Releases: CrazeeGhost/PS4JbEmu
Releases · CrazeeGhost/PS4JbEmu
PS4 9.00, 10.0x & 11.00 PPPwn Auto Jailbreak using Raspberry Pi
Changes
- #8 Added support for FW 10.0x
Instructions
PS4 Setup
- Go to Settings and then Network
- Select Set Up Internet connection and choose Use a LAN Cable
- Choose Custom setup and choose PPPoE for IP Address Settings
- Enter
ps4for both PPPoE User ID and PPPoE Password - Choose Automatic for DNS Settings and MTU Settings
- Choose Do Not Use for Proxy Server
Pi Setup
- Download and burn image onto a 2GB or larger micro SD card
- Navigate to the boot partition/drive on the SD card and change contents of
pppwn-cpp.txtas follows -
| Target FW | File Contents |
|---|---|
| 9.00 | 900 |
| 10.0x | 1000 |
| 11.00 | 1100 |
- Insert the micro SD card into a Raspberry Pi
- Optional - Connect the Pi to your WiFi (easiest using
sudo raspi-config). Then power if off. - Download and extract SiSTR0's GoldHEN v2.4b17.2
- Copy
goldhen.binto the root of an exFAT formatted USB drive - Plug the USB Drive into a USB port on your PS4
- Connect the Pi to your PS4 via an Ethernet cable and power on both devices.
- Wait for notifications confirming GoldHEN was loaded. This should happen within 2-3 minutes depending on how many attempts are required for that instance. If nothing happens within 5 minutes of boot up, I recommend restarting both the Raspberry Pi and the PS4.
Notes
- This Jailbreak is for PS4 running software versions 9.00, 10.0x & 11.00 only
- Tested on Raspberry Pi 3 Model B
- If you followed step 4 above, your PS4 will have internet access which may result in your PS4 updating it's system software. You have been warned.
- After the first successful load of GoldHEN, you do not need to repeat steps 5 through 7 for subsequent runs on the same PS4
- Auto updates the pppwn_cpp exploit binary at device boot (if internet available)
- PS4 can access internet if Pi is connected to WiFi and only after successful Jailbreak
- No need to restart Pi if Re-Jailbreaking after PS4 was shutdown/restarted (PS4 must have stayed off for at least 30 seconds)
- Handles exceptions when PS4 crashes during exploit or if the exploit itself halts or hangs
Credits
PS4 9.00 & 11.00 PPPwn Auto Jailbreak using Raspberry Pi
Changes
- Auto update the pppwn_cpp exploit binary at device boot (if internet available)
- PS4 can access internet if Pi is connected to WiFi and only after successful Jailbreak
- No need to restart Pi if Re-Jailbreaking after PS4 was shutdown/restarted (PS4 must have stayed off for at least 30 seconds)
- Better handling of exception when PS4 crashes during exploit
- Handle if exploit halts or hangs
Instructions
PS4 Setup
- Go to Settings and then Network
- Select Set Up Internet connection and choose Use a LAN Cable
- Choose Custom setup and choose PPPoE for IP Address Settings
- Enter
ps4for both PPPoE User ID and PPPoE Password - Choose Automatic for DNS Settings and MTU Settings
- Choose Do Not Use for Proxy Server
Pi Setup
- Download and burn image onto a 2GB or larger micro SD card
- If exploiting FW 9.00, navigate to the boot drive on the SD card and change contents of
pppwn-cpp.txtto900 - Insert the micro SD card into a Raspberry Pi
- Optional - Connect the Pi to your WiFi (easiest using
sudo raspi-config). Then power if off. - Download and extract SiSTR0's GoldHEN
- Copy
goldhen.binto the root of an exFAT formatted USB drive - Plug the USB Drive into a USB port on your PS4
- Connect the Pi to your PS4 via an Ethernet cable and power on both devices.
- Wait for notifications confirming GoldHEN was loaded. This should happen within 2-3 minutes depending on how many attempts are required for that instance. If nothing happens within 5 minutes of boot up, I recommend restarting both the Raspberry Pi and the PS4.
Notes
- This Jailbreak is for PS4 running software versions 9.00 and 11.00 only
- Tested on Raspberry Pi 3 Model B
- If you followed step 4 above, your PS4 will have internet access which may result in your PS4 updating it's system software. You have been warned.
- After the first successful load of GoldHEN, you do not need to repeat steps 5 through 7 for subsequent runs on the same PS4
Credits
PS4 9.00 & 11.00 PPPwn Auto Jailbreak
Changes
- Using the C++ version of the PPPwn exploit
- Added support for FW 9.00
Instructions
PS4 Setup
- Go to Settings and then Network
- Select Set Up Internet connection and choose Use a LAN Cable
- Choose Custom setup and choose PPPoE for IP Address Settings
- Enter anything for PPPoE User ID and PPPoE Password
- Choose Automatic for DNS Settings and MTU Settings
- Choose Do Not Use for Proxy Server
Pi Setup
- Download and burn image onto a 2GB or larger micro SD card
- If exploiting FW 9.00, navigate to the boot drive on the SD card and change contents of
pppwn-cpp.txtto900 - Insert the micro SD card into a Raspberry Pi and connect it to your PS4 via an Ethernet cable
- Download and extract SiSTR0's GoldHEN
- Copy
goldhen.binto the root of an exFAT formatted USB drive - Plug the USB Drive into a USB port on your PS4
- Power On the PS4 and the Raspberry Pi
- Wait for notifications confirming GoldHEN was loaded. This should happen within 5 minutes depending on how many attempts are required for that instance. If nothing happens within 10 minutes of boot up, I recommend restarting both the Raspberry Pi and the PS4.
Notes
- This Jailbreak is for PS4 running software versions 9.00 and 11.00 only
- Tested on Raspberry Pi 3 Model B
- After the first successful load of GoldHEN, you do not need to repeat steps 5 & 6 for subsequent runs on the same PS4
Credits
PS4 11.00 Auto PPPwn Jailbreak
Instructions
PS4 Setup
- Go to Settings and then Network
- Select Set Up Internet connection and choose Use a LAN Cable
- Choose Custom setup and choose PPPoE for IP Address Settings
- Enter anything for PPPoE User ID and PPPoE Password
- Choose Automatic for DNS Settings and MTU Settings
- Choose Do Not Use for Proxy Server
Pi Setup
- Download and burn image onto a 2GB or larger micro SD card
- Insert the micro SD card into a Raspberry Pi and connect it to your PS4 via an Ethernet cable
- Download SiSTR0's GoldHEN
- Copy goldhen.bin to the root of an exFAT formatted USB drive
- Plug the USB Drive into a USB port on your PS4
- Power On the PS4 and the Raspberry Pi
- Wait for notifications confirming GoldHEN was loaded. This should happen within 5-20 minutes depending on how many attempts are required for that instance. If nothing happens within 20 minutes of boot up, I recommend restarting both the Raspberry Pi and the PS4.
Notes
- This Jailbreak is for PS4 running software version 11.00 only
- Tested on Raspberry Pi 3 Model B
- After the first successful load of GoldHEN, you do not need to repeat steps 4 & 5 for subsequent runs on the same PS4
- SSH username is
piand password ispppwnin case you need to access the Pi
Credits
PSFree Exploit for faster, more stable JailBreak
Local PS4 9.00 Jailbreak Host with USB emulation
This project is aimed at setting up a local web host, with USB emulation, on select Raspberry Pi boards that can be used to exploit and jailbreak PS4 consoles running firmware version 9.00. Raspberry Pi Zero W / Pi Zero 2 W / Pi4 B are eligible boards as they support a USB on-the-go (OTG) gadget mode and eliminate the need to manually insert and remove the USB stick required in the exploit process. This project is implemented on a clean Raspberry Pi OS (Debian) install which makes it easier to repurpose the Pi to run additional applications and services on it.
Developed and Tested on Raspberry Pi 4 B but should work on Pi Zero W / Pi Zero 2 W / Pi4 B
Benefits
- Clean Raspberry Pi OS install - easy to setup the Pi for other purposes as you desire
- Easily update exploit, GoldHen and payload files from the web interface
- One device for local web server and USB emulation
- One USB cable is sufficient to power the Pi and emulate USB
- You can leave the Pi permanently connected to the PS4. No need not to remove and plug in a USB stick to run explolit
Setup - Easy Method
- Write the image provided in the releases to an SD card (using program like Pi Imager or Rufus)
- Insert the SD card into the Raspberry Pi
- For Pi Zero W & Pi Zero 2W, connect the USB marked Pi USB port to PS4. Be sure to use a cable that supports data transfer
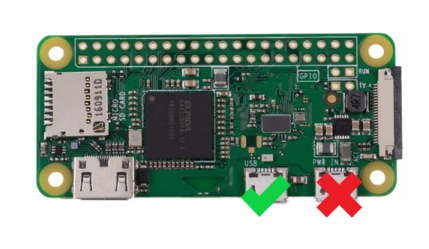
- For Pi4 B, connect a USB C cable from Pi to PS4
- Power up the PS4. This should also boot up your Pi
- Use
raspi-configto expand the filesystem to the capacity of your SD card - On the PS4 go to Browser and visit http://<ip.address.of.your.pi>/ps4
- Click on the GoldHen button for the version you want to exploit with
a. A popup will be thrown saying USB emulation started and wait for ps4 pop up

b. Once the USB message disappears, Click ok
c. Gold Hen will load automatically - If you need SSH access, username is
piand password isps4free
Setup - Advanced Method
- Install a clean Raspberry Pi OS image to an SD card (Developed and tested on Debian Bullseye)
- Enable USB Gadget Mode on the Pi
a. Adddtoverlay=dwc2,dr_mode=peripheralto the[all]section inside/boot/config.txt - Prevent the Pi from automatically becoming a USB gadget on every boot
a. Addsudo /sbin/modprobe -r g_mass_storageto/etc/rc.local - Install and setup
lighttpdandPHP - Enable fast cgi module for lighttpd
a.sudo lighttpd-enable-mod fastcgi fastcgi-php
b.sudo systemctl reload lighttpd.service - Configure
/var/www/html/ps4as the document root directory for the exploit app (vialighttpdconfigs) - Clone or download the source code from this repo
a.cd /home/pi
b.git clone https://github.com/CrazeeGhost/PS4JbEmu.git - Allow the webserver user to run modprobe as root without password
a. Addwww-data ALL=(ALL) NOPASSWD: /sbin/modprobeto your sudoers file using thevisudocommand - Make the web app accessible to the webserver (will not work if you did not follow the directory strcture in step 8)
a.cp /home/pi/PS4JbEmu/updateHost.sh /home/pi
b.sudo chmod 755 /home/pi/updateHost.sh
c.sudo /home/pi/updateHost.sh - (Optional) Enable auto-updates via cron
a.sudo crontab -e
b.*/30 * * * * /home/pi/updateHost.sh
Credits
- Kameleonre_ - Porting PSFree Exploit
- Sleirsgoevy – Webkit, Offline Activator
- Chendochap – KeExploit
- PaulJenkin – Inspiration for USB Emulation
v1.1
Minor tweaks and README updates.
v1.0
Added note to expand filesystem