New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Question] - Please help on defining casbin model and policy for following use case. #1246
Comments
|
Hi, @sujit-baniya It looks like there are several issues, and I cannot help you solve them all at once, but don't worry, I will help you sort them out gradually. First, your model configuration format should correspond to your actual policy: The following figure shows the actual correspondence, which obviously does not match your expectations. One field should correspond to one string, and you can try writing multiple policies. Since I am not sure about the actual meaning of each field, you can make some modifications first and reply to me below, and then we can further correct them. |
|
@PokIsemaine Thank you for your response. I'm able to fix the permission by using following model and policy func main() {
perm, err := permission.Default(permission.Config{
Model: "model.conf",
Policy: "policy.csv",
})
if err != nil {
fmt.Println("error: ")
panic(err)
}
perm.AddFunction("isMatch", func(args ...interface{}) (interface{}, error) {
switch attributes := args[0].(type) {
case map[string]any:
switch condition := args[1].(type) {
case map[string]any:
return IsMatch(attributes, condition)
case string:
t, err := getMapFromString(condition)
if err != nil || len(t) == 0 {
return true, nil
}
return IsMatch(attributes, t)
}
case string:
if attributes != "" {
attr, err := getMapFromString(attributes)
if err != nil {
return false, nil
}
switch condition := args[1].(type) {
case map[string]any:
return IsMatch(attr, condition)
case string:
t, err := getMapFromString(condition)
if err != nil {
return true, nil
}
if len(t) == 0 {
return str.EqualFold(attributes, condition), nil
}
return IsMatch(attr, t)
}
}
}
return false, nil
})
fmt.Println(perm.EnforceEx("finance", "domainHere", "/expense/1", "write", map[string]any{
"service": "*",
"db": "golang",
}))
}It's working as intended. Now the thing I'm stuck is on group. Can you please suggest how could I fix Basically I'm trying to assign a role to user for a domain with service and entity id For .e.g |
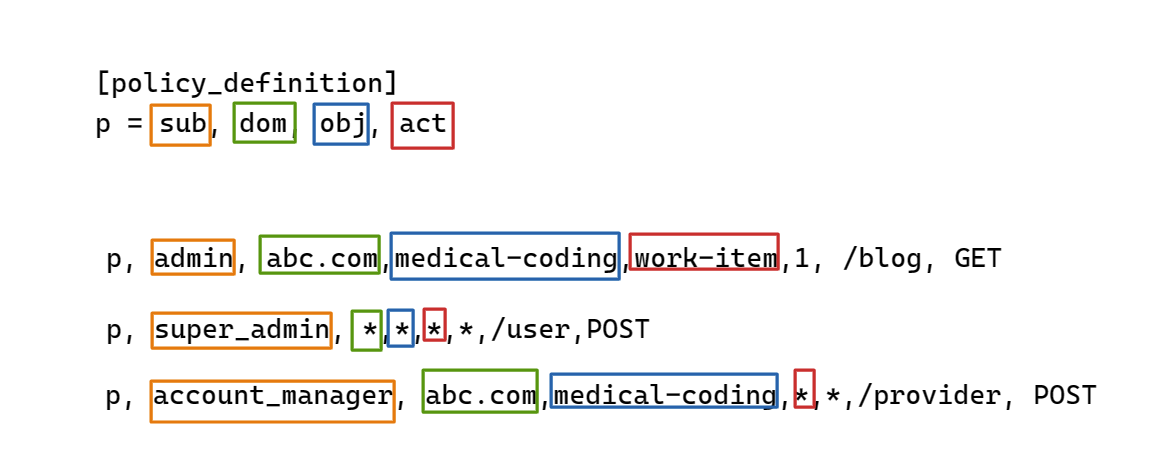
I have a use case where a role is assigned to an entity id on a service for a specific domain. the policy would look like this.
Here, I'm unsure how to define a model to match/enforce requests based on the sample policy provided above.
I've tried to refactor the following model to make it work for the policy.
I'm not able to refactor the model. Please suggest how I could make it work.
The text was updated successfully, but these errors were encountered: