-
Notifications
You must be signed in to change notification settings - Fork 2.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
auth w/ Google Federation - Access Token does not have required scopes #5921
Comments
|
@mtraynham as I mentioned on the issue #5935. Previous the change you mention the library was sending the query string param scopes instead of scope which is the correct param. The default behavior by Cognito when the scope param is missing is that it will return (as is mentioned on this Authorization endpoint Cognito docs) all the scopes available. Can you check if the scope you have configured are present on AllowedOAuthScopes on your App client (clientId) settings. You can check those on Cognito console under App Integration>App client settings or using |
|
@mtraynham Can you check removing |
|
We have other providers that use phone, Google just doesn't provide that, so I can't really remove it |
|
I have the exact same problem, where users from external identity providers (federated) cannot update their attributes. Any updates on this? |
|
@mtraynham Can you let me know where you are at with this? We want to help you but I'm trying to understand if you were able to figure out a workaround for this issue? As @elorzafe mentioned, there were some changes that we made to fix the separation for string queries in order for not all scopes to be returned. Please let us know where you are at with this and where we can help. Thanks ! |
|
Im getting the same error whenever I attempt to even Read the user attributes of a cognito user. Any update on this? |
|
How can Amazon, AWS and Cognito have a javascript client with 642 open issues, and a major issue like this that affects Cognito opened 8 months ago that hasn't had any activity in over a month? |
|
I'm stuck with Unfortunately testing something like SAML integration is a bit more involved for a local environment, so may not get to it today. |
|
This is not a bug with amplify per-se, it's an issue with Cognito & federated/SSO auth - if you look at the network tab when you call |
|
Is there any update on this one? I'm struggling to get a user's profile image (which was working around 9 months ago)... Something must have changed which has broken this? I've attempted to call Any ideas? @dabit3 @ericclemmons |
|
Same issue. Occurs on Cognito account that is still valid, but was already removed from the consuming application. We have disabled and then removed the user from Cognito. |
|
Same issue, what version of amplify doesn't have this issue? |
|
Waiting for a miracle over here |
|
Good evening, everyone 👋 Wanted to give an update on this issue before the weekend. We have have been trying to reproduce this issue this on We have to yet to reproduce this issue with a Google OAuth flow but we will continue to look into it. Below are the current results of the attempts to reproduce. In the meantime, here is the code and amplify config used during testing. Some follow up questions:
package.json {
"name": "5921-oauth-google",
"version": "0.1.0",
"private": true,
"dependencies": {
"@aws-amplify/auth": "3.2.8",
"@testing-library/jest-dom": "^5.11.4",
"@testing-library/react": "^11.1.0",
"@testing-library/user-event": "^12.1.10",
"react": "^17.0.2",
"react-dom": "^17.0.2",
"react-scripts": "4.0.3",
"web-vitals": "^1.0.1"
},
"scripts": {
"start": "react-scripts start",
"build": "react-scripts build",
"test": "react-scripts test",
"eject": "react-scripts eject"
},
"eslintConfig": {
"extends": [
"react-app",
"react-app/jest"
]
},
"browserslist": {
"production": [
">0.2%",
"not dead",
"not op_mini all"
],
"development": [
"last 1 chrome version",
"last 1 firefox version",
"last 1 safari version"
]
}
}aws-exports.js const awsmobile = {
"aws_project_region": "XXXXX",
"aws_cognito_identity_pool_id": "XXXXX",
"aws_cognito_region": "XXXXX",
"aws_user_pools_id": "XXXXX",
"aws_user_pools_web_client_id": "XXXXX",
"oauth": {
"domain": "XXXXX.amazoncognito.com",
"scope": [
"phone",
"email",
"openid",
"profile",
"aws.cognito.signin.user.admin"
],
"redirectSignIn": "http://localhost:3000/",
"redirectSignOut": "http://localhost:3000/",
"responseType": "code"
},
"federationTarget": "COGNITO_USER_POOLS"
};
export default awsmobile;App.js import React from "react";
import Amplify, { Auth } from "@aws-amplify/auth";
import awsconfig from "./aws-exports";
Amplify.configure(awsconfig);
const App = () => {
const initialState = { session: null, user: null, userInfo: null };
const [state, setState] = React.useState(initialState);
const handleSignIn = async () => {
await Auth.federatedSignIn({ provider: "Google" });
};
const getUser = async () => {
const user = await Auth.currentAuthenticatedUser();
const userInfo = await Auth.currentUserInfo();
const session = await Auth.currentSession();
console.log({ session, user, userInfo });
setState({ session, user, userInfo });
};
React.useEffect(() => {
getUser();
}, []);
const { user } = state;
return (
<div className="App">
<button onClick={handleSignIn}>Open Google</button>
<button onClick={getUser}>Get Current Session</button>
<button onClick={() => Auth.federatedSignIn()}>Open Hosted UI</button>
<button onClick={() => Auth.signOut()}>
Sign Out {user?.getUsername()}
</button>
</div>
);
};
export default App;
Results: Console logging |
|
Hi there, I was having the same problem and bumped into this thread. I was initially using "aws-amplify": "^4.0.2" fwiw. I have tested your code (which btw is not the same the one from your comment than from your repo) and I still face the same issue: So I suspect the problem is not the library, but my cognito config. In my aws-exports the oauth scopes are: And, in case it helps, my Cognito client is configure as follows: esource "aws_cognito_user_pool_client" "client" {
name = "demo_app"
user_pool_id = aws_cognito_user_pool.pool.id
allowed_oauth_flows = [
"code",
]
allowed_oauth_flows_user_pool_client = true
allowed_oauth_scopes = [
"email",
"openid",
"profile",
]
callback_urls = local.callback_urls
logout_urls = local.logout_urls
explicit_auth_flows = [
"ALLOW_REFRESH_TOKEN_AUTH",
"ALLOW_USER_SRP_AUTH",
]
prevent_user_existence_errors = "ENABLED"
read_attributes = [
"address",
"birthdate",
"email",
"email_verified",
"family_name",
"gender",
"given_name",
"locale",
"middle_name",
"name",
"nickname",
"phone_number",
"phone_number_verified",
"picture",
"preferred_username",
"profile",
"updated_at",
"website",
"zoneinfo",
]
supported_identity_providers = [
"Google",
"COGNITO",
]
write_attributes = [
"address",
"birthdate",
"email",
"family_name",
"gender",
"given_name",
"locale",
"middle_name",
"name",
"nickname",
"phone_number",
"picture",
"preferred_username",
"profile",
"updated_at",
"website",
"zoneinfo",
]
access_token_validity = 60
id_token_validity = 60
refresh_token_validity = 30
token_validity_units {
access_token = "minutes"
id_token = "minutes"
refresh_token = "days"
}
}Interestingly enough, if I log in with a user that uses username and password, I can fetch the attributes. If I log in with a user that uses Google SSO, I can't. Any ideas as to what's wrong in my cognito client? Thanks! |
|
Small nit: I have re-tried the whole thing and I've got two users (one using google SSO and one using email and password); and here are the results of some tests I've just made:
|
|
Last update from me: I have been testing Allowed OAuth Scopes and I fixed my problem: |
|
Here is the solution I found to this problem: #6444 (comment) |
|
@menendezjaume hmm, I did have the I will reach out to the team with this issue and update the docs to reflect this. Thank you for pointing that out! |
|
That being said, closing this out as we have a working solution in the necessary step of making sure the If you try the above and it still does not work for you, please open a separate issue with your particular auth configuration so we can better find the cause of the issue in your case. Thank you! |
|
This issue has been automatically locked since there hasn't been any recent activity after it was closed. Please open a new issue for related bugs. Looking for a help forum? We recommend joining the Amplify Community Discord server |


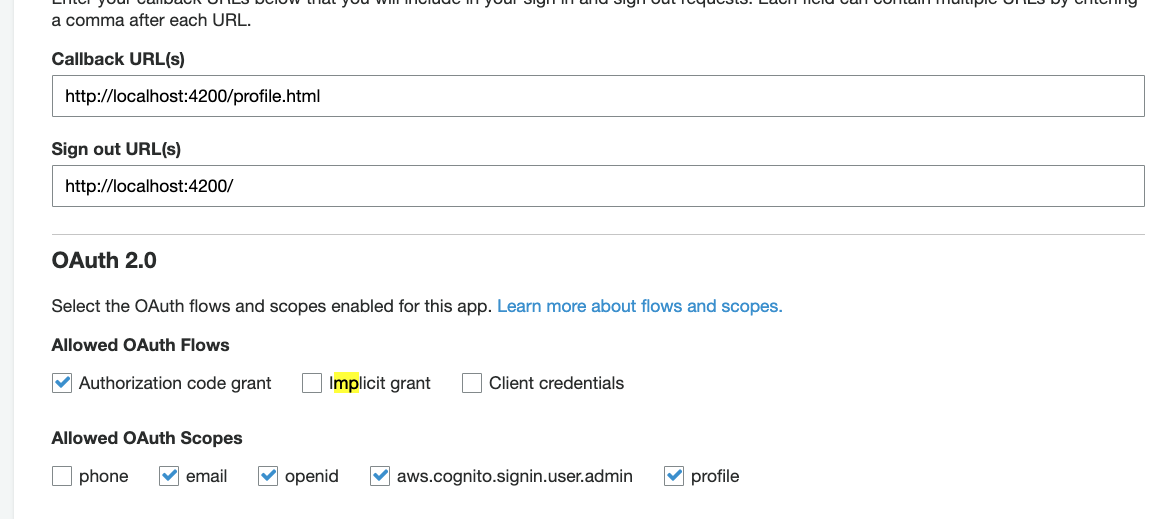

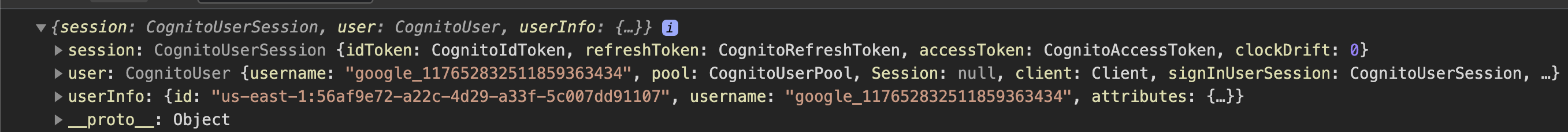

Describe the bug
Upgraded from
"@aws-amplify/auth": "3.2.7"to"@aws-amplify/auth": "3.2.8"and a federated login with Google stopped working with a 400 error from Cognito.I initially upgraded to 3.2.8, and then downgraded back to 3.2.7, and downgrading has resolved the error. None of the dependency versions for
"@aws-amplify/auth"were changed during the downgrade, so I believe the bug is specifically within theauthpackage.Likely related to:
To Reproduce
Using
"@aws-amplify/auth": "3.2.8", login with a federated user and retrieve the session.Expected behavior
It doesn't 400 and passes the scopes correctly.
Code Snippet
Screenshots
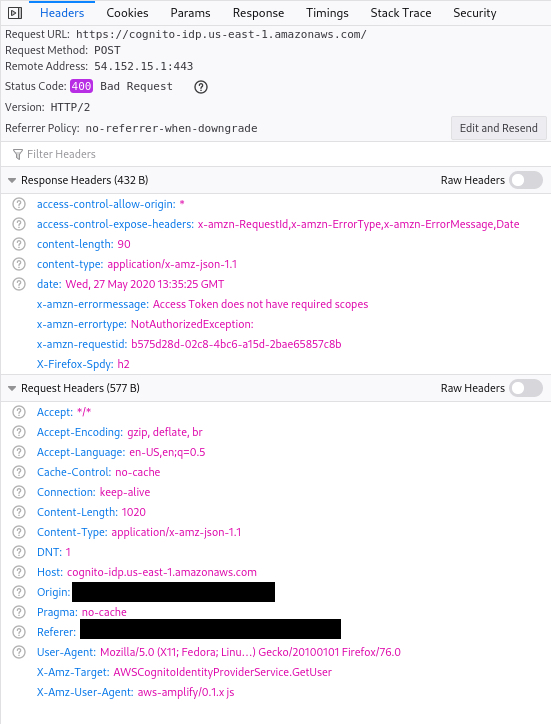
What is Configured?
Smartphone (please complete the following information):
Additional context
The text was updated successfully, but these errors were encountered: