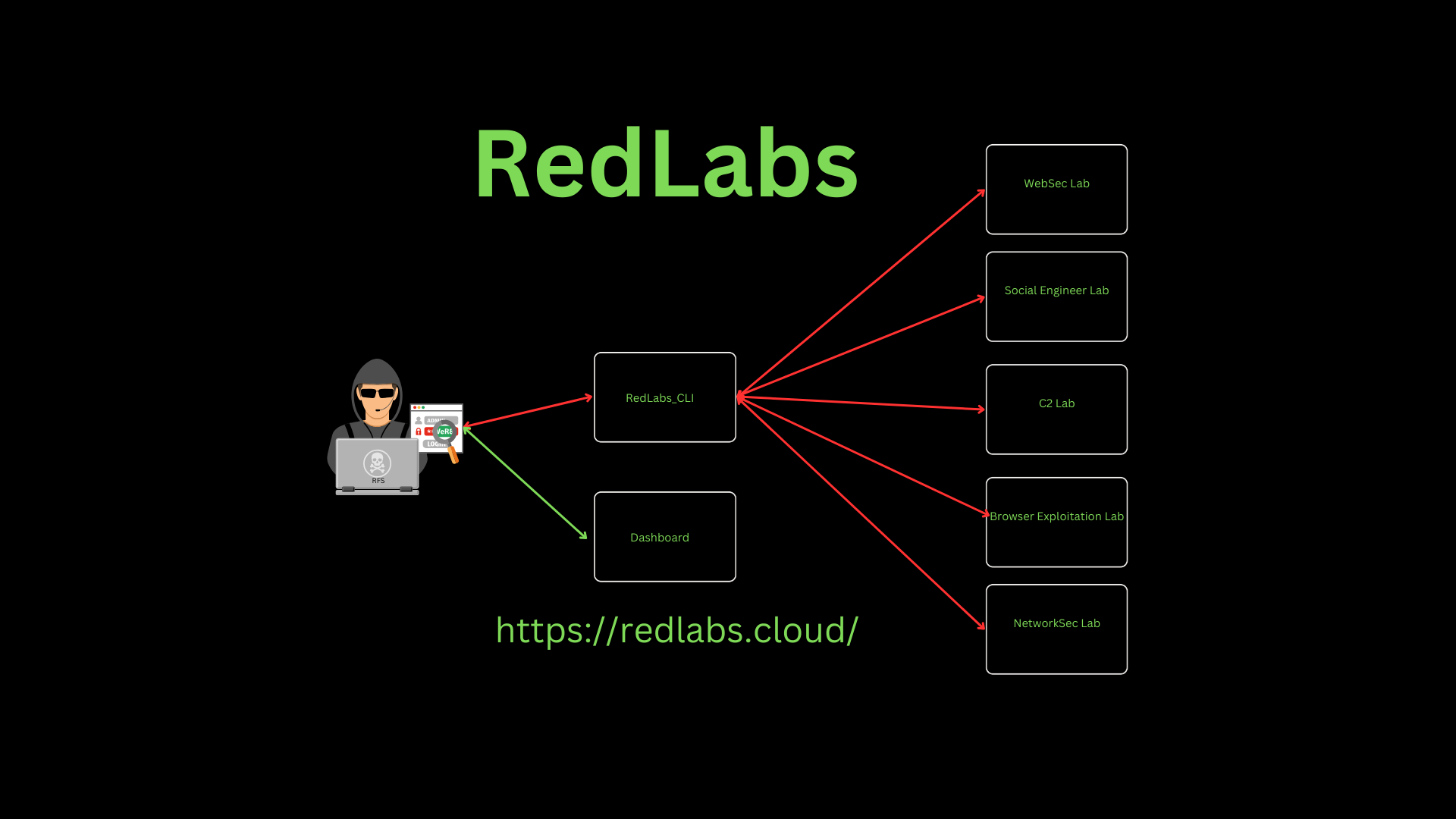
This repository provides resources and tools for building and managing efficient cyber ranges specifically designed for red team training.
A cyber range is a simulated environment that mimics real-world networks and systems. Red teams utilize cyber ranges to practice offensive security techniques, test attack methodologies, and refine their skills in a safe and controlled environment.
This repository can contain various resources depending on your specific setup and goals. Here are some potential inclusions:
- Deployment Scripts: Scripts to automate the deployment of cyber range environments within cloud providers or on-premises infrastructure. (e.g., scripts using tools like Terraform or Ansible)
- Scenario Templates: Pre-built scenarios simulating real-world attack vectors and objectives for red teams to practice against.
- Vulnerable Machines: Vulnerable system images or configurations that can be deployed within the cyber range for red teams to exploit.
- Blue Team Tools: Tools and resources to simulate blue team activity within the cyber range, providing a more realistic training experience. (e.g., Security Information and Event Management (SIEM) logs, pre-configured detection rules)
- Documentation: Documentation outlining best practices for building and managing red team cyber ranges.
The specific instructions for using this repository will depend on the resources included. However, here are some general steps to get started:
- Clone the Repository: Clone this repository to your local machine using Git.
- Review Documentation: Carefully review any included documentation for specific setup instructions and configuration details.
- Deploy the Environment: Follow the provided deployment scripts or instructions to set up the cyber range environment.
- Import Scenarios: Import any pre-built scenarios or customize them to fit your training needs.
- Start Training: Begin red team training exercises within the deployed cyber range environment.
- Command and Control Infrastructure
- Social Engineering LAB
- Browser Exploitation LAB
- Vulnerable Active Directory
- WebApp Security LAB
- Network Security LAB
- Threat Intelligence
- Telecom 4G LAB
- Telecom 5G LAB
We welcome contributions to this repository! If you have any scripts, scenarios, or documentation that can benefit red team cyber range training, feel free to submit a pull request.
Please ensure your contributions adhere to the following guidelines:
Clearly document the purpose and functionality of your contribution. Follow consistent coding style and conventions. Ensure your contribution is well-tested and functional.