- Support port service brute and target scanning (compatible with Debian/Centos/Ubuntu/Kali/Mint,if you use the docker container run the script,then compatible with all linux distros)
- There is no purpose in writing this script, just for the convenience of security testers and improve system security, there is no mercy in the battlefield, if you pick up the hands of weapons, you will make a terrible mistake.
- The author is not responsible for any legal consequences arising out of the user's use of this script.
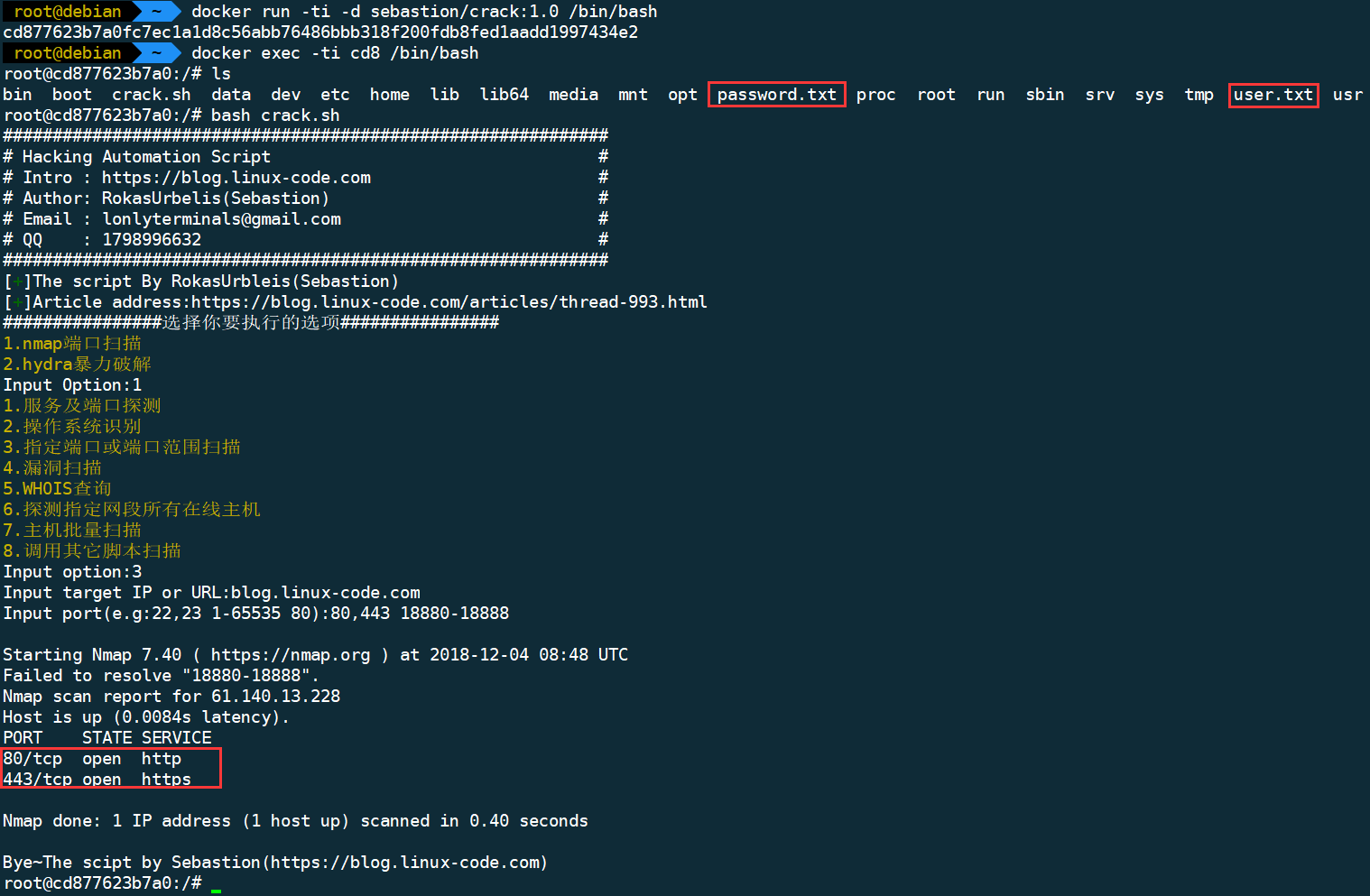
- Container operation mode the root directory of the cabin
user.txtandpassword.txttwo files, also you can use a custom dictionary by yourself
The following two methods of security testing are supported
-
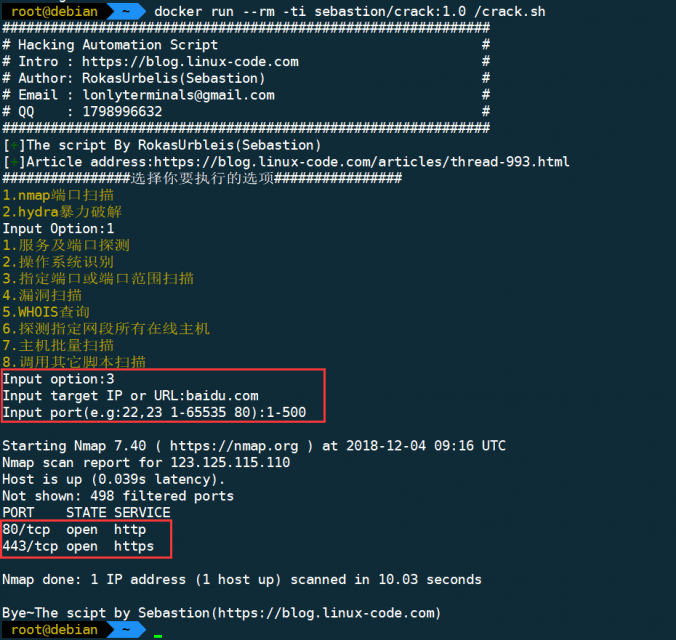
nmap
- 1.Service and port scanning
- 2.OS identification
- 3.Specifies a port or port range to scanning
- 4.Vulnerability scanning
- 5.WHOIS query
- 6.Probes all online hosts in a specified network segment
- 7.Host batch scanning
- 8.Call any nmap scripts to scanning
-
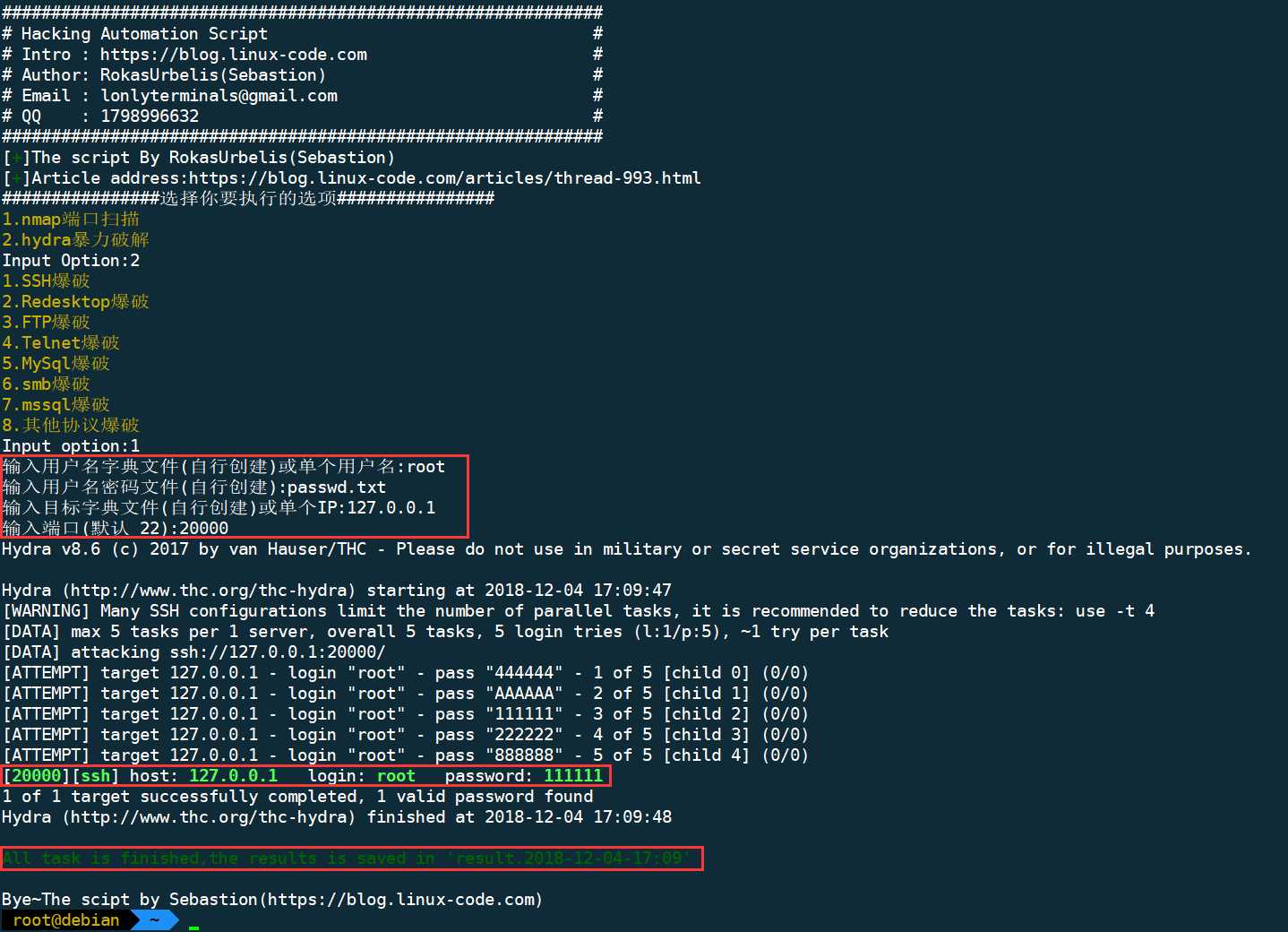
hydra
- 1.SSH brute
- 2.Redesktop brute
- 3.FTP brute
- 4.Telnet brute
- 5.MySql brute
- 6.Smb brute
- 7.Mssql brute
- 8.Other protocol brute
There are currently several supported protocols:
asterisk cvs cisco-enable firebird ftp ftps icq imap irc ldap2 nntp mssql mysql oracle-sid pcanywhere pcnfs pop3 rdp postgres radmin2 rexec rlogin rpcap rtsp sip smb smtp smtp-enum socks5 ssh sshkey svn teamspeak vnc xmpp
git:
git clone https://github.com/RokasUrbelis/system_security_testing.git
cd crack
bash crack.shcurl:
bash -c "$(curl -fsSl https://blog.linux-code.com/scripts/crack.sh)"docker container:
docker run -ti --name crack sebastion/crack:1.0 crack.shenter the container:
docker run -ti -d --name crack1 sebastion/crack:1.0 /bin/bash
docker exec -ti $(awk '{FS="[ ]+"}{if(NR==2){print $1}}'< <(docker ps -l)) /bin/bash
bash crack.shtemporary container run:
docker run --rm -ti sebastion/crack:1.0 /crack.shUse Dockerfile to build the image and run the container:
git clone https://github.com/RokasUrbelis/system_safety_test.git
cd system_safety_test
docker build -t crack:1.0 .
docker run --ti --rm crack:1.0- Email: Rokas.Yang@gmail.com
- QICQ :1798996632
- And Blog😊(Subscribe to our RSS feed for more technical articles)