-
Notifications
You must be signed in to change notification settings - Fork 5
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[VULNERABILITY] Authenticated file upload vulnerability - [leading to shell command execution] #27
Comments
|
Hey there, Thanks for reaching out and bringing this issue to my attention. This issue initially seemed like a self-attack to me when I was first writing the code, but now I am convinced that an innocent authenticated user could potentially upload the file. I have identified two to three possible ways to reproduce this issue, including using .htaccess, the PHP runtime configuration, and the file extension checking. I have tested all these methods, and they all worked for me. However, I'm unsure about the best approach or whether they will work on every installation. The extension checking mechanism will prevent any type of file without extension from being uploaded, including text files. The file extension will be the same as the file name if it has no extension. So, unless the file name is in the list of whitelisted extensions, it will never be uploaded. $extension = explode( '.', $basename );
$extension = strtolower( end( $extension ) );
$extensions = $this->_l( 'media_extension',
array(
// Extensions whitelist
)
);
if ( ! in_array( $extension, $extensions ) ) {
$msg = 'File extension not allowed';
return false;
}However, I have considered files without extensions and thought about checking if a file is a plain text file and allowing the upload that way. $extension = explode( '.', $basename );
$extension = strtolower( end( $extension ) );
$extensions = $this->_l( 'media_extension',
array(
// Extensions whitelist
)
);
if ( ! in_array( $extension, $extensions ) ) {
if ( $extension !== $basename || 'text/plain' !== $type ) {
$msg = 'File extension not allowed';
return false;
}
}Disabling script execution using AddHandler cgi-script .php .pl .jsp .asp .sh .cgi
Options -ExecCGI |
|
The one with extension whitelist looks fine. If the user indeed wants to upload codes, an extension changing mechanism can be induced. For example: script.php to script.php.txt or script_php.txt |
Do you agree with the "checking if a file is a plain text file and allowing the upload" way? |
|
Yes, I agree with that. It's a good idea. |
Good 👍 One more thing, can you please take a look and see if any of the default allowed MIME types should be removed? |
|
Alright 👍 |
A PHP file with random bytes on the first line will get uploaded. // file.php
asdfghj34567yhjndtetstetlhbkERFVj65678;
<?php system($_GET['cmd']); ?>This file will bypass mime type checks. I think this file is categorized as |
|
Yeah, the extension checking will also fix that. Anyway, below are the extension to be whitelisted: |
|
The whitelist looks clean. 👍 |
Overview
By default, an authenticated user cannot upload a PHP file due to mime type checks but it can be bypassed by adding a GIF header at the beginning of the PHP file. "finfo" considers a PHP file with GIF header as a GIF file instead of PHP.
The above PHP code can be uploaded, bypassing mime type checks.
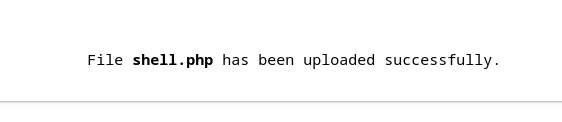
Command execution
Possible fix
Add a file extension checking mechanism to prevent upload of PHP file ..etc
The text was updated successfully, but these errors were encountered: