-
Notifications
You must be signed in to change notification settings - Fork 1.9k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Go through all Kafka passwordless quickstart/migration-guide to make sure following them can work #30800
Comments
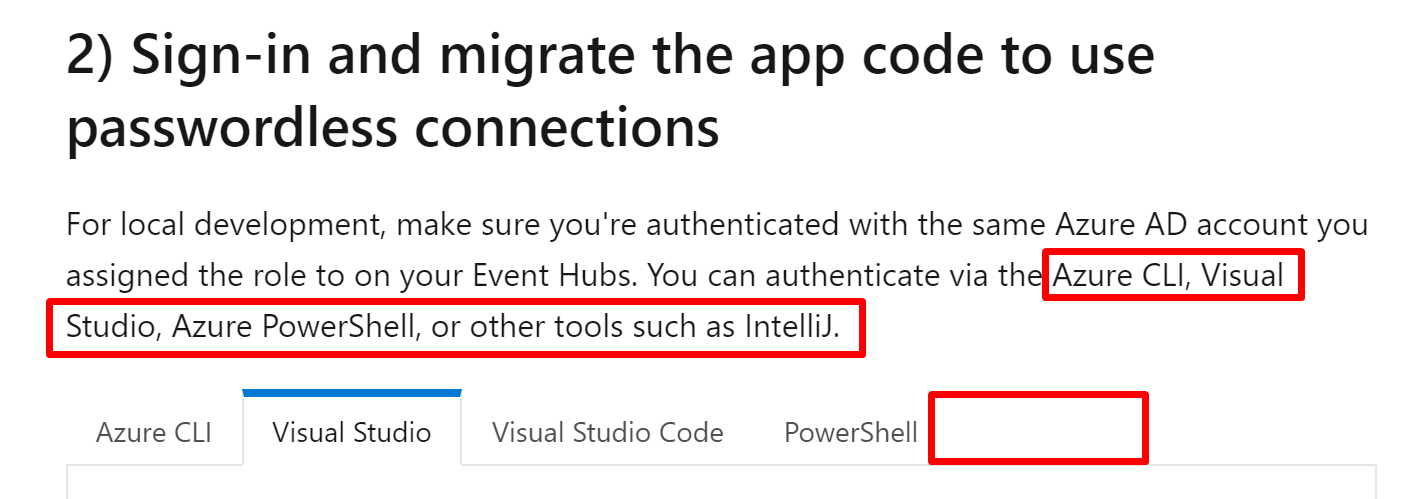
Quick start feedback:Link to quick start: https://review.docs.microsoft.com/en-us/azure/developer/java/spring-framework/configure-spring-cloud-stream-binder-java-app-kafka-azure-event-hub?branch=pr-en-us-3583&tabs=passwordless
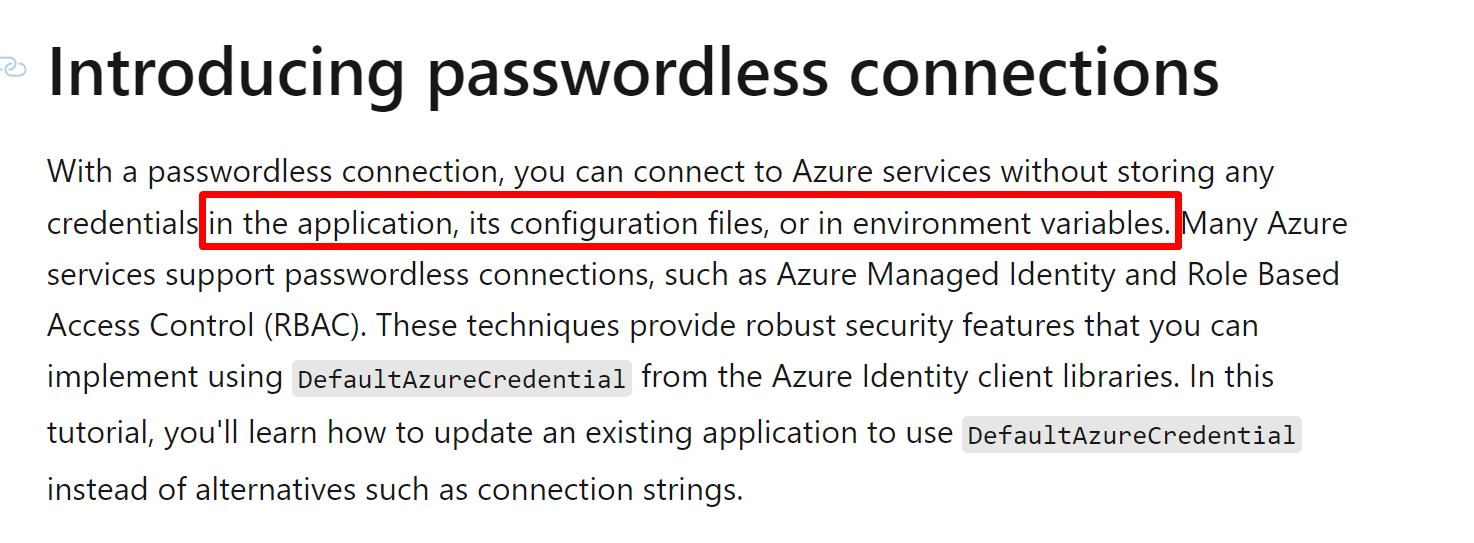
1.1. Azure Active Directory (Azure AD) authentication Event Hubs provides an endpoint compatible with the Apache Kafka® producer and consumer APIs. This quick start is not using Apache Kafka. My suggestion:
This problem has been solved by this:
Refs: https://github.com/git-for-windows/build-extra/blob/main/ReleaseNotes.md We can write this down in the doc in case other reader face the same problem.
|
Feedback of Migration guideBTW, why this feature is not written in the changelog? https://github.com/Azure/azure-sdk-for-java/blob/main/sdk/spring/CHANGELOG.md
8, Change link from .net to java Current link is about .net: https://review.docs.microsoft.com/en-us/dotnet/api/overview/azure/Identity-readme#defaultazurecredential
13... |
|
|
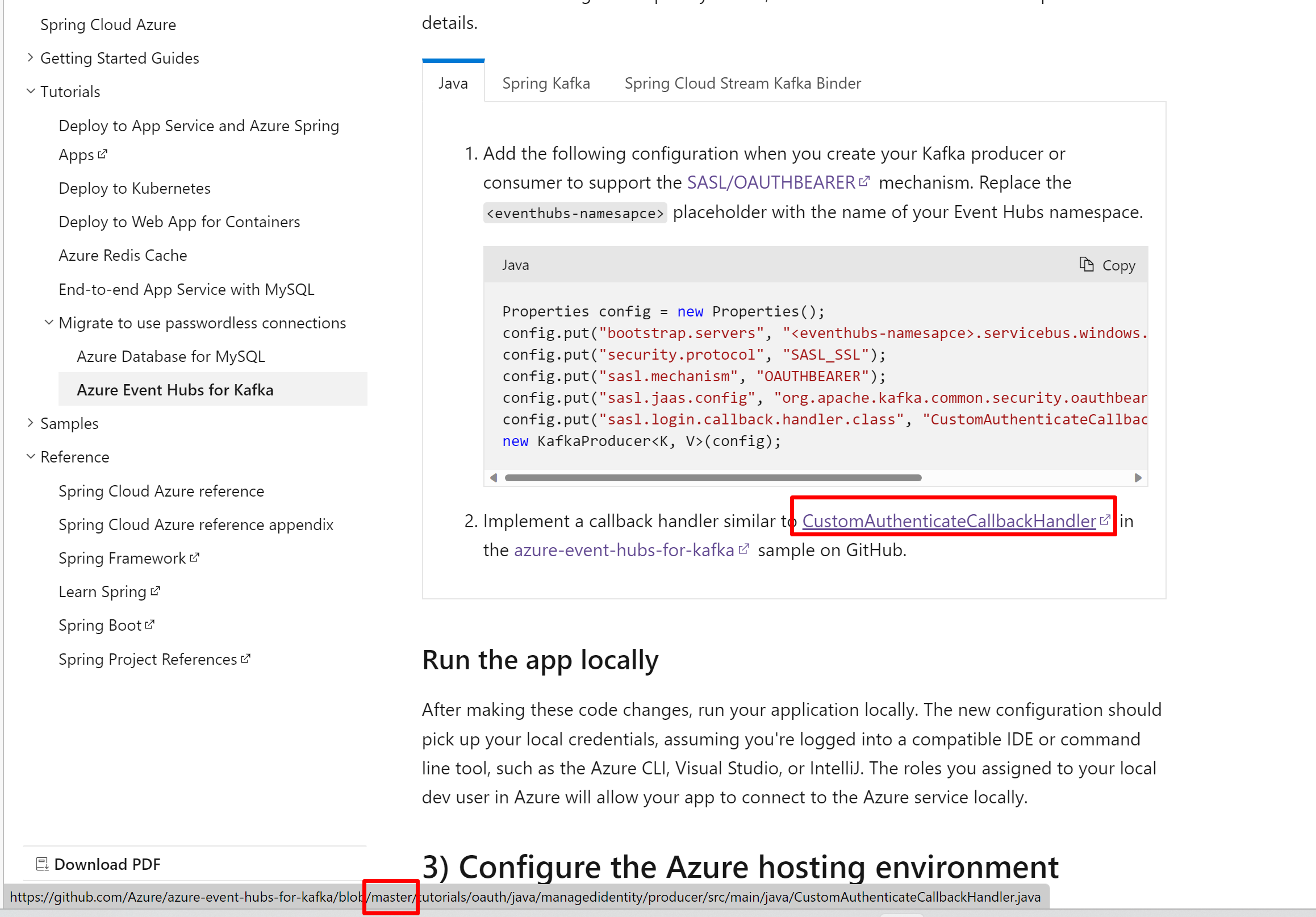
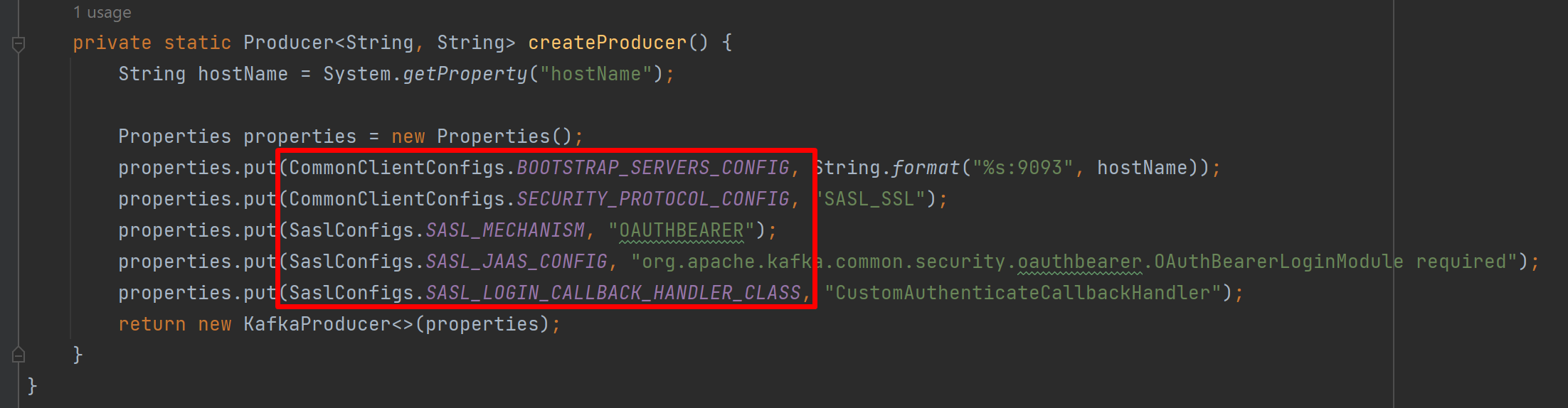
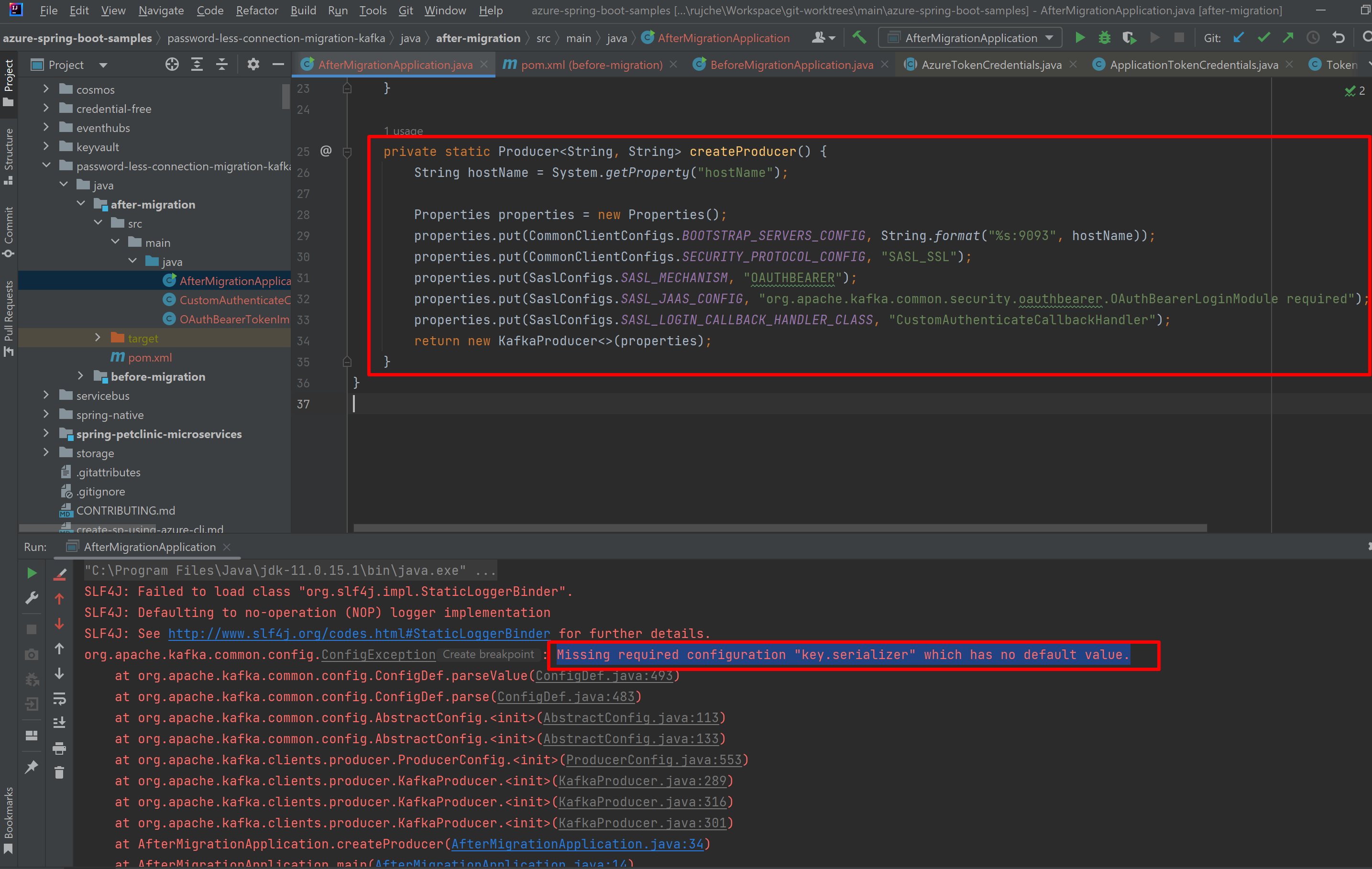
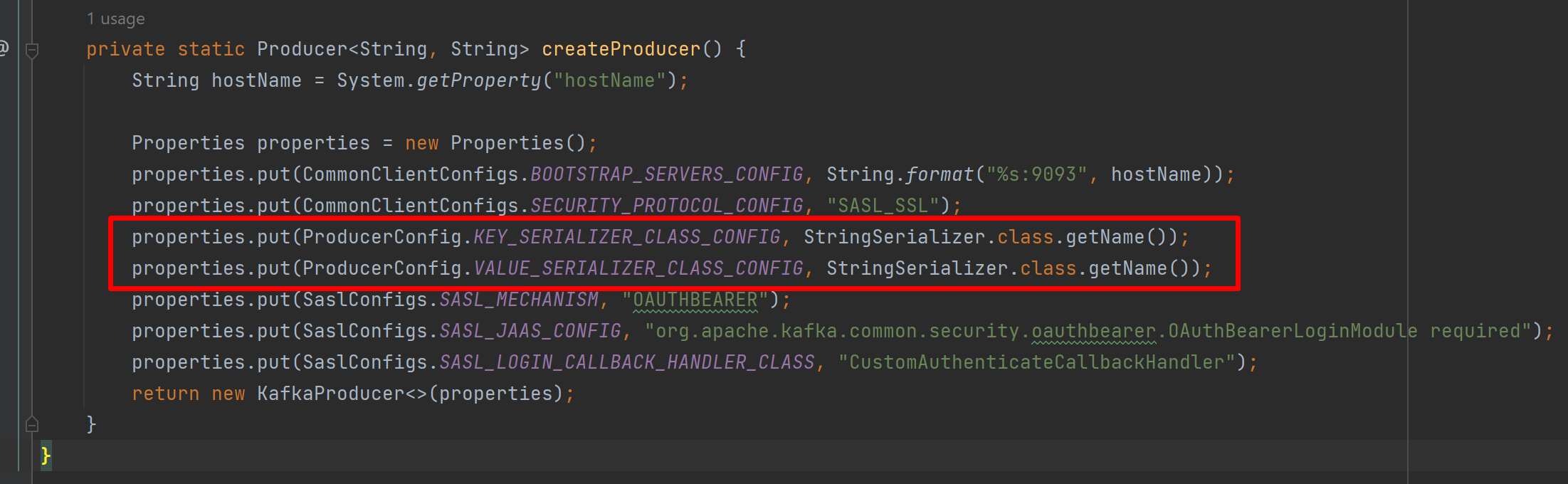
Fixed by adding the 2 properties: properties.put(ProducerConfig.KEY_SERIALIZER_CLASS_CONFIG, StringSerializer.class.getName());
properties.put(ProducerConfig.VALUE_SERIALIZER_CLASS_CONFIG, StringSerializer.class.getName()); |
Code of import com.microsoft.azure.credentials.AzureCliCredentials;
import com.nimbusds.jwt.JWT;
import com.nimbusds.jwt.JWTClaimsSet;
import com.nimbusds.jwt.JWTParser;
import org.apache.kafka.clients.producer.ProducerConfig;
import org.apache.kafka.common.KafkaException;
import org.apache.kafka.common.security.auth.AuthenticateCallbackHandler;
import org.apache.kafka.common.security.oauthbearer.OAuthBearerToken;
import org.apache.kafka.common.security.oauthbearer.OAuthBearerTokenCallback;
import javax.security.auth.callback.Callback;
import javax.security.auth.callback.UnsupportedCallbackException;
import javax.security.auth.login.AppConfigurationEntry;
import java.io.IOException;
import java.net.URI;
import java.text.ParseException;
import java.util.Arrays;
import java.util.List;
import java.util.Map;
import java.util.concurrent.ExecutionException;
import java.util.concurrent.TimeoutException;
public class CustomAuthenticateCallbackHandler implements AuthenticateCallbackHandler {
final static AzureCliCredentials CREDENTIALS;
static {
try {
CREDENTIALS = AzureCliCredentials.create();
} catch (IOException e) {
throw new RuntimeException(e);
}
}
// final static MSICredentials CREDENTIALS = new MSICredentials();
// Use AppServiceMSICredentials instead for App Service deployment.
// final static AppServiceMSICredentials CREDENTIALS = new AppServiceMSICredentials(AzureEnvironment.AZURE);
private String sbUri;
@Override
public void configure(Map<String, ?> configs, String mechanism, List<AppConfigurationEntry> jaasConfigEntries) {
String bootstrapServer = Arrays.asList(configs.get(ProducerConfig.BOOTSTRAP_SERVERS_CONFIG)).get(0).toString();
bootstrapServer = bootstrapServer.replaceAll("\\[|\\]", "");
URI uri = URI.create("https://" + bootstrapServer);
this.sbUri = uri.getScheme() + "://" + uri.getHost();
}
public void handle(Callback[] callbacks) throws IOException, UnsupportedCallbackException {
for (Callback callback: callbacks) {
if (callback instanceof OAuthBearerTokenCallback) {
try {
OAuthBearerToken token = getOAuthBearerToken();
OAuthBearerTokenCallback oauthCallback = (OAuthBearerTokenCallback) callback;
oauthCallback.token(token);
} catch (InterruptedException | ExecutionException | TimeoutException | ParseException e) {
e.printStackTrace();
}
} else {
throw new UnsupportedCallbackException(callback);
}
}
}
OAuthBearerToken getOAuthBearerToken() throws InterruptedException, ExecutionException, TimeoutException, IOException, ParseException
{
String accessToken = CREDENTIALS.getToken(sbUri);
JWT jwt = JWTParser.parse(accessToken);
JWTClaimsSet claims = jwt.getJWTClaimsSet();
return new OAuthBearerTokenImp(accessToken, claims.getExpirationTime());
}
public void close() throws KafkaException {
// NOOP
}
}Log: This problem is not solved yet. |
|
Property like My suggestion: 2 options:
|
|
|
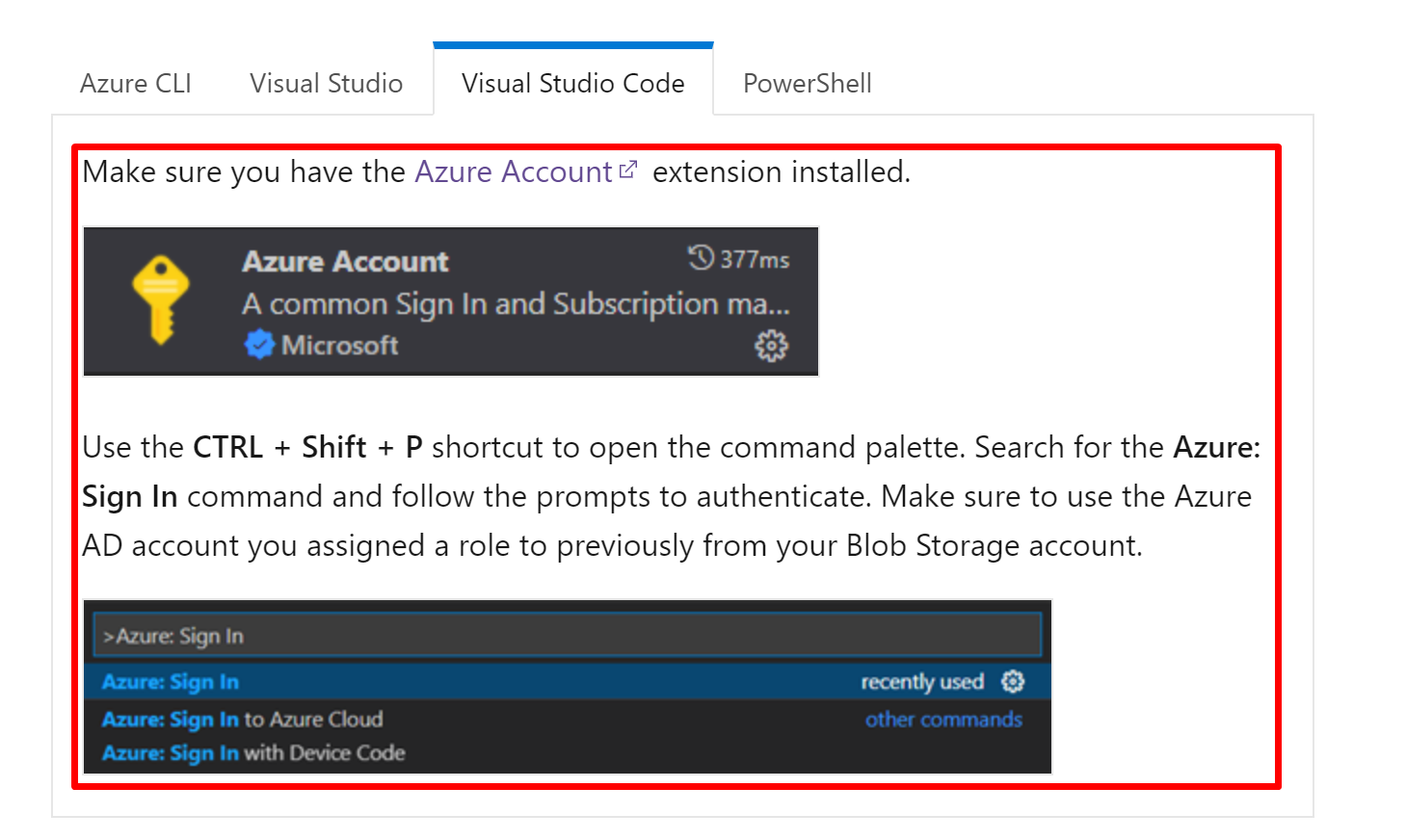
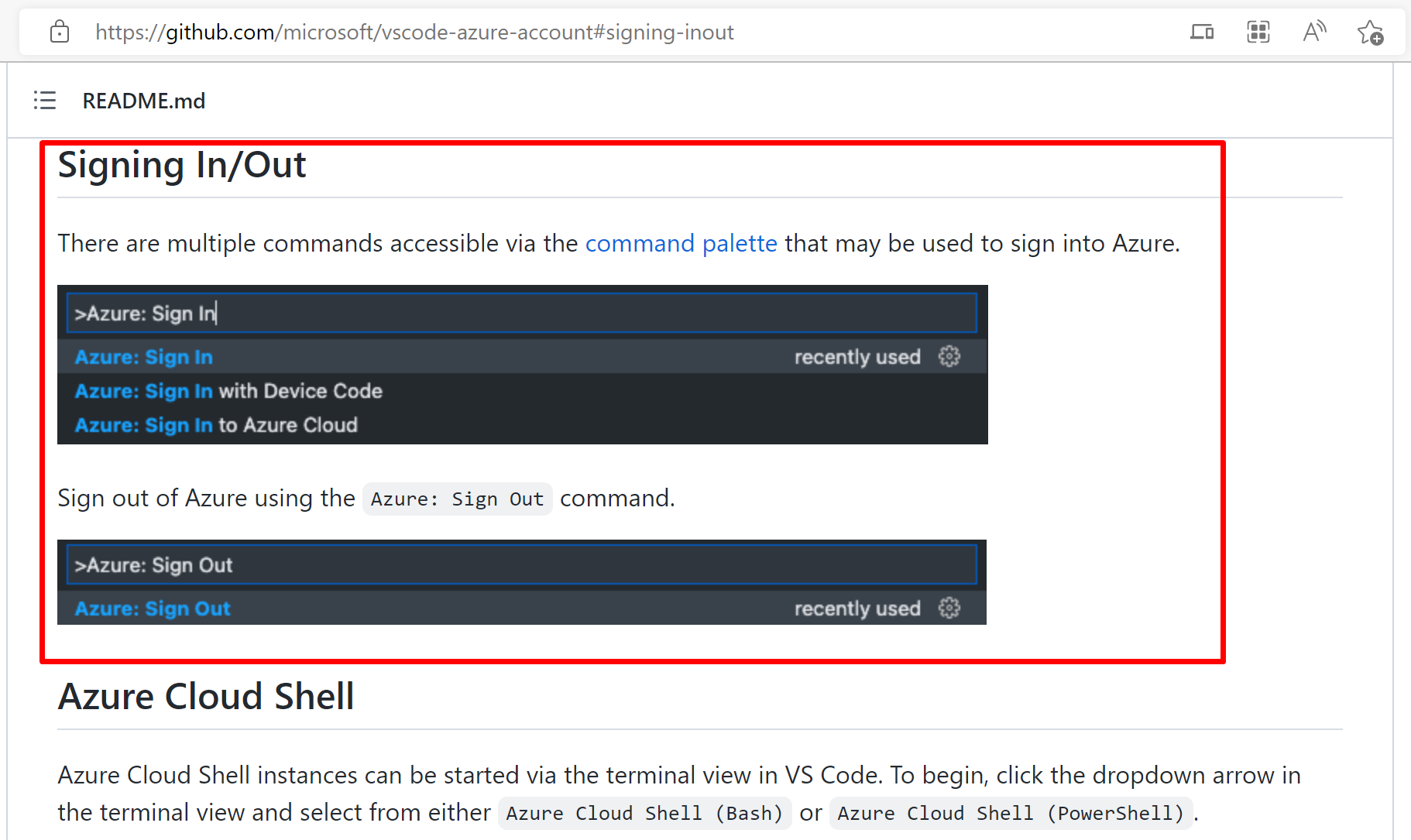
For example, we can use this link instead: https://github.com/microsoft/vscode-azure-account#signing-inout Otherwise, it's possible that the login step changed, and we (migration guide maintainer) will not know that. |
|
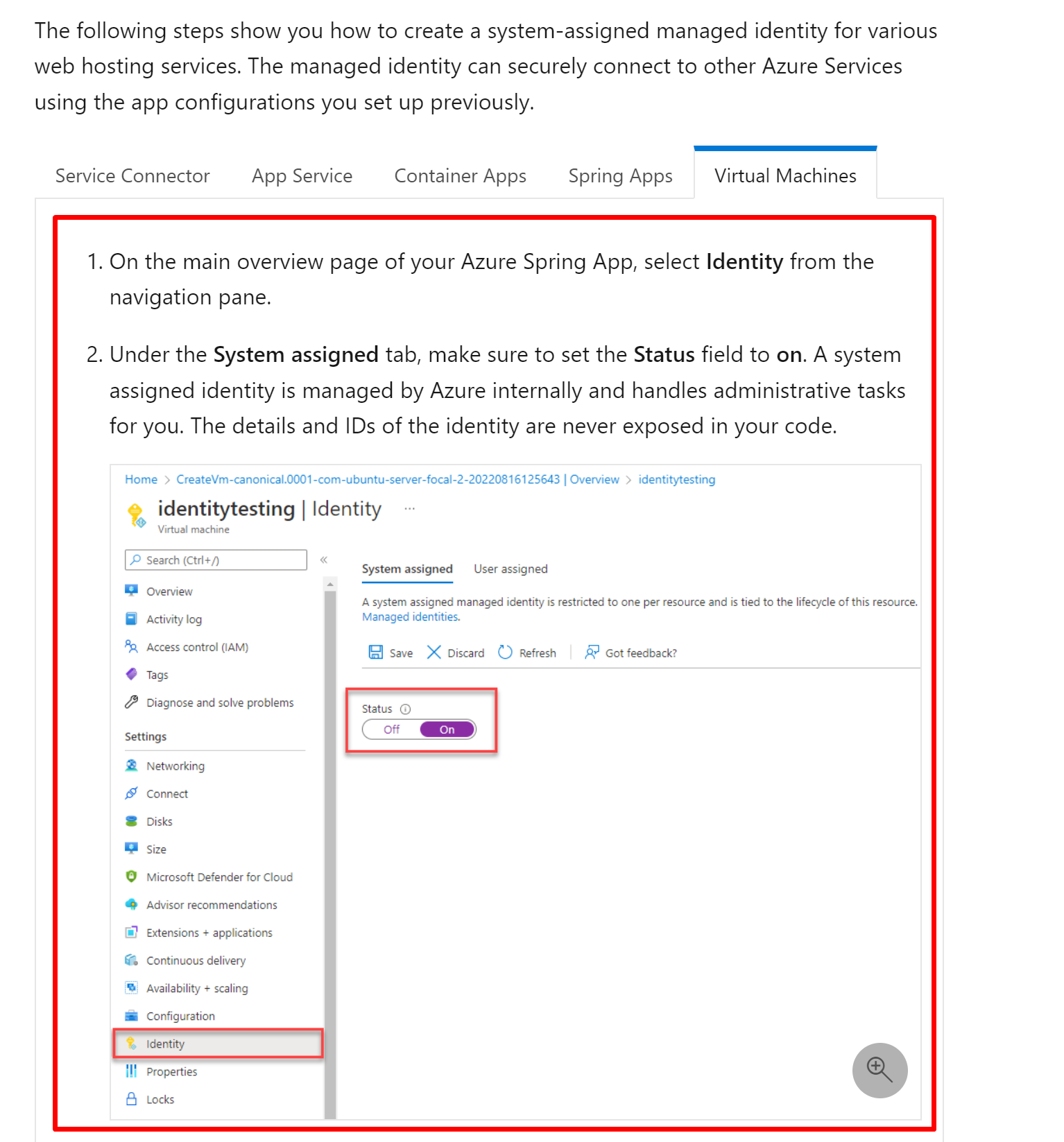
This content can be replaced by this link: https://learn.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/qs-configure-portal-windows-vm#enable-system-assigned-managed-identity-on-an-existing-vm |
|
|
===========
Screenshots: |
|
I have finished go-through related documents. Closing this issue. Next step: #31346 |
|
The #30800 (comment) is tracked with microsoft/spring-cloud-azure#1037. |



















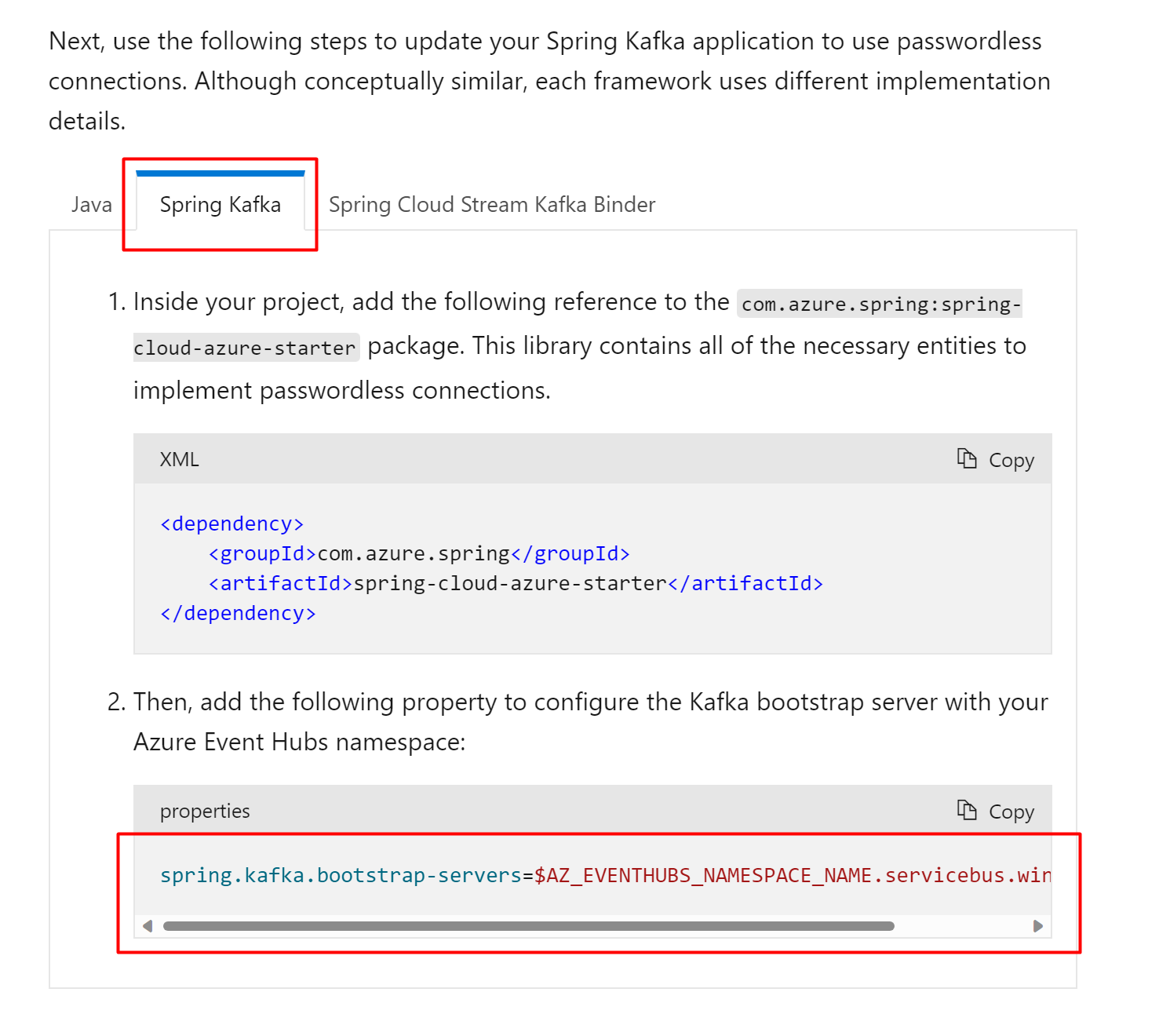

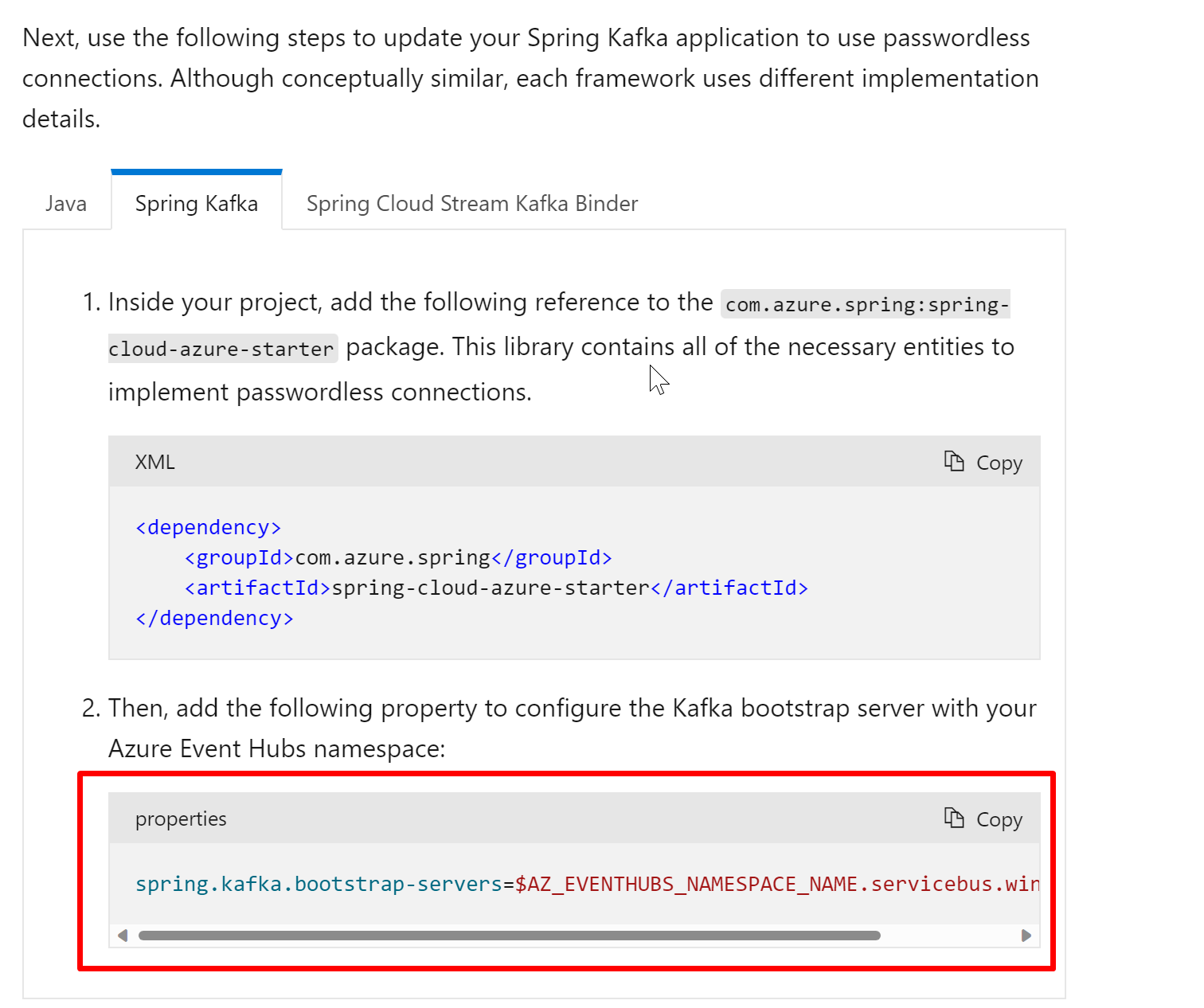
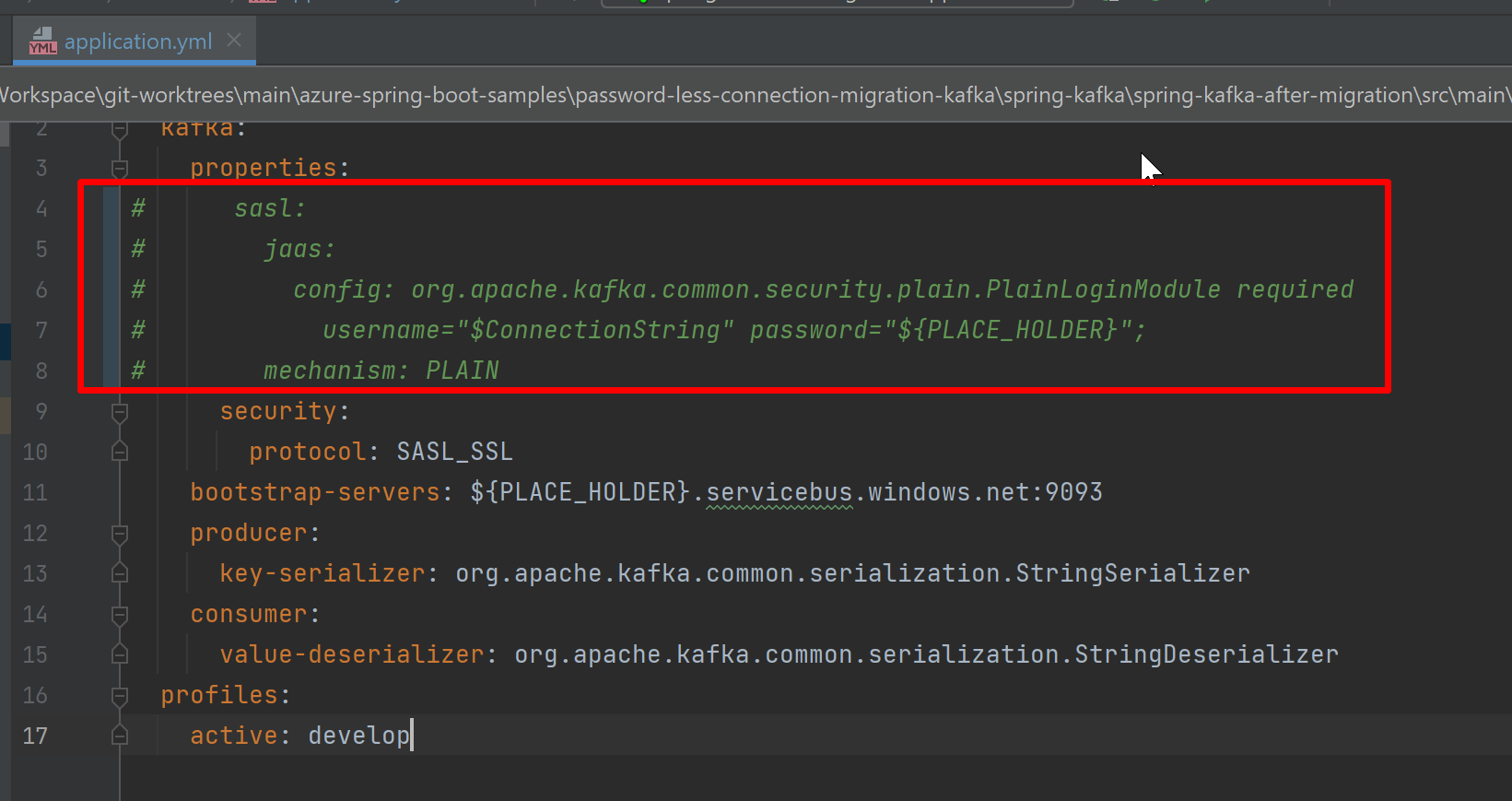























Context
With all Kafka passwordless-doc being finished, we should check the readability and correctness of those docs.
Goal
Go through the docs in the below PRs to make sure it is easy to understand and execute, and all the commands are correct and operational.
The text was updated successfully, but these errors were encountered: