New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
enable DOH/DOQ using Let's Encrypt certs out of the box #154
Conversation
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
This comment was marked as outdated.
|
I feel like Hal changing a light bulb 😓 |
This comment was marked as outdated.
This comment was marked as outdated.
|
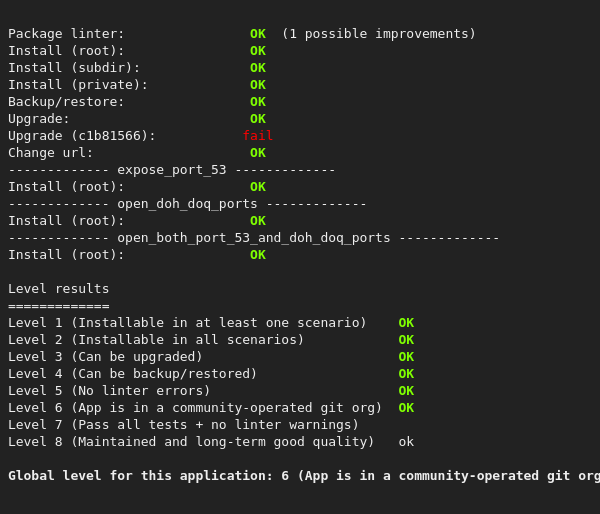
about f65fc16: and that's OK except for YNH, as dnsmasq uses port 53 on localhost, the port is used and YNH refuses to give it to AGH for outsides IP: so I had to remove the port from the manifest.toml and hardcode it in config and scripts |
This comment was marked as outdated.
This comment was marked as outdated.
i found why the Private DNS setting on Android was working on local but on another network....... it's working fine if i deactivate my allowlist! |
|
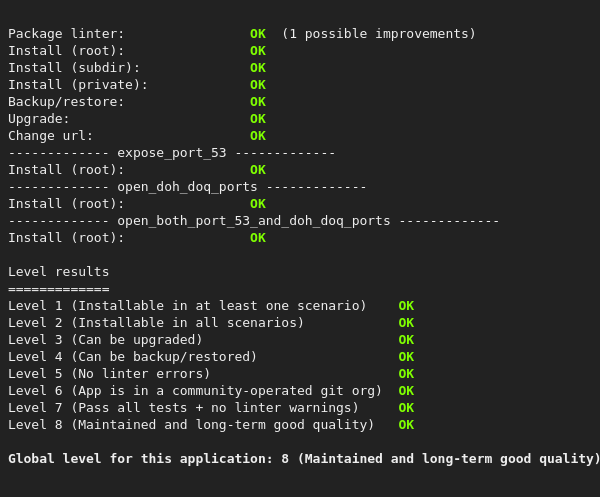
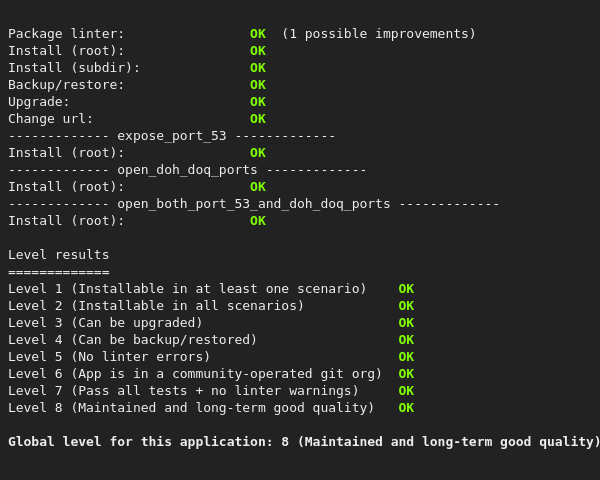
i think the release is ready, at last to merge in testing branch ^w^ poke @Ddataa it's lacking android docs and french translations but eh |
|
@OniriCorpe if you wish I can add some docs for Android. ;) Edit: Maybe it's not worth it, there's already an included guide in the app at
|
maybe documenting this could be useful to permit the ClientID usage on Android ?
|




Problem
Solution
is someone OK to test this?
PR Status
TODO
Current state
For the package
For AdGuard Home itself
A screenshot of the AdGuard Home front-end, showing the "Encryption settings", with all things validated