New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Custom SAN is not trusted by Chrome #76
Comments
|
There is a bug in |
|
Can you provide sample certificate that doesn’t work? BTW, does first name in SAN list work? |
|
First SAN does not work in Chrome as well. |
|
Ok, can you send me certificates from first example, where you had 1 and 2 names (as in initial screenshots)? Also, can you paste code you used to create |
|
Files attached (there is single certificate with CN and two SANs on the 1st screensthot). |
|
So is there any other workaround we could use in short term? Or there is no chance to modify SANs for now at all? Thx. in advance. |
|
Sorry, I was extremely busy last week. I will get back to you soon. |
|
I made a quick check and my initial suspect was correct. The idea is that when The extension is malformed when length of SAN extension is odd number. In this case, you need to add a fake name with odd length (considering that overal length won't exceed 127 bytes). This will fix the extension. The workaround you tried didn't work, because the name length is even number, thus total SAN extension value is still odd. That is, if you create SAN extension (any extension is affected), check its length. Say, this will work. I tried to contact Microsoft on this long-time bug, but no progress and unlikely will be fixed. |
|
This workaround seems to work, thank you! |
|
Although, this one is old, but I eventually found a way to work around |
* upgraded .NET version to 4.7.2 * added support for KeyBasedRenewal flag in CES URL * added missing Convert.ToInt32 method on authentication conversion to string * added missing KeyBasedRenewal bit encoding * updated CES URL encode to be URI-compliant (spaces replaced with %20) * ipmproved and updated CRL text dump * version bump * updated casing and xml-doc comments * addressed #49 * added another missing enum value * code style * Added ToString() implementation which returns * addressed #51 * implemented #50 * added basic support for new Microsoft extension 1.3.6.1.4.1.311.25.2 (from KB5014754). * addressed PKISolutions/PSPKI#76 in backing library * renamed class and made it static
|
Fixed in v4.0.0 |
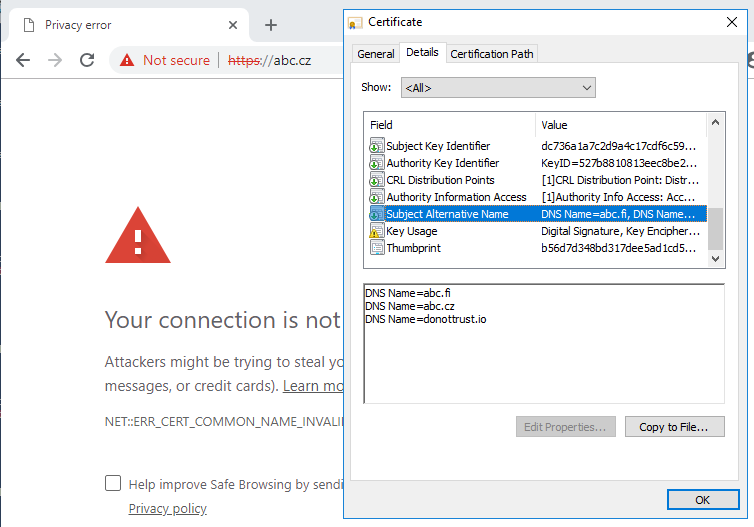
Certificate issued with SAN modified by "$Request | Set-CertificateExtension -Extension $SAN" is trusted by Edge and IE, but is not trusted by Chrome.
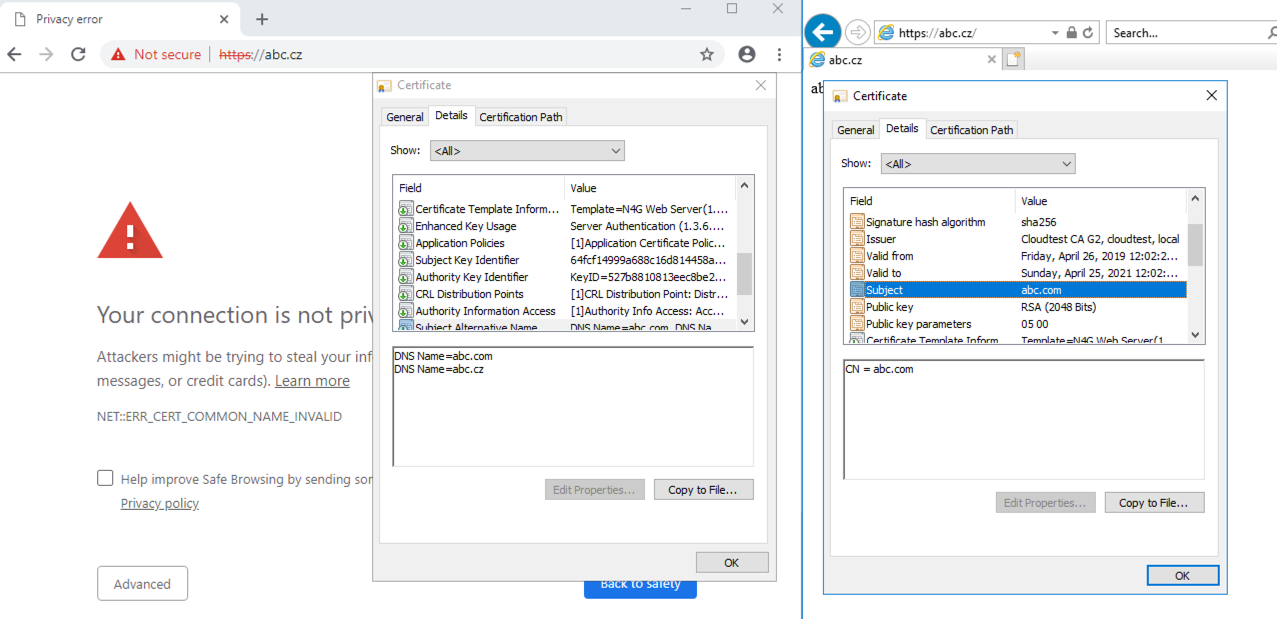
Error is "NET::ERR_CERT_COMMON_NAME_INVALID".
Same error for version 3.4.1.0 and 3.2.7.0
The text was updated successfully, but these errors were encountered: