This repository has been archived by the owner on Dec 19, 2023. It is now read-only.
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Metadata *
Bounty URL: https://www.huntr.dev/bounties/2-other-monica
⚙️ Description *
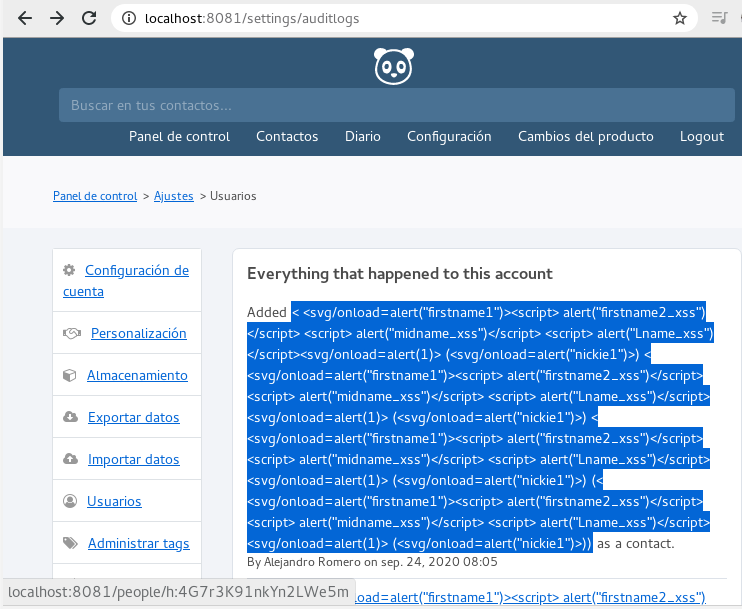
XSS queries being triggered from people info page by the audit log at the settings, fix sanitizes content before showing to user.
Technical Description *
Even tough Laravel has inbuilt protection for XSS it has been disabled when presenting log:
{!! $log['description'] !!}to enable embeding contact links, leading to XSS, htmlentities was used to sanitize data before showing to user, efectively avoiding new as well as already stored XSS.Edit
Looking further into the code I realized the XSS protection have been disabled in many views so I added a Middleware that will strip html tags using
strip_tags, and sincestrip_tagscan be tricked with malformed markup reamaning input is encoded using htmlentities.Middleware is at app/Http/Middleware/SanitizeInput.php and can be tunned for specific keys adding them to the
$exceptarray:Proof of Concept (PoC) *
< <svg/onload=alert("firstname1")><script> alert("firstname2_xss")</script> <script> alert("midname_xss")</script> <script> alert("Lname_xss")</script><svg/onload=alert(1)> (<svg/onload=alert("nickie1")>)Proof of Fix (PoF) *
After fix introduced data is displayed as text and no XSS is executed
Stored XSS will be also stripped out and encoded after contact is edited
User Acceptance Testing (UAT)
Functionallity is unafected, contact link works as usual