New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
OAuth 2.0 authentication issues after 2022.7.0 #5670
Comments
|
Thanks for the report @batista16 , this is related to my PR #5571 previous implementation became I can revert this and make it continue to fail quietly but I still want to dig a little deeper, can you explain why your oauth2 access token request doesn't return a hash? Perhaps you can anonymise the request timeline so i can see the structure, and the console logs around the time this error shows up. |
|
I'm not sure I understand what you mean. For us it wasn't failing at all, it was working fine to retrieve a token. If it helps, the authentication server is not our own implementation, we use keycloak as an identity broker. How can I check the request timeline on insomnia? |
|
I see oauth2 failures from insomnia failing to give the response_type parameter on implicit grant I know this from logs on the oauth service. Like @batista16, Im not sure how I can see the request flow for an implicit grant opening some popup window. I cannot see the redirect flow in this pop up or its dev tools. The view/hot keys only open the dev tools on the primary app window. @jackkav I doubt a revert of your error case related to an empty hash is the root cause. Im guessing the hash is empty because the error from the oauth service is being hidden/dropped/ or their impl of oauth isnt providing the information. |
|
Hello, I am also getting an error after the most recent update. When attempting to get a token I get: |
|
I see the same error after upgrading to v2022.7.2. |
|
Hi, I am using oauth2 with grant type "Resource Owner Password Credentials" and am getting as well errors since 2022.7.2 when using the "Refresh Token" function. It works fine for me when I clear the tokens and fetch new ones. In the refresh token request the authorization header seems to be missing. |
|
OAuth2 isn't working for me on 2022.7, though it does on 2022.6. The process all looks normal until Insomnia requests I can provide comparison oauth timelines for the two if useful (though I'd rather not post them publicly here!) They aren't very obviously different. Could it be an issue with how 2022.7 extracts the code from the redirect URL in the little browser window? |
|
P.S. My grant type is Authorization Code - so it may not be the same issue as those listed above, but it certainly works fine in 2022.6.0. |
|
Same problem on my end, with v2022.7.2, worked perfectly before with the same requests on v2022.7.0. Grant type is Implicit, Oauth2 implementation is Azure AD. Note : I do not have a redirect URL configured in my request. |
|
So my problem was that I didn't have the oAuth2 checkbox enabled. Once that was done it started working. It would probably be a nice enhancement to disable the token fetching when that was off. Or generate a better error message. Thanks! I love Insomnia and use it every day! Thanks for making it better! |
|
@quentinsf Thanks for the report we did find a logical error when handling codeVerifier and codeChallenge which is fixed in #5691 thanks for your patience. |
|
@srikanthnd @batista16 and anyone hitting the specific In order to help us debug this, try to check on the Dev tools console logs to see what
Pay close attention to the The |
Just wanted to add my thanks to others' : Insomnia's a great project and we're finding it very helpful and enjoyable to use - many thanks for all your efforts! |
|
@filfreire - thank you for the quick response. Here is the screen shot as you requested. And by the way I agree to what @quentinsf said :-) ... I feel that Insomnia is a great tool too I don't see any error logs in the console apart from what is seen in the screen shot. I hope this helps all of us... |
|
@srikanthnd thats an awesome screenshot, I know exactly what to do, we just need to show the error. |
|
@batista16 @srikanthnd @Dremor @tylerhjones - we're merging soon #5703 which will make the need for redirect url returned by server non-mandatory - so things should go back to normal for you folks after an upcoming release. |
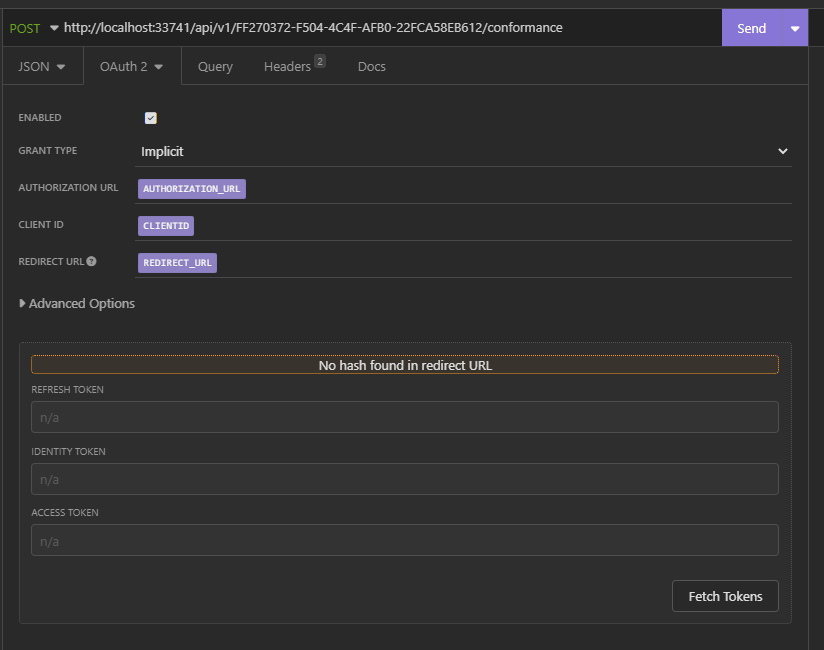




Hi, our oath authentication stopped working after the latest update. I've downloaded v2022.7.0 and v2022.7.2 and on the latest I get this message:
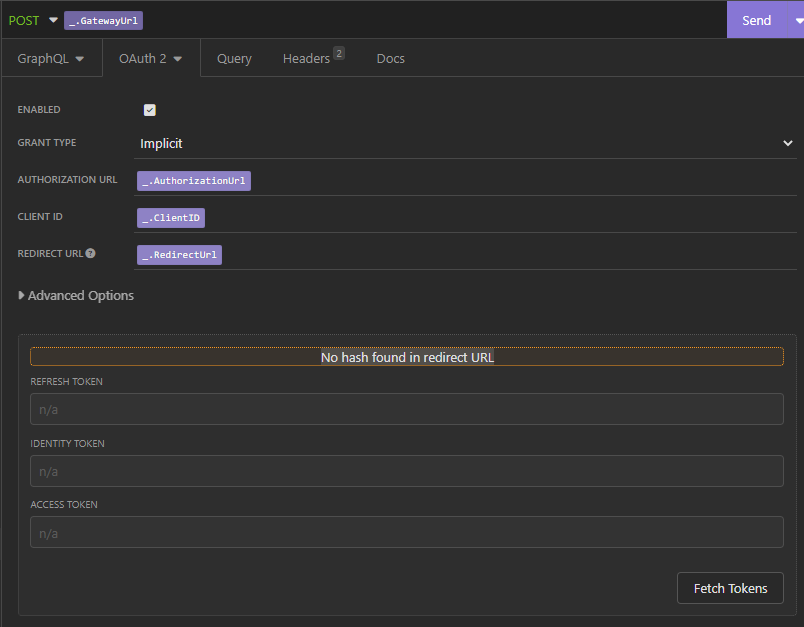
While on v2022.7.0 it works just fine.. (same collection, same env)
I'm not sure what more information can I give you without sharing sensitive information.
is this a bug or an undocumented breaking change?
The text was updated successfully, but these errors were encountered: