-
Notifications
You must be signed in to change notification settings - Fork 570
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Security limitations and issues for TagUI #146
Comments
|
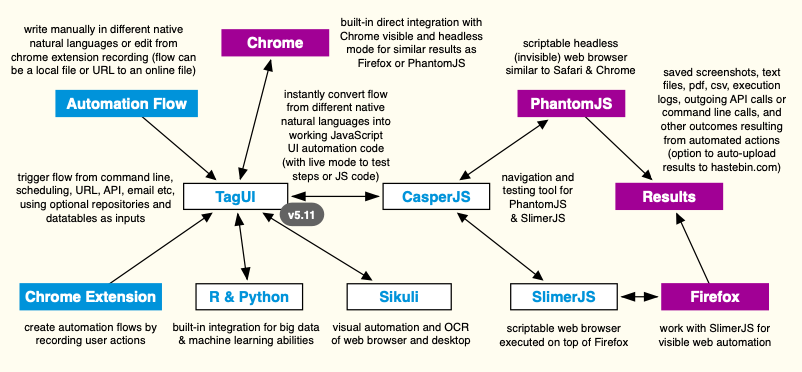
I'll use below architecture diagram for TagUI to elaborate on this topic. As TagUI and the foundation it is built on is open-source software, it means users can read the code of TagUI and all its dependencies to check if there is a security flaw or malicious code. This is an advantage compared to using commercial software that is closed-source, as users cannot see what is the code behind the software due to lack of visibility. For open-source software, users and developers who spot security issues will raise the issues to the maintainers and work towards a fix. For commercial software, other ways such as tracking the http traffic or file system activities have to be deployed to infer on what the software is doing. Following are links to the source code for TagUI and other open-source dependencies. You can dig through the source code for the other open-source dependencies below, or assume that security issues would have been spotted by users and fixed, as these projects are mature and have large user bases.
Following are more comments specific to TagUI for topic of security.
|
remove a potential security risk for webservice implementations of TagUI
|
The above security points had been committed to be part of |
Raising this issue on behalf of user email so that other users can benefit -
Currently, I've been tasked with conducting research on the security limitations/issues for TagUI, I would like to ask if there are any that you know of with regards to the tool.
The text was updated successfully, but these errors were encountered: