Assert WDACConfigIntegrity
Assert-WDACConfigIntegrity
[-SaveLocally]
[-Path <FileInfo>]
[-SkipVersionCheck]
[<CommonParameters>]This cmdlet scans all of the relevant files in the WDACConfig module's folder and computes their SHA2-512 hashes.
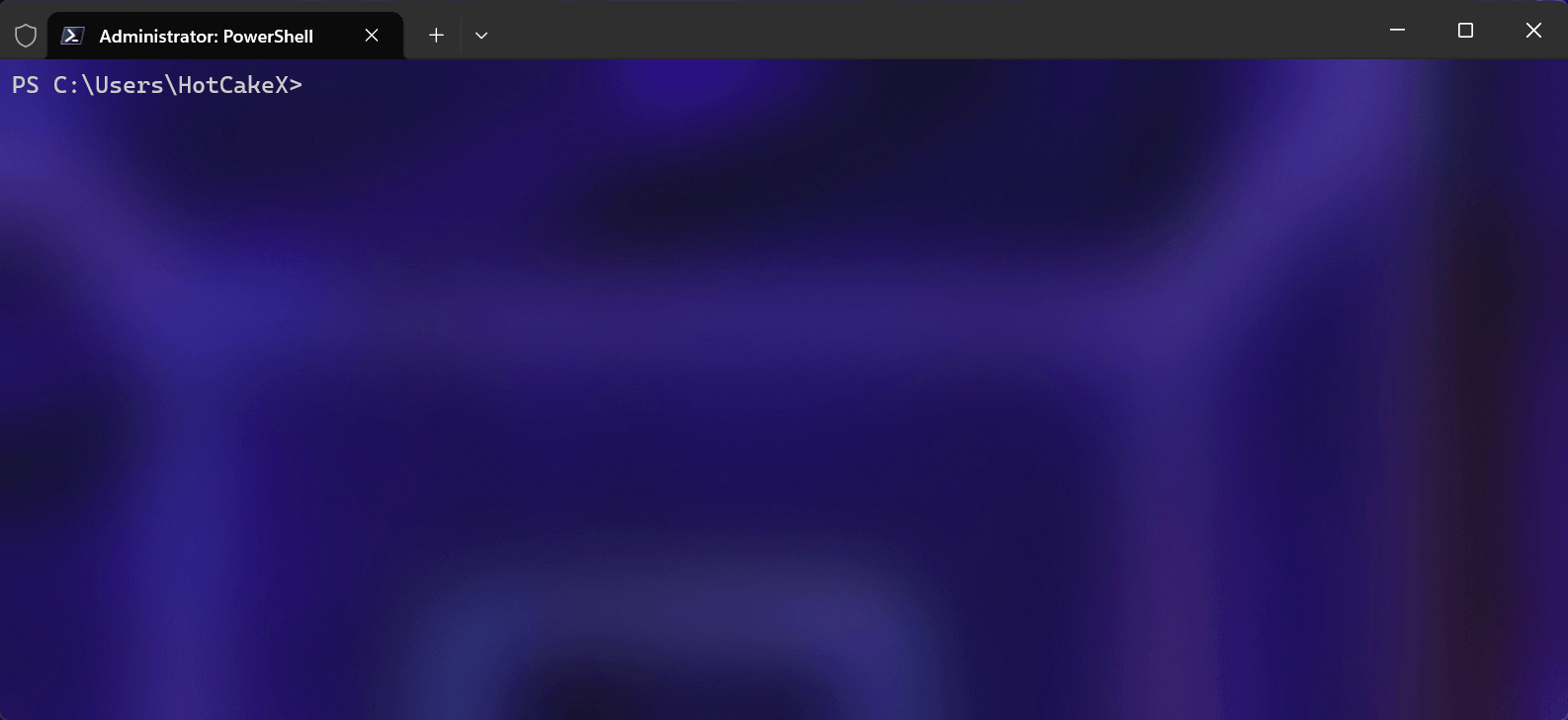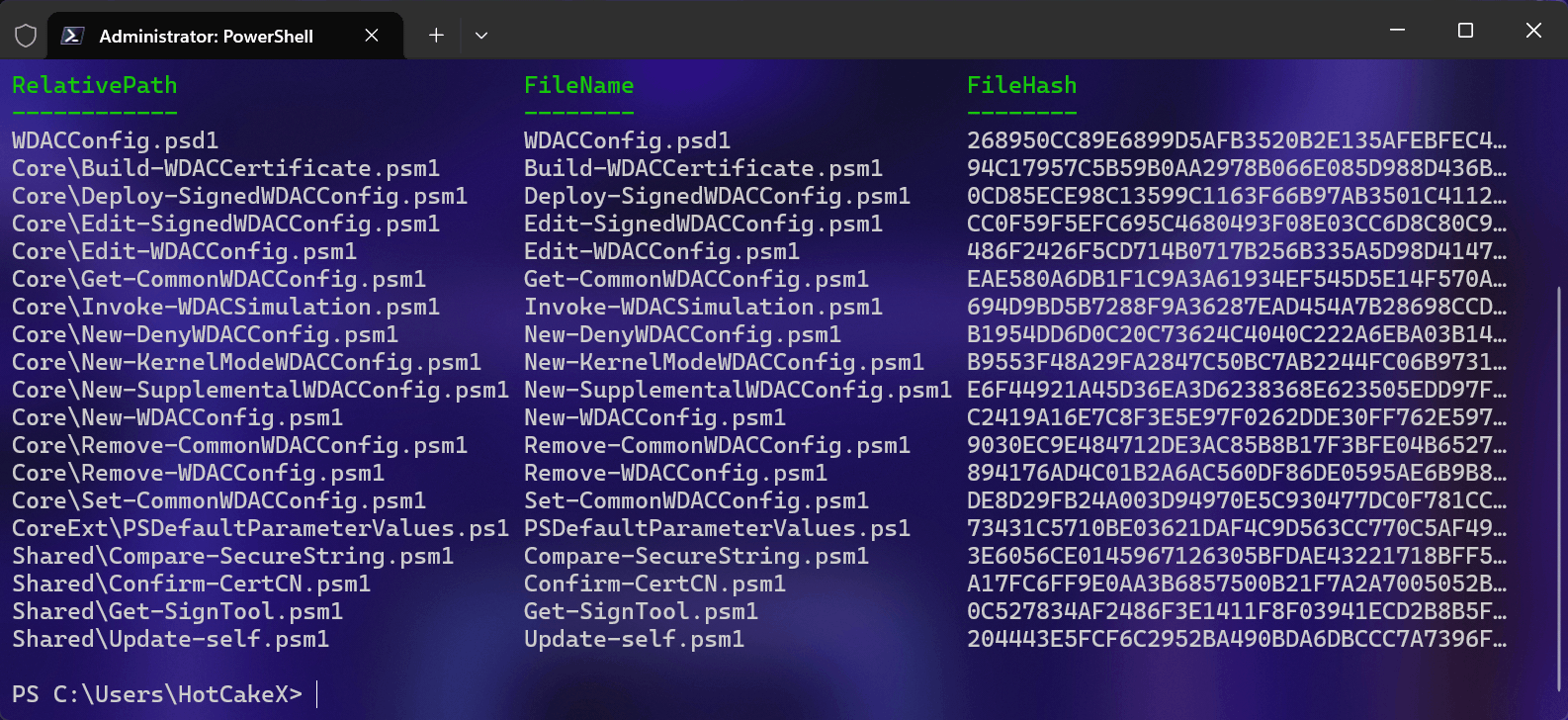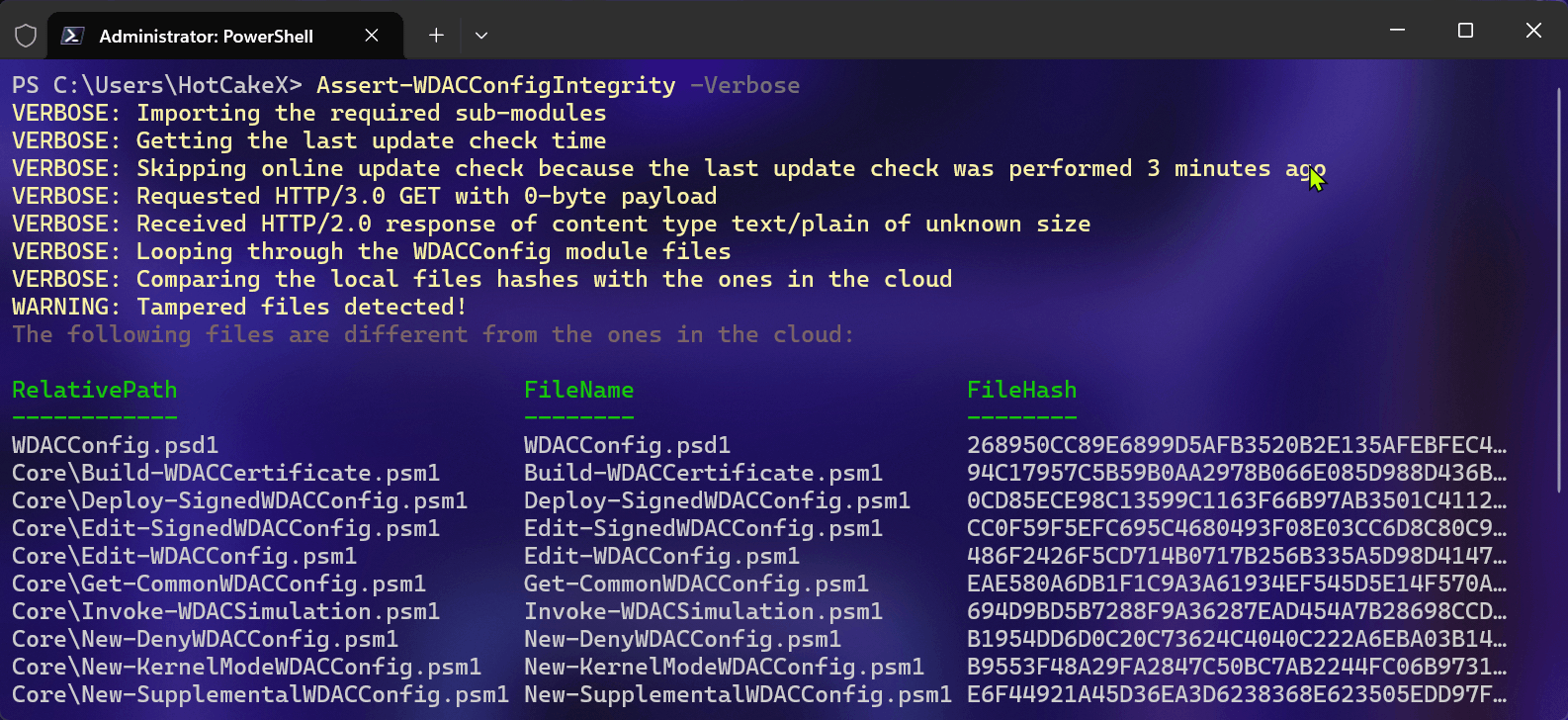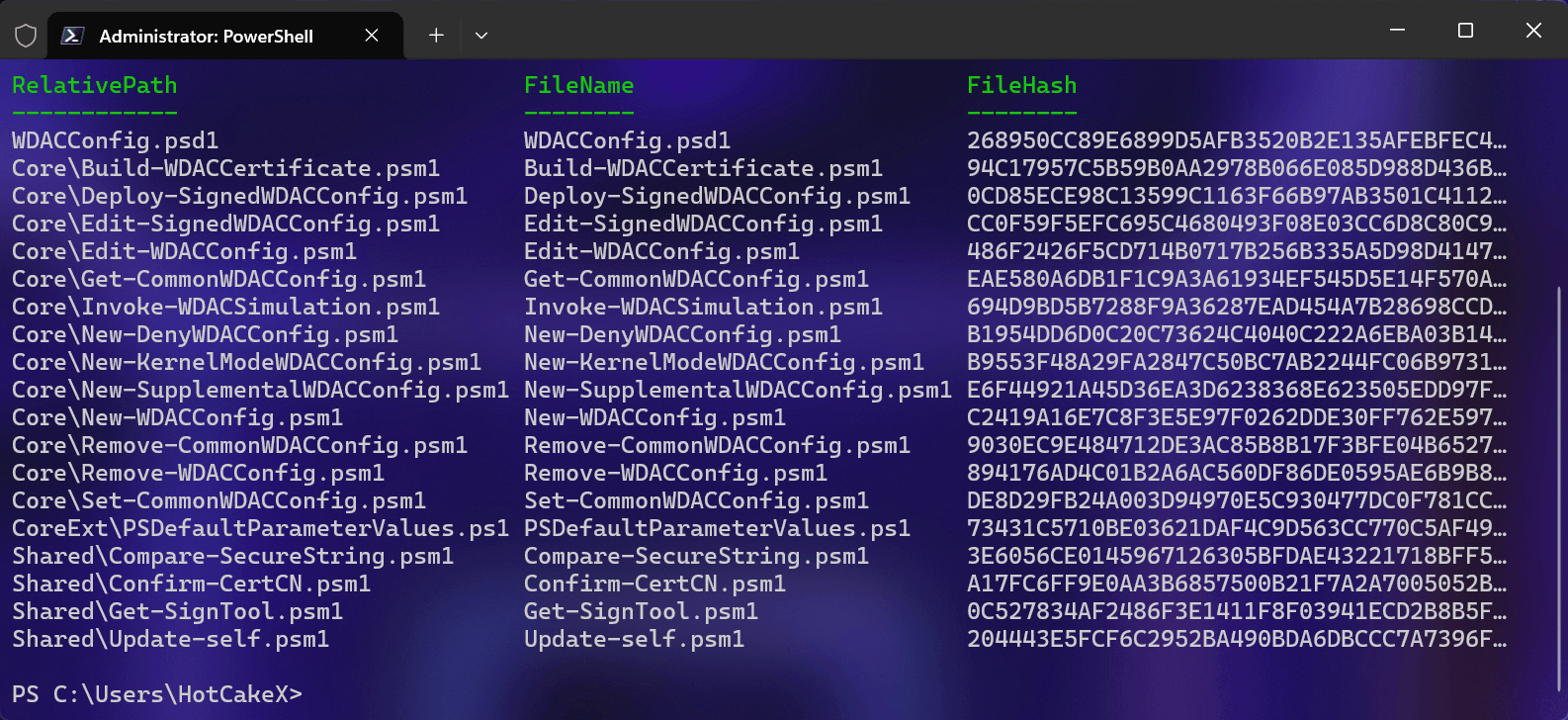
Then it downloads the cloud CSV file from the GitHub repository and compares the hashes of the local files with the ones in the cloud.
By doing so, you can ascertain that the files in your local WDACConfig folder are identical to the ones in the cloud and devoid of any interference.
If there is any indication of tampering, the outcomes will be displayed on the console.
This parameter is used to generate hashes of the final module's files prior to publishing them to the GitHub. This parameter shouldn't be used.
| Type: | SwitchParameter |
|---|---|
| Position: | Named |
| Default value: | None |
| Required: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Can define a different path for the Hashes.csv file. This parameter shouldn't be used.
| Type: | FileInfo |
|---|---|
| Position: | Named |
| Default value: | Module's Root Directory |
| Required: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
The WDACConfig module comprises of .ps1 and .psm1 files that bear the cryptographic signature of my local certificate authority's (CA) certificate. The module incorporates mechanisms to automatically ascertain the integrity of the module files and prevent any unauthorized modifications. The module manifest, .psd1 file, on the other hand, lacks a signature due to the installation error that arises from the PowerShell gallery when it is signed with a self-signed certificate.
The public key of the certificate used to sign the module files can be obtained from here.
-
 New-WDACConfig
New-WDACConfig
-
 New-SupplementalWDACConfig
New-SupplementalWDACConfig
-
 Remove-WDACConfig
Remove-WDACConfig
-
 Edit-WDACConfig
Edit-WDACConfig
-
 Edit-SignedWDACConfig
Edit-SignedWDACConfig
-
 Deploy-SignedWDACConfig
Deploy-SignedWDACConfig
-
 Confirm-WDACConfig
Confirm-WDACConfig
-
 New-DenyWDACConfig
New-DenyWDACConfig
-
 Set-CommonWDACConfig
Set-CommonWDACConfig
-
 New-KernelModeWDACConfig
New-KernelModeWDACConfig
-
 Get-CommonWDACConfig
Get-CommonWDACConfig
-
 Invoke-WDACSimulation
Invoke-WDACSimulation
-
 Remove-CommonWDACConfig
Remove-CommonWDACConfig
-
 Assert-WDACConfigIntegrity
Assert-WDACConfigIntegrity
-
 Build-WDACCertificate
Build-WDACCertificate
-
 Test-CiPolicy
Test-CiPolicy
-
 Get-CiFileHashes
Get-CiFileHashes
-
 ConvertTo-WDACPolicy
ConvertTo-WDACPolicy
-
 Introduction
Introduction
-
 WDAC for Lightly Managed Devices
WDAC for Lightly Managed Devices
-
 WDAC for Fully managed device - Variant 1
WDAC for Fully managed device - Variant 1
-
 WDAC for Fully managed device - Variant 2
WDAC for Fully managed device - Variant 2
-
 WDAC for Fully managed device - Variant 3
WDAC for Fully managed device - Variant 3
-
 WDAC for Fully managed device - Variant 4
WDAC for Fully managed device - Variant 4
-
 WDAC Notes
WDAC Notes
-
 How to Create and Deploy a Signed WDAC Policy
How to Create and Deploy a Signed WDAC Policy
-
 Fast and Automatic Microsoft Recommended Driver Block Rules updates
Fast and Automatic Microsoft Recommended Driver Block Rules updates
-
 WDAC policy for BYOVD Kernel mode only protection
WDAC policy for BYOVD Kernel mode only protection
-
 EKUs in WDAC, App Control for Business, Policies
EKUs in WDAC, App Control for Business, Policies
-
 WDAC Rule Levels Comparison and Guide
WDAC Rule Levels Comparison and Guide
-
 Script Enforcement and PowerShell Constrained Language
Script Enforcement and PowerShell Constrained Language
-
 How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control
How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control
-
 Create Bootable USB flash drive with no 3rd party tools
Create Bootable USB flash drive with no 3rd party tools
-
 Event Viewer
Event Viewer
-
 Group Policy
Group Policy
-
 How to compact your OS and free up extra space
How to compact your OS and free up extra space
-
 Hyper V
Hyper V
-
 Overrides for Microsoft Security Baseline
Overrides for Microsoft Security Baseline
-
 Git GitHub Desktop and Mandatory ASLR
Git GitHub Desktop and Mandatory ASLR
-
 Signed and Verified commits with GitHub desktop
Signed and Verified commits with GitHub desktop
-
 About TLS, DNS, Encryption and OPSEC concepts
About TLS, DNS, Encryption and OPSEC concepts
-
 Things to do when clean installing Windows
Things to do when clean installing Windows
-
 Comparison of security benchmarks
Comparison of security benchmarks
-
 BitLocker, TPM and Pluton | What Are They and How Do They Work
BitLocker, TPM and Pluton | What Are They and How Do They Work
-
 How to Detect Changes in User and Local Machine Certificate Stores in Real Time Using PowerShell
How to Detect Changes in User and Local Machine Certificate Stores in Real Time Using PowerShell
-
 Cloning Personal and Enterprise Repositories Using GitHub Desktop
Cloning Personal and Enterprise Repositories Using GitHub Desktop
-
 Device Guard and Virtualization Based Security in Windows
Device Guard and Virtualization Based Security in Windows
-
 Clean Source principle, Azure and Privileged Access Workstations
Clean Source principle, Azure and Privileged Access Workstations
-
 How to Securely Connect to Azure VMs and Use RDP
How to Securely Connect to Azure VMs and Use RDP
-
 Basic PowerShell tricks and notes
Basic PowerShell tricks and notes
-
 Basic PowerShell tricks and notes Part 2
Basic PowerShell tricks and notes Part 2
-
 Basic PowerShell tricks and notes Part 3
Basic PowerShell tricks and notes Part 3
-
 How To Access All Stream Outputs From Thread Jobs In PowerShell In Real Time
How To Access All Stream Outputs From Thread Jobs In PowerShell In Real Time
-
 PowerShell Best Practices To Follow When Coding
PowerShell Best Practices To Follow When Coding
-
 How To Asynchronously Access All Stream Outputs From Background Jobs In PowerShell
How To Asynchronously Access All Stream Outputs From Background Jobs In PowerShell
-
 Powershell Dynamic Parameters and How to Add Them to the Get‐Help Syntax
Powershell Dynamic Parameters and How to Add Them to the Get‐Help Syntax