-
Notifications
You must be signed in to change notification settings - Fork 50
5. Detecting Shellcode Instructions
SHAREM can be used to detect suspicious sequences of instructions in both PE files and “raw” samples of assembly code. This is done purely through static analysis and without the use of emulation. These results can also be used to enrich the disassembly, so even these found will also show up as comments in the disassembly of the shellcode. Additionally, when SHAREM generates reports, it will generate a small, representative excerpt of disassembly for this particular instruction.
While occasionally coincidental, these sequences of instructions possible could indicate malicious sections of code within the sample. Some may or may not be related to shellcode, if found in a PE file. Not all may be known to a causal analyst, so identifying what these instructions mean – rather than having them be cryptic, unknown features – is another pragmatic feature. When analyzing a sample, the user should typically enter this menu, choose the desired types of instructions to search for, then execute the search. Next, the user can display and save all discovered code snippets via the Print Menu accessible via p from the main menu.
SHAREM is currently able to detect these types of instructions:
- PUSH RET – a technique that pushes an address onto the stack and immediately returns to it. This technique can be used to obfuscate API calls or navigate to different portions of shellcode. A PUSH RET is functionally equivalent to a JMP, and this can also be obscured by having junk instructions in between the push and the ret. Shellcode often uses this technique, and additionally malware also often uses it as a means to transition to the shellcode.
- CALL POP – a technique used by shellcode to self-locate using the return address put on the stack by the CALL instruction. It is a necessity that shellcode of complexity perform self-location, so it know where it is process memory.
- FSTENV – another self-location technique, this time using an FPU instruction in conjunction with the FSTENV instruction.
- Syscalls – SHAREM can detect when syscalls are executed by the program. This is often an indication of malicious activities – normally WinAPI calls would be used instead. When detecting syscalls through this method in either shellcode or PE files, our normal emulation is not used. This uses a fairly accurate, but more lightweight custom emulation, and while not perfect, it can be accurate, and it is a great way to identify syscalls in a large PE file, for instance. With shellcode, the full emulation is the better option. (This is done by default when emulating it).
- Heaven’s Gate – an obfuscation technique used to transition from 32-bit mode to 64-bit mode. This can break some debuggers.
- PEB Walking – The PEB is a structure that contains a large amount of information about the current running process. If a sample is traversing this structure, it is a strong indication of malicious activity. Walking the PEB is a first step before traversing the exports directory. Both of these can be used jointly to covertly obtain runtime addresses of APIs. In essence, this is how all modern Windows shellcode operates to utilize shellcode.
To toggle selections for SHAREM to look for, use the g option then type in the corresponding selections indicated by the text onscreen.
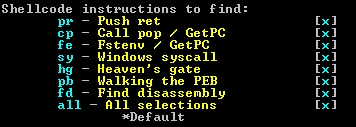
The c option can be used to deselect all options. When ready, the z option can be used to look for all sequences selected. A selection will have x next to it. Afterwards, the r option can be used to clear all discoveries if the user wants to choose different selections instead.
This menu contains advanced options that should usually only be altered when attempting to combat false positives. Each option contains some additional information upon selection to help the user.
The “global settings” option can be used to tweak the amount of disassembly bytes forwards and backwards that SHAREM uses when looking for instruction patterns. Tweaking this can either lower or increase both false and true positives.
The c option refers to the maximum distance between the CALL and POP instructions for the CALL POP type of GetPC pattern. This should generally be left alone.
The p option can be used to select how many unique features must be detected before SHAREM will classify a snippet as PEB Walking. As indicated by the helper text, values below 3 are not recommended due to a much high number of false positives. However, setting this value significantly above 3 may eliminate true positives as well. It is recommend to be left at 3. Values of 5 are the maximum that can be obtained generally, but some will only obtain a 3 or 4, and having a value of 5 would cause a lot to be missed.
The k option simply changes the minimum length of strings to save.