New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Setting Sec-WebSocket-Protocol header on response to ws request fails
#179
Comments
|
Hey! 👋 Thanks for raising this and apologies for the delayed response. I might be misunderstanding this, but I would've thought this code that copys headers from the miniflare/packages/http-server/src/index.ts Lines 353 to 363 in b887877
Which version of Miniflare are you using? |
|
2.3.0
…On Fri, Mar 4, 2022 at 10:10 AM MrBBot ***@***.***> wrote:
Hey! 👋 Thanks for raising this and apologies for the delayed response. I
might be misunderstanding this, but I would've thought this code that copys
headers from the Response to the WebSocket response added in 2.1.0 would
solve this:
https://github.com/cloudflare/miniflare/blob/b887877810a745f2a458d20da0a3dbd9f8a58cf4/packages/http-server/src/index.ts#L353-L363
Which version of Miniflare are you using?
—
Reply to this email directly, view it on GitHub
<#179 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/AAATUBGDAKCUZU2IC7ZJEWDU6JU25ANCNFSM5OWVZZIQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
You are receiving this because you authored the thread.Message ID:
***@***.***>
|
|
I realize this isn't a reduced test case and I apologize. It's possible we are doing something wrong. What we found was that in order for a web socket connection to succeed in CF's environment, if the request included the header But that if we added that response header to Miniflare then ... something bad happened. I can't remember what the bad thing was, maybe an error, or maybe the connection just failed in some way. It actually wasn't me who found this on our team. I'll poke the person and see if he can remember what the failure mode was. |
|
Miniflare appears to automatically set the
When we set the The browser does not like receiving these duplicate headers and fails the connection upgrade. Chrome won't show the response headers with this type of failure, but you can see them in Firefox: |
|
Ah ok, that makes more sense! Thanks for the extra details. Will get this fixed. 🙂 For now (you might already be doing this), you could skip adding the |
|
Thanks @mrbbot. Thanks for the suggested workaround, that is exactly what we are doing for now. |
See #490 for a detailed description of the problem this solves. Previously, we had `ws`'s automatic `Sec-WebSocket-Protocol` handling enabled, in addition to adding the header ourselves. This lead to duplicate sub-protocols in the WebSocket handshake response which is a protocol error. Workers require users to include this header themselves in WebSocket `Response`s, so ignoring this key outright when copying headers would be incorrect. Instead, we just disable `ws`'s automatic handling. Funnily enough, we had exactly the same issue in Miniflare 2 too (#179), and fixed it in 34cc73a. Looks like the fix didn't make it into Miniflare 3 though. :( This PR also fixes an issue where `1006` closures were not propagated correctly. This is an issue in Miniflare 2 too (#465), so we should back-port this. Supersedes #490
See #490 for a detailed description of the problem this solves. Previously, we had `ws`'s automatic `Sec-WebSocket-Protocol` handling enabled, in addition to adding the header ourselves. This lead to duplicate sub-protocols in the WebSocket handshake response which is a protocol error. Workers require users to include this header themselves in WebSocket `Response`s, so ignoring this key outright when copying headers would be incorrect. Instead, we just disable `ws`'s automatic handling. Funnily enough, we had exactly the same issue in Miniflare 2 too (#179), and fixed it in 34cc73a. Looks like the fix didn't make it into Miniflare 3 though. :( This PR also fixes an issue where `1006` closures were not propagated correctly. This is an issue in Miniflare 2 too (#465), so we should back-port this. Supersedes #490
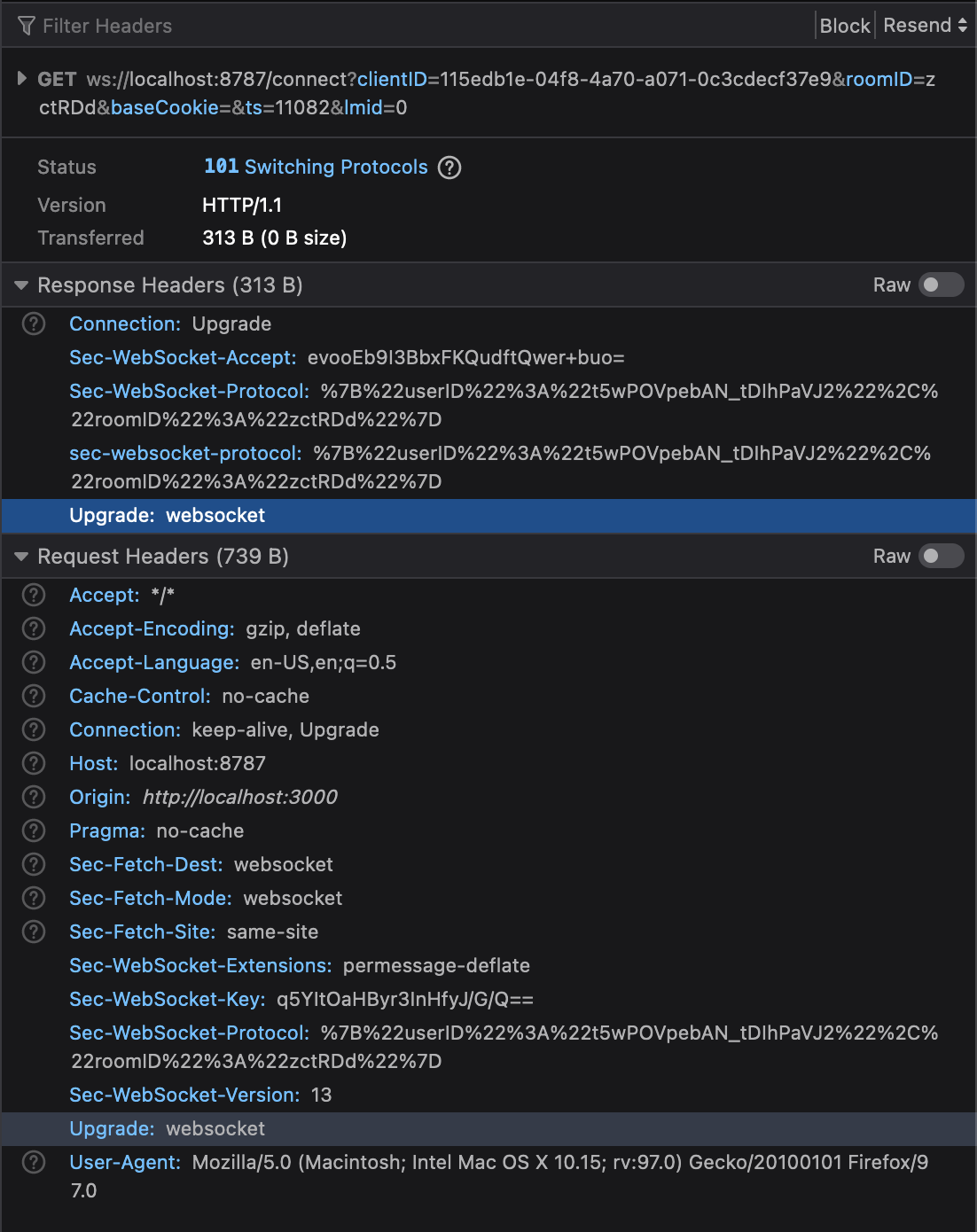
The standard (and Cloudflare) require that if
Sec-WebSocket-Protocolrequest header is sent in a websocket connection request, the server must acknowledge it by setting a response header with the same value.If you do this in miniflare, however, the response fails:
The text was updated successfully, but these errors were encountered: