New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
invalid_origin error in OpenID Connect flow with Google after enabling self-service registration #1018
Comments
|
Questions:
It may also be helpful to see a HAR file of the sequence you recorded to see which redirects are occurring in order. I was able to set up our Google account as an OIDC provider and it worked fine. It sounds like the HTTP origin header is changing based upon the user's locale, or maybe even the browser or browser mode (incognito). If you are configured to validate the origin, then it seems like you would just have to configure each possible origin. I don't see anything that is jumping out at me as far as changes in this validation. |
|
Answers:
|
|
Ok, for fun - can you try disabling self service in stage and see if that removes the symptom? This may give us a clue as to what may be causing the change. |
|
Confirmed, with self-service registration disabled I can no longer reproduce the issue. |
|
I'll update the title and description of the issue in light of this being related to self-service registration, and not the version upgrade. |
|
Ok, good to know. I am unable to recreate so far, I tried with a normal configuration, and then also with self service registration enabled. Can you also attempt to recreate with self service enabled using the stock (default) theme, this will tell us if we have a problem in general, or something is different in your themed template than the default one that may be causing the issue. |
|
I've tried with the default theme but I still get the invalid_origin error. |
|
Ok, so the work around is to do one of two things:
I'll have to dig into that path to see what would be different. More to come. |
|
So far I've been unable to recreate. In your screenshot/gif I see a few redirects after you log into Google, please outline the entire flow with each redirect or provide a HAR file of the recreate so I can ensure we are testing the same workflow. Thanks! |
|
I think I figured it out. Note: Cannot reproduce in Brave, but I can reproduce in Chrome. This is because Brave is omitting the Here is what is happening: Works: Self Service Registration Enabled : false
Does not work: Self Service Registration Enabled : true
So, technically the failure is correct - this origin is not registered and thus we cannot validate it. However - perhaps we are being a bit too aggressive here - the Origin validation which is optional - likely should only be verified when it is an unsolicited request and the user has not yet completed authentication. This means we should validate the origin (if configured) on requests to The plan is to re-work when we perform origin validation so that this validation behavior does not change based upon the self service configuration setting. Also - as a side note, validating the origin is not that important in my opinion. Unless you're in a legit browser, modifying or removing this header is not out of the question, and if the header is omitted we cannot validate the origin. So this validation can be bypassed relatively easily. This is why I was originally unable to recreate using Brave, it had removed the header so the Origin configuration was not being used. The one current use case where this configuration is valuable, is if you need to load any of the themed pages in an IFRAME, in this case we use the Authorized Origin configuration to know when to omit the |
|
Thanks for the detailed write-up. |
|
Was this ever fully resolved? I'm seeing the following in error logs, and I'm assuming it's the same issue: Do we have to add each of these URLs as valid origins to each application? Is it safe to just not use authorized request origin URLs at all? |
invalid_origin errors start occurring after self-service registration is enabled
Description
We have configured a OpenID Connect Identity Provider for Google. We choose this option over the built-in Google provider as it causes a pop-up window to open. This has been working fine for us. However, after having enabled self-service registration on our staging environment we started noticing errors, with users redirected to our authorization page with the following querystring arguments:
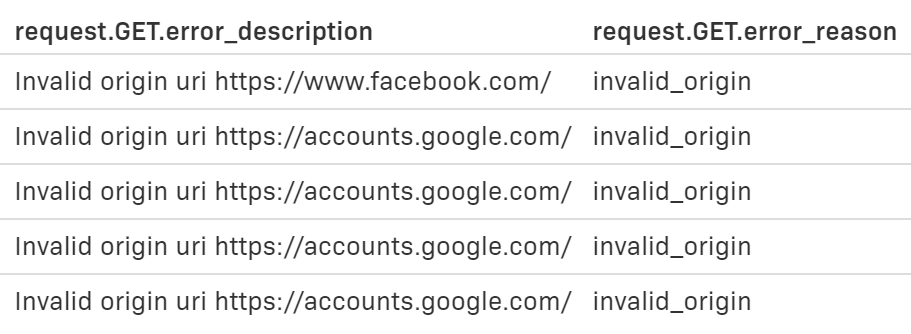
?error=invalid_request&error_reason=invalid_origin&error_description=Invalid+origin+uri+https%3A%2F%2Faccounts.google.com%2F...At first, we modified our Application in FA, adding https://accounts.google.com to the list of authorized request origin URLs. Later, we found that when logging in with our @grid.is Google accounts in a freshly opened Incognito window, we'd be redirected to https://accounts.google.is (notice the .is top-level-domain) during the authentication flow and get the same error, unless we also add https://accounts.google.is to the list. I have tried adding https://accounts.google.* to the list but that doesn't appear to work. I therefore see only two options:
a) Empty out the list of authorized request origin URLs to allow all
b) Manually add an entry for every top-level-domain that Google has
I'm not particularly fond of either. Is there anything else we can do?
Below is a screen capture of an authentication flow that ends with an error. If you pay attention to the address bar, you'll notice a brief visit to https://accounts.google.is/accounts/SetSID right before the user is redirected back to us.

The text was updated successfully, but these errors were encountered: