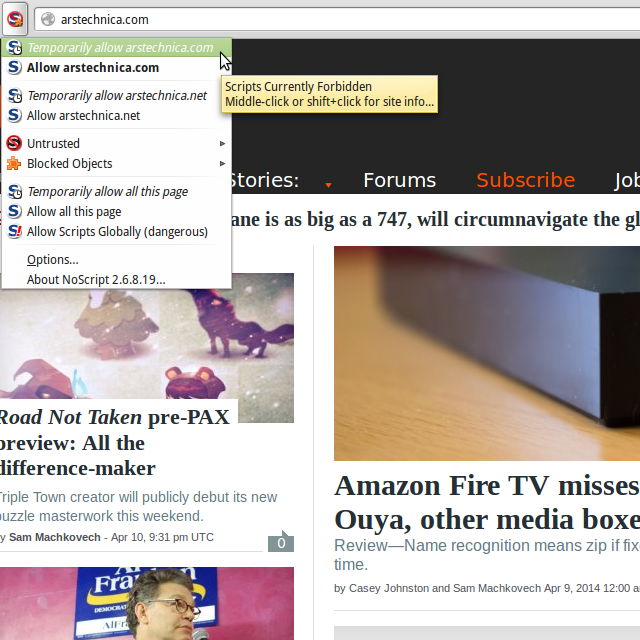
####Consider NoScript:
####And now HTTPSB:
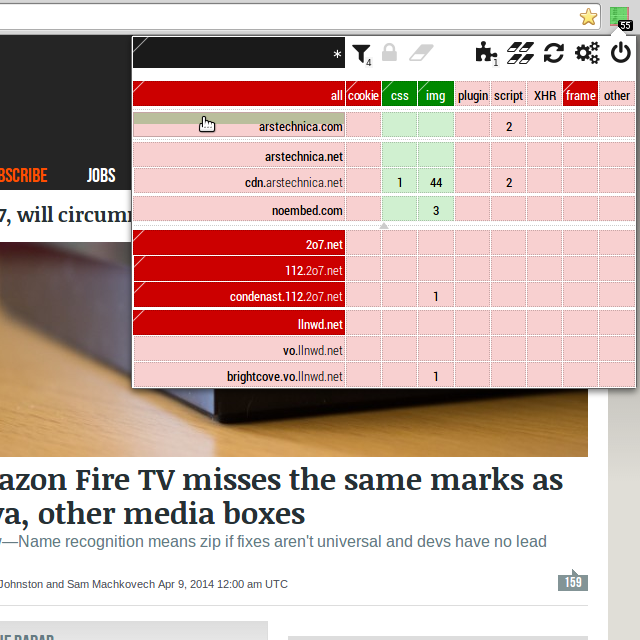
In both case, one single click was required to enable scripts temporarily from arstechnica.com.
From the two screenshots, one can see however that HTTPSB refers to more hostnames than NoScript: It is because HTTPSB will report all net traffic, i.e. not just that of scripts on the page. In the example above, one can see that with out-of-the-box settings, HTTPSB also blocked a tracking pixel from condenast.112.2o7.net.
Of course, the more scripts allowed by a user, the more tracking pixels and other annoyances are going to be reported by HTTPSB. To get the same similar (but falling short) level of information and control, a user would have to also install Request Policy aside NoScript. (I say "falling short" because Request Policy categorizes request only using their hostname, it does not further categorize requests by type.)