-
Notifications
You must be signed in to change notification settings - Fork 2
Getting started
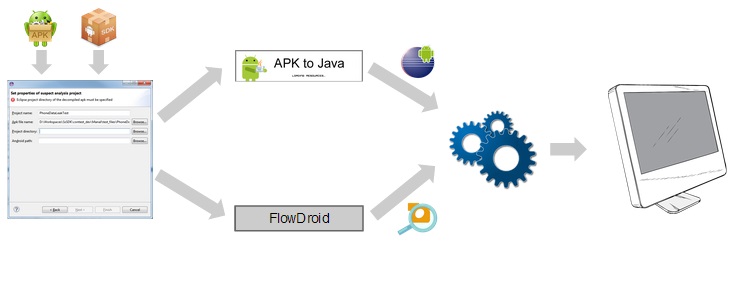
We started implementation of this project for the Digital Forensic Challenge. Manal is the open source Eclipse plugin which automates the process of mobile malware analysis. The work was motivated observing real-world needs of cyber-policemen who wanted to quickly check capabilities of mobile malware and had enough programming skills but were not familiar with mobile technologies. Our plugin extends one of the most popular development environment Eclipse which is naturally used by most technicians who are familiar with programming. Our plugin is easily deployed and features an intuitive interface which provides common-sense information for technicians with basic programming and digital forensic skills. Our plugin hides details of mobile internals and program analysis.
- Process automation of the malware analysis;
- Integration of the command line FlowDroid tool in a popular IDE Eclipse as a plugin.
- Integration of a decompilation tool APKtoJava;
- Integration of Eclipse Java Development Tool (JDT) framework.
- In Eclipse select the Help > Install New Software menu.
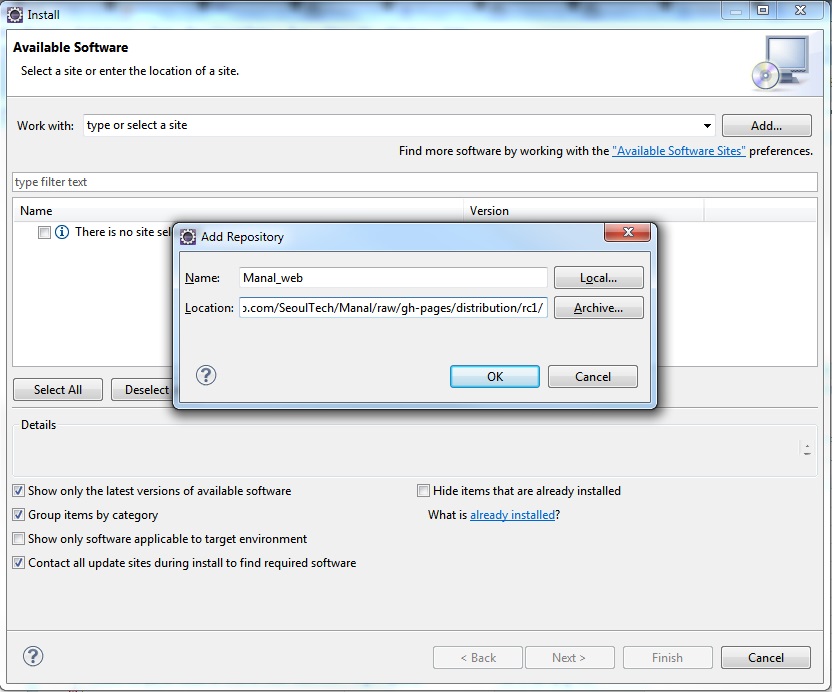
- Click the Add button and input https://github.com/SeoulTech/Manal/raw/gh-pages/distribution/rc1/ in the location field. Input any name you prefer.
- Click Ok and select Suspect Analysis, click the Finish button.
- Read and follow further instructions in the wizard dialogs.
- Agree to GNU license.
-
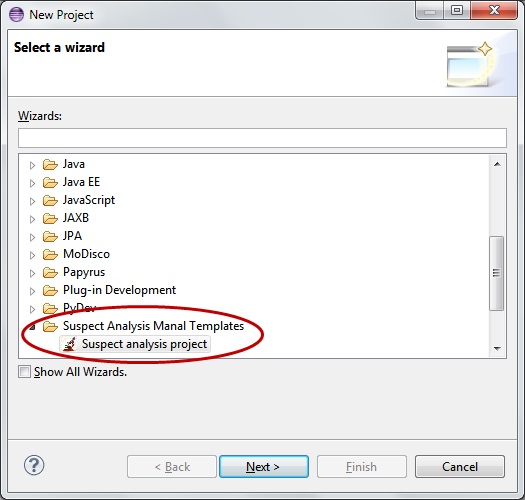
Create a new suspect analysis project: from any perspective in Eclipse open menu File > New > Project. As in the picture below select the Suspect analysis project from the the Suspect Analysis Manal Templates category.
-
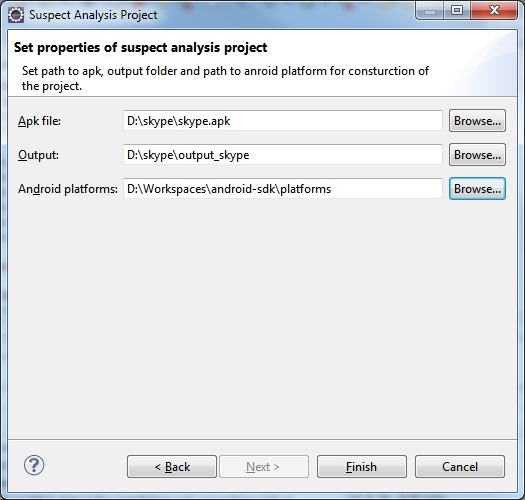
Fill properties for the suspect analysis project: FlowDroid uses apk and the path to android/platforms as input. Apk2Java needs the path to apk and the output directory where it stores results of the decompilation.
-
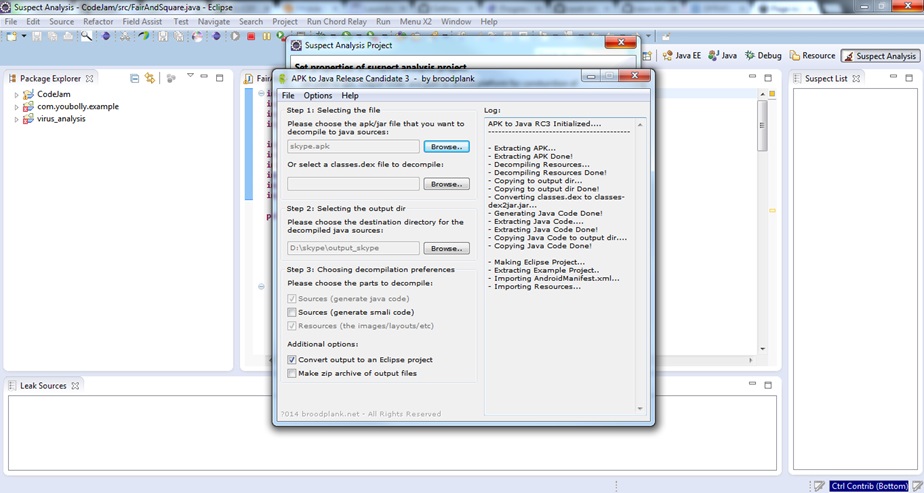
Progress of APKtoJava: shows the progress of the decompilation.
-
Suspect analysis perspective consists of: a package explorer, a suspect list view and a leak sources view. Sinks found by FlowDroid are displayed in suspect list and sources are displayed in leak sources. When a new suspect analysis project is created through the wizard, the decompiled source is added in the package explorer.
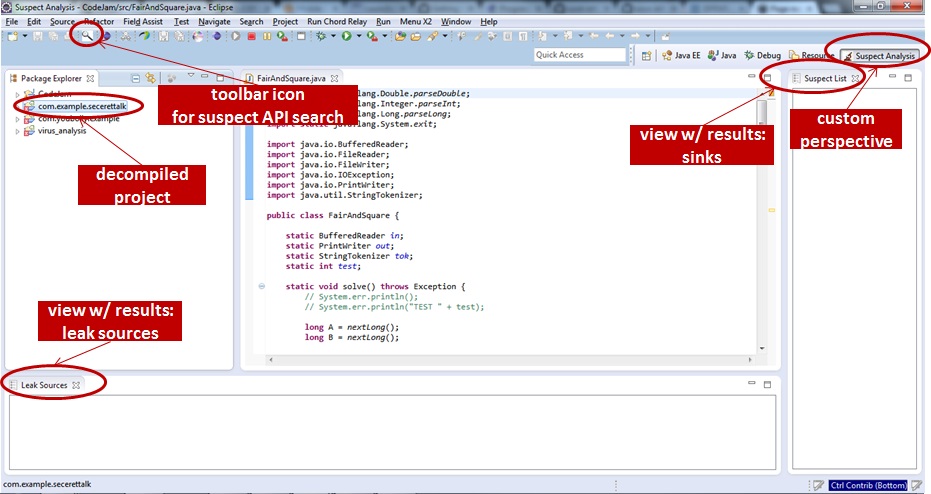
- To extract suspect APIs: call a context menu for the created project in the project explorer and choose the Search suspected API menu which will run FlowDroid. The magnifier button in the toolbar can perform the same action.
-
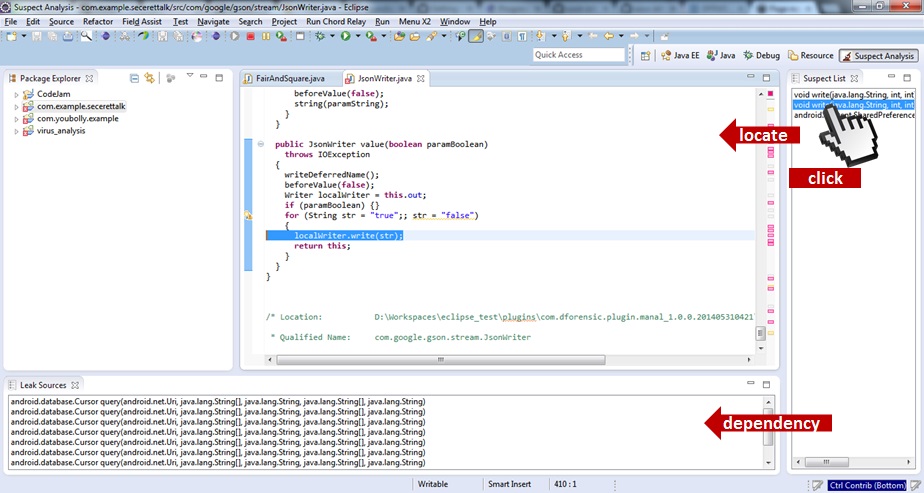
Results: are displayed in the suspect list view. The results are sinks detected by FlowDroid. In the suspect lis view a click of items opens relative source code in the editor and dependent list of leak sources.
Sinks and sources define privacy leaks in mobile malwares (details can be found in research papers of FlowDroid). Sources are Android APIs which access (read) sensitive data in devices and sinks are Android APIs which output (write) data outside of an application's context. Leaks are detected if sources and sinks are connected in terms of data flows.
- If an eclipse project is created in the output folder but a source code is not decompiled, try to create a new suspect analysis project with the output in the same folder (keep previously extracted results in the folder as well).
- If there are no results after the run of Search suspect API, check that you have a version of the android platform same as the target SDK of the analyzing apk.
- Clone and pull https://github.com/SeoulTech/Manal.git.
- In Eclipse open the Plug-in Development perspective and import the /Manal/Manal-plugin project.
- In the context menu of the imported project select Run As > Eclipse Application.
- Show description of malicious capabilities for found suspicious APIs;
- Improve UX;
- Improve stability;
- Explore the usability analyzing databases of malware;
- Research for the extension of FlowDroid precision and performance;
- Add dynamic analysis in an emulator;
- Integrate a platform for collaboration and knowledge sharing among malware analysts.
- Powered by FlowDroid and Apk2Java.
- To Dr. Joshua James for inspiration to participate in the Challenge and for advising.
- To the KITRI Best of the Best center for help to make a team and for the space to collaborate.
- To the Seoul Tech Society for making a creative environment in Korea which stimulates new discoveries.