New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Password for ssh keyfile is being saved in the keychain even when it is told not to do so #299
Comments
|
OK, I can replicate this. Weird one. It correctly skips the saving of the password when you click OK with the checkbox off: - (IBAction)closeSSHPasswordSheet:(id)sender
{
//<snip code>
NSString *thePassword = [NSString stringWithString:[sshPasswordField stringValue]];
// Add to keychain if appropriate
// IT DOESN"T GO INTO THIS BLOCK
if (currentKeyName && [sshPasswordKeychainCheckbox state] == NSOnState) {
SPKeychain *keychain = [[SPKeychain alloc] init];
[keychain addPassword:thePassword forName:@"SSH" account:currentKeyName withLabel:[NSString stringWithFormat:@"SSH: %@", currentKeyName]];
[keychain release];
SPClear(currentKeyName);
}
}
if (!requestedPassphrase) passwordPromptCancelled = YES;
[[answerAvailableLock onMainThread] unlock];
}But it does store it in memory. Need to track down where it's saving... |
|
Ah. I noticed the password was added to the keychain by "OpenSSH", not Sequel Ace: Did some googling and found this tech note:
From the man page(x-man-page://5/ssh_config) for
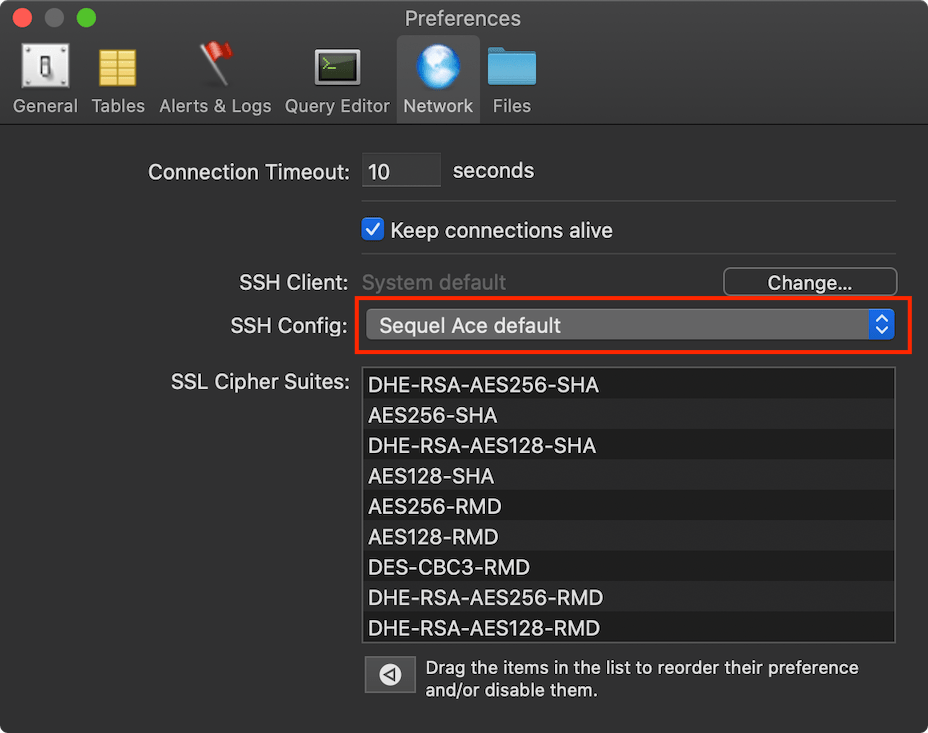
When constructing the ssh command to connect to a server, Sequel Ace looks for a custom config file, else uses the default: // Use a custom ssh config file
NSString *sshConfigFile = [[NSUserDefaults standardUserDefaults] stringForKey:SPSSHConfigFile];
// If the config is not set, use the default one
if (sshConfigFile == nil) {
sshConfigFile = [[NSBundle mainBundle] pathForResource:SPSSHConfigFile ofType:@""];
}So, unless you have specified a custom ssh_config file in Preferences, it uses the Sequel Ace default: Which contains So, @lphilps for a quick fix, use a custom Or edit the file at: For @Sequel-Ace/all - macOS default for |
|
Ah ha! That workaround solved the problem. Many thanks! I had a custom ssh config file I use for command line access, so I added Oddly, both my existing config file, and the default Sequel Ace config file, contain the line:
but it appears this isn't working, which is a bit surprising because openSSH, which I believe implements the ssh* command line utilities, does work with that setting and stores keys into and reads keys from the ssh-agent. Even if I manually add the key to the ssh-agent before running Sequel Ace, it still doesn't find it? Perhaps another Mac App Store Sandbox issue? If there is a way to make that work, like it did in the old Sequel Pro, that would be perfect for me. I'd only have to type my .pem file passphrase once per session, while ensuring that passphrase was never saved anywhere in permanent storage on my Mac. BTW, on a related note, I do not set
in my ssh config file because it seems to totally break the ssh-agent. Keys get stored in the agent, but are never found when a subsequent attempt is made to access the same system. I'll confess I never figured out why. |
Good catch, @jamesstout! Yeah,I think we should set UseKeychain to no in our default ssh config file. Perhaps even we want to remove the option from our default config file and set it to no in our ssh connection setup manually like some of the other config options like retry are (so it's set to no regardless of the user's ssh config file, if we're going to handle sequel Ace storing passwords for key files it seems confusing if they sometimes are saved by openssh regardless of what that checkbox says). |
|
I was curious as to why the Sequel Ace / Openssh combo was not communicating with the ssh-agent on my Mac, so I (finally) investigated a little. Turns out the problem is, once again, related to a Unix Domain socket, similar to the problem in issue #113. Launchd on the Mac is creating a Unix Domain Socket for the ssh-agent at
then it sets the SSH_AUTH_SOCK environment variable in all shells to point to that file. The ssh command uses the environment variable to find the socket and communicate with the ssh-agent, but of course that won’t work for apps running in the Mac App Store Sandbox that can’t open the socket. Sadly, it is not even workable to add an option to launch a file selector to select the socket and store it as a bookmark because the RandomString part of the socket path changes on every system restart. I did figure out a workaround that works for me though. I created a launchd script (adapted from
This runs another copy of ssh-agent (you can run more than one of these on the system at one time) forcing the Unix Domain socket for this instance to be in the Sequel Ace Sandbox, i.e.
Then I created a simple Automator “Run Shell Script” application that contains: Clicking that automator icon will launch of copy of Sequel Ace (without a controlling terminal, which is necessary to get ssh to work properly) that communicates with the second ssh-agent instance and everything functions the way it is supposed to. Using the Automator script has some drawbacks, in particular you can’t launch more than one copy of Sequel Ace, and I am now storing 2 completely separate copies of keys in memory, but … Sure seems like the Sandbox restriction on opening Unix Domain Sockets is a huge limitation. |
I think this should belong on a different issue? May be useful info for #346 and #113 however. |
|
Reopening until 2.2.0 is actually released |

Description
When I create a connection to a db that requires going through an ssh tunnel, I use the ssh tab on the connection screen and enter the ssh host & user, then browse to the appropriate ssh key for the bastion host. All good.
I always ensure all my ssh keys are encrypted to implement a form of 2-factor authentication. Even if somebody steals the key or manages to get access to my laptop, the .pem file is useless unless you know the password used to encrypt it. Still all good.
So when I use Sequel Ace to connect to such a server, it pops up a dialogue asking me for the password for the .pem file. Included in that dialogue is a checkbox saying "Remember password in my keychain" (see attached screenshot). Even if I leave that box unchecked, the password I enter is stored in the keychain and is then automatically used in the future by Sequel Ace, even across reboots, removing the "2-factor" protection.
What the old Sequel Pro used to do in this situation was to use the MacOS ssh-agent to store the key in memory, allowing reuse during the current login session, without ever storing it to disk, and thus requiring one to re-enter the key on every new login (or after a reboot). Do apps in the MAS Sandbox have access to the ssh-agent? If so, can Sequel Agent be changed to use that interface to store ssh keys?
Just to be clear, I feel it is fine for Sequel Ace to store the db passwords in the keychain, just not the ssh keys that give access to the bastion hosts that allow connections to be made to the db in the first place.
Thanks.
Steps To Reproduce
Is Issue Present in Latest Beta?
2.1.5 is the latest release available at the moment.
The text was updated successfully, but these errors were encountered: