Home

WebGoat is a deliberately insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components.
Now, while we in no way condone causing intentional harm to any animal, goat or otherwise, we think learning everything you can about security vulnerabilities is essential to understanding just what happens when even a small bit of unintended code gets into your applications.
What better way to do that than with your very own scapegoat?
Feel free to do what you will with Hack. Poke, prod and if it makes you feel better, scare him until your heart’s content. Go ahead, and Hack the goat. We promise he likes it.
Thanks for your interest!
The WebGoat Team
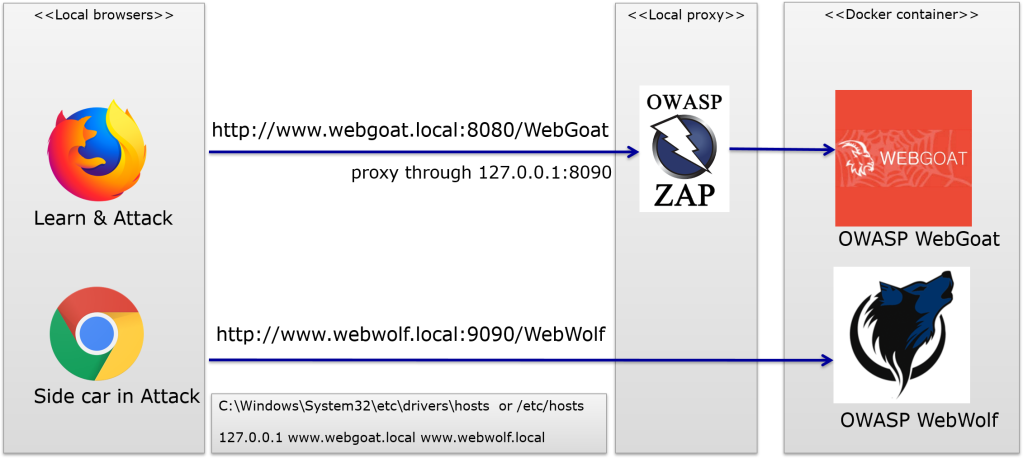
The following picture shows the ideal local setup for running WebGoat and following the lessons. It also shows WebWolf and how OWASP Zap can be used between the browser and OWASP WebGoat.
WebGoat consists of two applications that work together. One is called WebGoat and one is called WebWolf. WebWolf depends on WebGoat and requires that WebGoat is started first.
Both WebGoat and WebWolf are runnable jar files. Make sure the following ports are available: 80, 8080, 9090, 9001 when running locally.
There are several options to run WebGoat (and WebWolf):
-
Fork/Clone the repository, checkout the develop branch, build the artifacts using Java 17 and Maven 3.8+, and run the archives.
./mvnw clean install ./mvnw spring-boot:run -
Download the released and build jar files and run using Java 17
# Check if default ports 8080, 9001, 9090 are not taken or use the export (set for windows) below to change the defaults. export WEBGOAT_PORT=8080 export WEBWOLF_PORT=9090 java -jar webgoat-server-v8.2.3.jar -
Use the all-in-one docker container which contains a reverse proxy and both WebGoat and WebWolf which start in the correct order
docker run -d -p 8080:8080 -p 9090:9090 -e TZ=Europe/Amsterdam webgoat/webgoat:latest