-
Notifications
You must be signed in to change notification settings - Fork 2.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
'redirect_mismatch' error with hosted UI #5127
Comments
|
@YangMann do you've a repro project you could share with us? |
|
@attilah sorry the repo I'm working on is private. But I can share the details about redirect URLs. After having two sign-in/sign-out redirect URLs in amplify auth, amplify push, the generated "redirect link" to the hosted UI page is I think the problem is that the
At this point, when I run on localhost, the generated link will only contain localhost in the |
|
@attilah I have a question: how is the redirect uri populated when calling |
redirect uri populated from oauth.redirectSignIn at aws-export.js or Auth.configure({ oauth: {redirectSignIn: "..."} }). i got the problem when using two redirect uris, change it to one uri fix my problem. |
|
Hi Guys, any plans on fixing this issue? |
|
Same issue. I get |
Sorry guys but in fact, this is a normal behavior.Setup Then you get a Why ? What can you do ? and, Full code & example Personnally, I do something like |
|
@jordanranz 's fix totally worked for me! The correct solution is either that the SDK should handle this or the documentation should make a disclaimer about this snippet of code. |
|
Is it possible to change the I don't want my production add being allowed for localhost or my other callback URI's. Is there a way to override this value in the |
|
Remember to add your redirect url to the facebook developer dashboard |
|
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions. |
|
This issue has been automatically closed because of inactivity. Please open a new issue if are still encountering problems. |
|
For folks on this thread -- I recently experienced this issue myself and used the fix listed above. It works but I agree that our docs need to be updated and this should be fixed in the way the Amplify config state is created. This is now marked as a bug and will be addressed soon. #5565. |
|
could this fix also support an Expo app that has no window object? |
|
My Preview build fails with a redirect mismatch error, because it doesn't update auth with the preview url. I don't understand how Amplify doesn't do this automatically. How do you update sign-in/sign-out redirect URIs headlessly? |
|
I wish the documentation updates soon. I was facing this issue too, and in my case, I had more than 2 domains. I followed this comment and tidy that up a bit to suit my needs. I hope the following solution can help someone: Then you can call the |
|
@NiksanJP's solution worked for me, with a slight modification (my example is for Vuejs 3 with Pinia): I can now do multiple urls (as long as they are added using Amplify so that they are in the Cognito "App Client Settings") and I can use localhost for testing and development. This should be handled in the Amplify.configure() code. Its makes no sense to have this issue, I was limping along with another hack that meant that I could either run my prod service or my localhost but not both before this fix. Why isn't this the default? Thanks @NiksanJP! |
|
Hi 👋 Closing this as resolved. The docs now clearly show how to handle multiple redirect URIs. If you are still experiencing this issue and in need of assistance, please feel free to comment and provide us with additional information so we can re-open this issue and be better able to assist you. Thank you! |
|
I have to ask @tannerabread why is the newly documented answer better than mine above? I feel like mine is cleaner and assumes that the current window.location is in the cognito config and will fail otherwise. What is my solutions missing? |
|
Sorry @contractorwolf, I wasn't trying to imply the answer in the docs is better, only that a solution does exist. I prefer the succinct nature of your answer as well. I can speak with the team to make sure I'm not missing anything that could be wrong about that change, and if not I will change the docs for it myself. I will say though outside of setting the redirectSignIn/Out, you shouldn't be configuring both |
|
cool @tannerabread, I was working off of an earlier answer that included the Auth.configure(). I will test using my code without that and get back to this thread on whether or not it works. If so I would suggest that Amplify should assume these values and not require them in awsExports configuration: unless there is something else that I am not understanding? Ill update my answer after I have tested without the Auth configuration code. |
|
@contractorwolf Cognito/Hosted UI would still need to know all of the possible redirects for your app (I think the limit is 99 in and 99 out). Amplify currently doesn't handle that inside of the exports because using the window object doesn't work the same way for mobile apps AFAIK, which Amplify supports. So this would just be a docs change to show the cleaner way of finding the url on app load on the JS side. |
|
CORRECTION |
|
@tannerabread but if the Amplify.configure() method were to just assume that the redirectSignIn/redirectSignOut values were the current location origin (window.location.origin for web and however mobile determines it) then the values would never have to be stored in the awsExports file and then edited as above. It could just check the current location.origin url on that call of configure() against the list in cognito and validate. |
|
@contractorwolf |
|
right on @tannerabread, I just would just like to keep as simple as possible but I want to confirm that I am still within basic recommended guidelines. Just let us know what you find. |
|
I can give an update but the discussion isn't complete yet. For Amplify to handle it, it would have to be in a major version release sometime in the future because that would introduce some breaking changes and how it would be implemented would need to be discussed as Amplify would need to know if the user is on dev or prod while configuring. I will open up a separate feature request for this or reword the original post to be more clear what would be expected from this feature. I might be more inclined to leave this one because of all the context and just reword the title/OP. For the docs change, we are trying to ensure there are no security implications with using Second point about the docs change, we do allow redirects to specific paths, so if I would change the docs it would need to have 2 examples, one like you have shown above and one that shows Lastly, the solution you posted above modifies the original and maybe that's not desirable in some circumstances, so we might need to keep it as making a copy (e.g. updatedAwsConfig) and setting it through that. The discussion is still going but I wanted to update you with where we are at. The main points being Amplify handling it would need to go in a future major version and for the docs update we are just trying to make sure we put the best solution forward. I think we are in agreement the localhost check with the RegEx and other things is probably not the best solution, but want to find it before we change it. |
|
Cognito & Amplify should either not allow setting more than one URL, or they should handle it properly. When you set more than one domain/URL, it could link to some documentation and this can have consequences. |
|
This is how i made the application handle two redirectURIs. |
|
these docs are insufficient. still having issues getting this to work properly. |
|
Hi @dagnym - can you please help us by creating a new GitHub issue to help us get your set up and reproduce the issue? |
|
are we still in the holding pattern @tannerabread? I don't love my solution because it seems counter-intuitive but it does solve my specific issue. I just want to be sure that in solving this (ultimately configuration issue) isn't unknowingly leaving a door open for some security manipulation. What did the discussions reveal? |
** Which Category is your question related to? **
Auth / Hosted UI
** What AWS Services are you utilizing? **
Cognito, Amplify Console
** Provide additional details e.g. code snippets **
Hi,
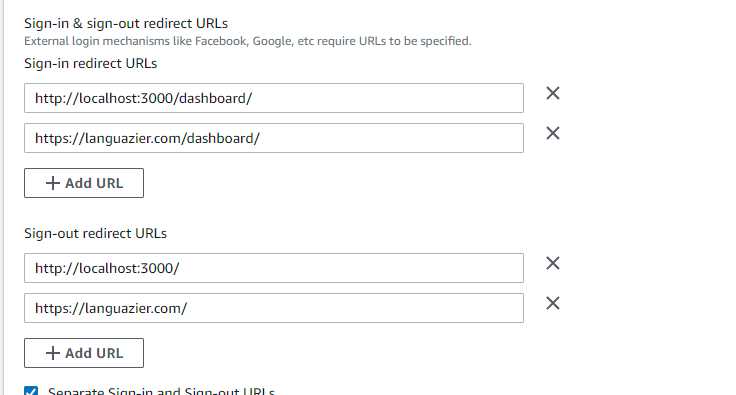
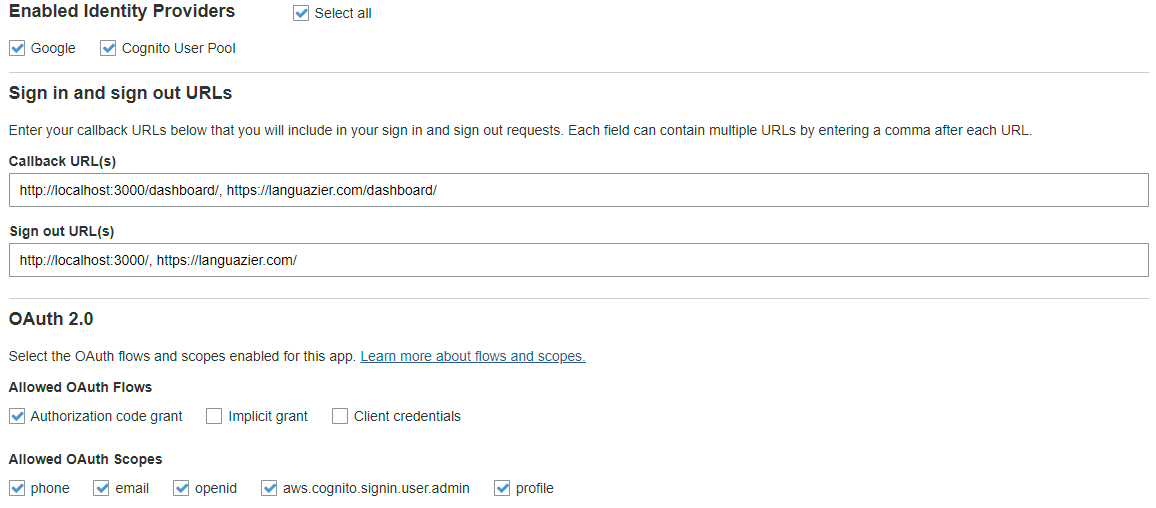
My auth work flow worked fine with the hosted UI when I was only using http://localhost:3000/ as the sign in/sign out url. When amplify console created a dev build, it hosted the frontend on a different url (https://dev.<some_id>.amplifyapp.com/ in my case). When opening the hosted UI from this url, it complained "redirect_mismatch", which is understandable since I only have localhost configured in cognito at this point.
I ran
amplify update authto add the console provided app url to the sign in/sign out urls,amplify pushthengit commit&git pushto make the amplify console pick up the changes. However, the console hosted app still gave me "redirect_mismatch" error. I checked the aws-export.js file and cognito console, the redirect urls are exactly the same ("http://localhost:3000/,https://dev.<some_id>.amplifyapp.com/"). I used Chrome's inspection tool to check the actualredirect_uristring in the HTTP request, also exactly the same. I have no idea why the hosted UI is complaining mismatch.Then I found out the app stopped working on my localhost, too. Same "redirect_mismatch" error. :(
Any help will be appreciated!
The text was updated successfully, but these errors were encountered: