New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
App Manifest "screenshots" member #49
Comments
|
Although we understand the appeal of showing screenshots of web applications as part of an application’s installation/“Add to Home Screen” UI, we have the following concerns:
We instead feel that web applications themselves serve as the screenshots: unlike “app stores”, users generally use web applications before they install them (i.e., they already have a good sense of what they look like and how they work, which is hopefully motivating users to install the application in the first place). Or, in case where installation is required to enable the features that would be represented in screenshots, the web site itself can present the screenshots in a web page. With respect to misrepresentation: the risk of emulating trusted system UI in the screenshot could be mitigated with appropriate presentation of the screenshot. Thus, it would be good for the spec to mention that as a security consideration in the spec. |
|
Perhaps the use case for this is not saving from the web but rather installing from a standalone separate store app that contains web apps packaged with a Web App Manifest? |
|
That's definitely a use case (and was the primary driver for it). However, Chrome on Android shows the screenshots (and |
|
Although I understand @marcoscaceres concerns, I do think all issues have to take into account a wider view of mobile ecosystems, specifically:
When considering functionality it's really important to consider a careful balance, with consumer needs taking a priority:
It's not clear that potential security issues outweigh the health/viability and cost to the consumer issues and regardless of Safari's implementation alternative browsers should be free to provide this functionality and decide what's best for themselves. |
|
Completely agreed with @mtom55's position. iOS & WebKits support for PWA, especially from an installation perspective lags far behind Android & Chrome. If Webkit continues to treat them as second class we are unlikely to see mass adoption. I also find two of @marcoscaceres points contradictory.
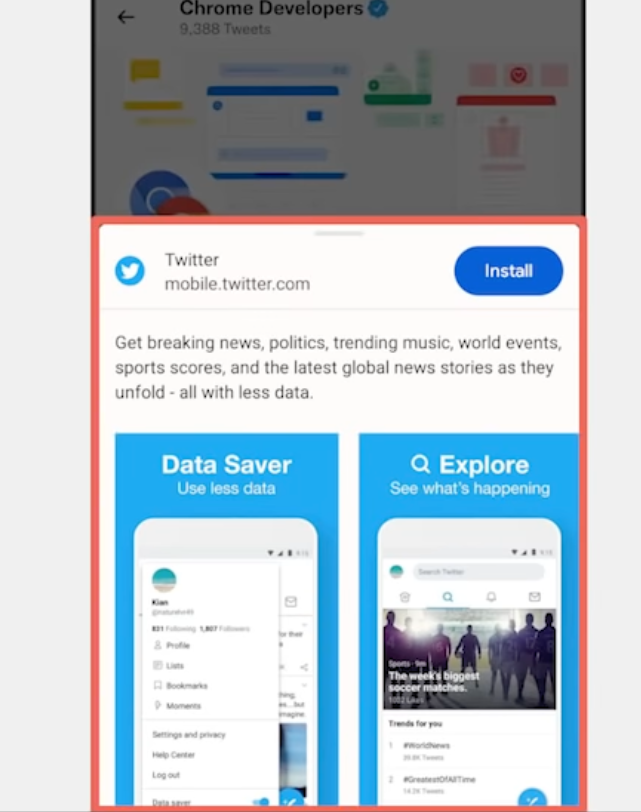
Screenshots of apps in app stores and otherwise are rarely directly representative of exactly the application, they provide context to what the user will do with the application- its material to convince the user that the application is worth installing! The twitter example posted earlier is a good example of this. Lastly, in response to this position:
I find this a low-concern to non-concern, assuming that invoking installation is done from the Safari web add to home-screen menu. The user has already started the installation flow at this point and has seen the application. From a security perspective, screenshot display is going to make any current not-possible impersonation attacks possible. Safari on mobile is already displaying the icon and name of the application. Safeties should be added in other layers around app installation- not by restricting PWA capabilities. Present the domain of the website and highlight cases where the domain is using common impersonation techniques (unicode character hacks etc). Safeties of this nature add to defence against phishing/impersonation attacks. |
|
Closing as we've identified our position. |
Request for position on supporting "screenshots" member in app manifest
(Please delete inapplicable rows.)
Information about the spec
Design reviews and vendor positions
Bugs tracking this feature
Anything else we need to know
Most browsers have facilities to enable users to add a website to their homescreen. Several browsers provide the ability to install PWAs. Currently the context that’s available to convey is the website’s origin, as well as the name and icons made available through the Web App Manifest. This is different from other store mechanisms, on all platforms, that also share developer-provided information such as a description and screenshots.
Microsoft’s Aaron Gustafson has proposed a Web App Manifest Application Information draft (see spec above), through which we can obtain that information.
Chrome implemented a new, richer user interface on mobile that displays this information (description and screenshots) when the developer has provided it (See help article). Chrome has started experimenting this on Desktop.
We’ve carefully designed this interface to continue to highlight known information such as the origin, and are working with the permissions and privacy teams to make sure we can evolve it responsibly going forward.
The text was updated successfully, but these errors were encountered: