Script to test prevention and detection of network threats.
Usage:
pip3 install -r requirements.py
python3 main.py
#1 Test connection with live known bad IPs.
#2 Test connection with live known phishing URLs.
#3 Test TOR Exits Nodes.
#4 Test access to live Malware distribution Urls
#5 Test connection to known Cryptomining domains
#6 Test connection to Domain-Generated-Algorithm Domains.
#7 Test connection to Remote Desktop Management.(Anydesk,etc.)
#8 Test connection using known bad user agents.
#9 Generate DNS queries using DoH
#0 Exit.
Choice:
The script will dowload samples from OpenDBL (EmergingThearts and Cisco Talos), Security.gives (Mirai), OpenPhish, URLHouse, Bad User-Agents (mitchellkrogza) and SecOps-Institue Github (TOR Exit Nodes) and test connection to random samples.
Results are saved to different text files on the running folder with a timestamp so you can validate detection at your FW, Proxy, SIEM, etc.
This script is Work-In-Progress, bugs and exceptions may appear, and new features may be added on the future.
To Do:
.-Test download of malware samples from MalwareBazaar/URLHouse - Done v0.2
.-Test ssh scanning - Added v0.3 (as part of existing tests SSH Port 22 is tested alongside 80 and 443)
.-Test crypto mining domains Done v0.3
.-Test IDS with dummy requests Shifted-> It would be too much of a hassle to do so I added new features in v0.4 to compensate
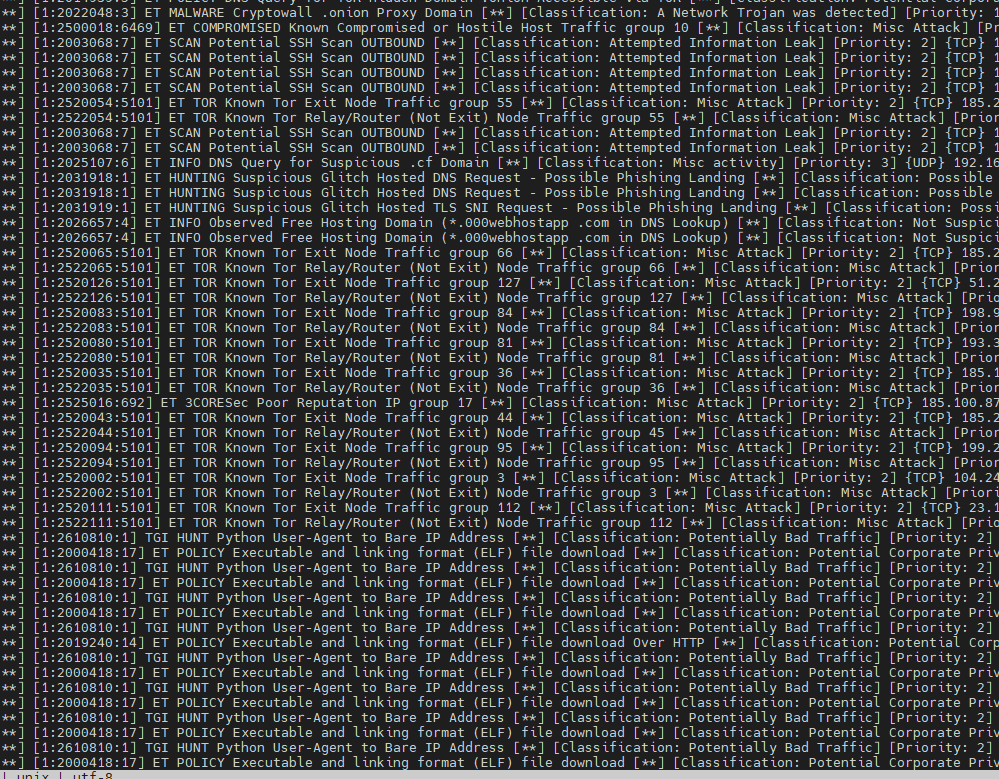
Suricata IDS picking up activity:
Thanks to:
.-OpenDBL
.-Abuse.ch
.-Netify (Used to get URLs for the Remote Desktop sim.)