New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Question] Why doesn't this model work? #1237
Comments
|
@JoshSharpe I tried to copy your model and policy, but the results are not consistent with yours. Are you sure that the model you provided is the same as the one you are using locally? |
|
Regarding the model, if you don't need a domain, you can use |
This is interesting. Here are my screenshots. They do appear to match from what I can tell. |
Struggling to understand domain vs obj. Based on my use case, I need to map subject based on group + object? So that is why I include |
|
@JoshSharpe There are some differences in matchers. The model you actually use After synchronizing with the model you actually used, their results are consistent |
|
@JoshSharpe I've drawn some diagrams that I hope can help you e, err := casbin.NewEnforcer("model.conf", "policy.csv")
if err != nil {
panic(err)
}
fmt.Println(e.Enforce("alice", "organizations/org1", "create_workspace"))First, NewEnforcer will generate an Enforcer based on the model and policy you provide e.Enforce("alice", "organizations/org1", "create_workspace")Then when enforced, it will first determine whether There is some ambiguity here, and I think that's why you're confused According to Casbin's default rules, Depending on the matcher in the model, you might think that Also, since the value of This matching only happens in matchers, and at the model level |
Is this a bug or intended behavior? So I saw the g function as: g(a,b) described how a is grouped to b It seems more like g(a,b,c) has additional underlying context. It isn't that it can be used for domain but it must be used for domains. Given that assumption, would my best approach here just to have a star for object and treat the object as the domain? So that a group/role can map to <permission, context> where context is "organizations/:id" as either the object or domain? |
|
@JoshSharpe I'm sorry for the delay in responding. This issue is quite complicated for me. You can achieve the desired effect by changing the naming method or using a matching function, or you can try to replace your model configuration. If you have a better method or suggestion, please share it with us as it would be very helpful. |
|
Looking forward to your updates and wishing you good progress. I will also be paying attention to this part recently. |
Copying to my correct account. |
|
Here's where I'm at now. Looking at model examples a little more, this one kind of works for my use case. But I think I'm still misunderstanding some concepts if you don't mind clearing things up. Model: Policy The thoughts here are that the roles are scoped to an object through the abbreviation:role. The domain is the id for the given object. And the action is a regex grouping of activities. Object is the "type" of domain. This produces the enforcement that I'm seeking. However, I'm not sure what the best approach is for searching this data. Say I want to find the organizations that Alice is has access to. Right now I can GetDomainsForUser. However, that includes domains for all objects (types). Do I need to manually filter data or is there some option I am missing in documentation to help me here? |
|
@JoshSharpe You may consider doing further screening manually. |
No I expect it to behave how it does. However, I am curious how people typically solve the following problems. Using my use-case as an example, how would one:
|
|
I'm going to just write my own mongo queries to do this for now. And probably abandon roles to keep the queries simpler. But if anyone can help suggest a model and/or policy that fits and the appropriate casbin functions, here is a summary of what I am trying to do. Alice has access to read org/A, which is an organization I'd also like to be able to do queries on the policy:
The problems I've run into:
|










Want to prioritize this issue? Try:
What's your scenario? What do you want to achieve?
I'm trying to get a basic model running to understand how this authorization works. The examples aren't practical enough to help me grasp these concepts well enough. I feel like I'm missing something so any help or guidance would be appreciated.
My hope:
Resource = /organizations/:orgId or /organizations/:orgId/workspaces/:wkspId
By doing the full path, I can ensure uniqueness across all and maintain a hierarchical structure. ie make sure a wkspId is inside a given org.
Actions = create_workspace, read_users, update_users, etc. So just various actions that can be done within these resources.
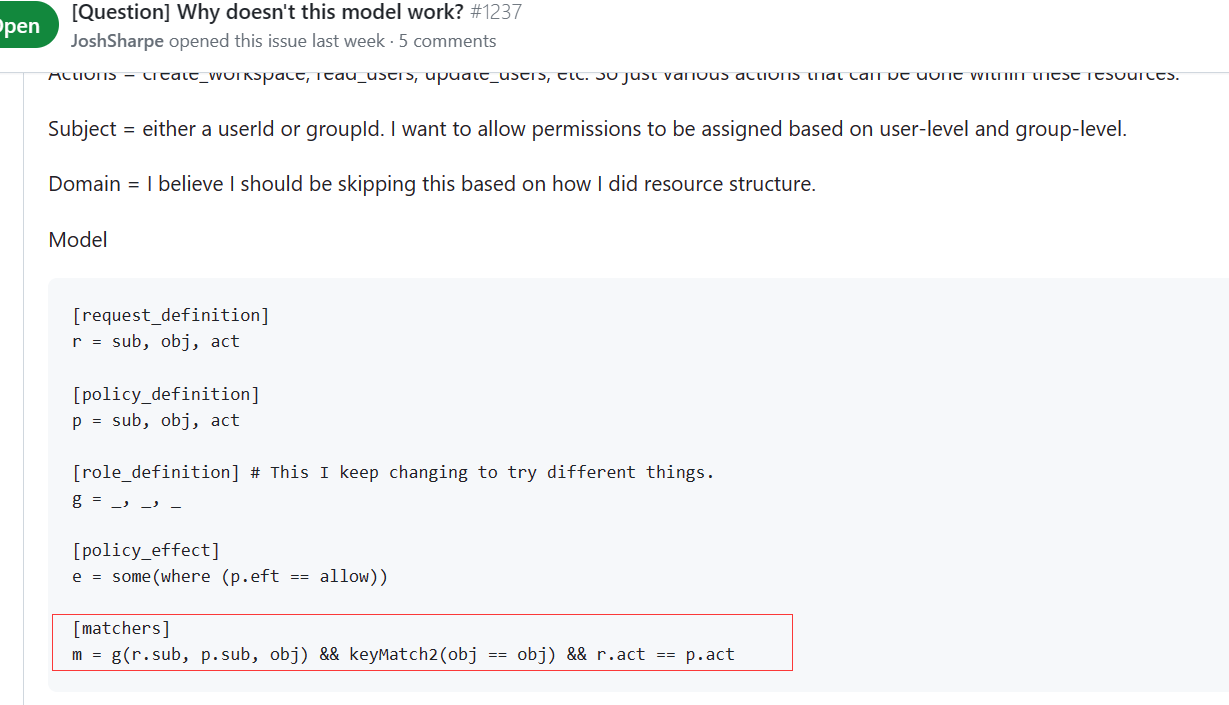
Subject = either a userId or groupId. I want to allow permissions to be assigned based on user-level and group-level.
Domain = I believe I should be skipping this based on how I did resource structure.
Model
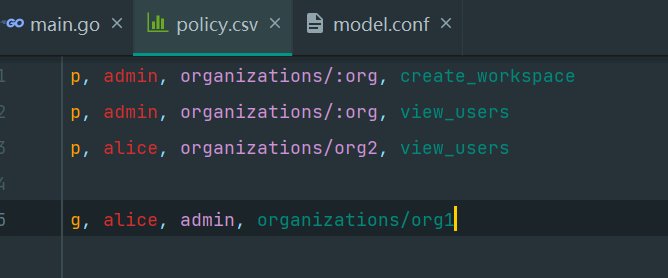
Policy
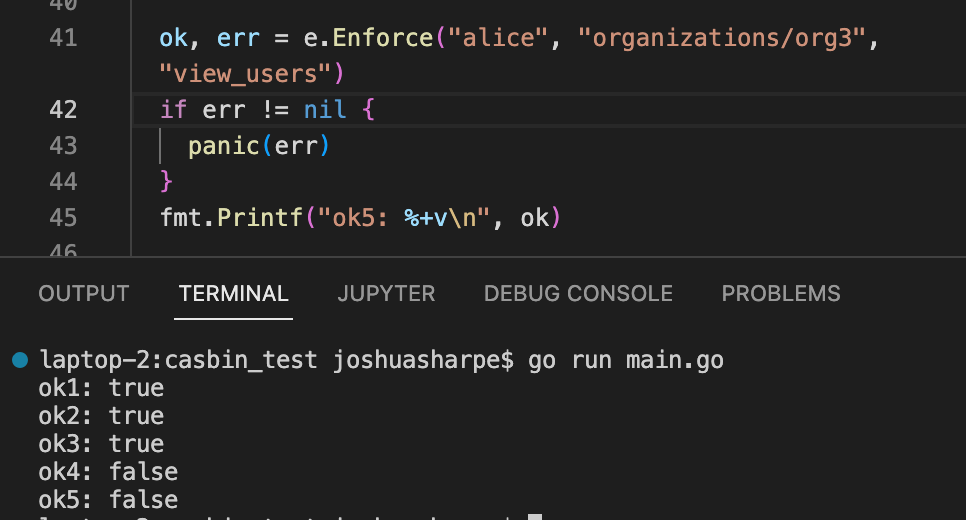
Enforce appears to work as expected:
However,
Questions:
How do I see a list of organizations that the user Alice has access to?
How do I see a list of users and roles that an organization includes?
Am I on the right track for setting this model up correctly?
The text was updated successfully, but these errors were encountered: