You can't prove that you created your content, or that it's not fake or false. But you can prove it's coming from you--not impersonation. And you're NEVER locked-in to any type of encryption; Data is authenticated using the binary presence & absence of keys to lists of encrypted items (hence publicly verifiable yet authorized-only.)
- Exposure is allowed (typically authentication--rolling-code or not--relies on shared secrets; employers allow you to open doors only if that door accepts your private string of characters--matching what the door expects to see; The door is aware of a secret and must never expose it. But if instead the door contained your number, that ever-changing number can be displayed on the door and even made public. EVERYTHING you gave the door, and EVERYTHING the door contains, can be safely made public raw.)
- Compromise-evident device (just as tamper-evident devices prove they've been tampered with, Authorship proves its user has been compromised; Your adversary's goal is to take your life and continue modifying your number--fooling us into thinking you're still there. But if your personal folder was protected, no one can modify on your behalf. This is how we'll know not to trust words under your name unless we can verify your number modification.)
- Canary update authentication
- Group authorization (numbers can be assembled using ciphertext from multiple users.)
- Animal theft management (animal biometric data can be assigned to numbers; If you can't modify the number associated with your animal, it's not your animal. Authority registrars should be able to easily identify animals such as by imaging a cow's wrinkly nose.)
- Voter fraud prevention (you verify voters whom only registrars identify.)
- Ownership proof (assign item to Authorship number, modify it with their message to prove ownership.)
- Cryptographer's acknowledgement (you may need to verify that your new number is available to the public or verifying party--as you can be censored in some extreme circumstances. Here, the verifying party may arrange to modify their number in response and you can rest assured that your authentication event has been acknowledged.)
- Skipping through verification with outdated numbers (here, the proving party had published multiple numbers beforehand. Their main number had changed so many times, public files older than a year for example, have been discarded. Now, those who have not verified since the number publishing, wish to know that each and every modification to this date is what the proving party intended. And so the proving party is asked to modify one of their slower numbers of higher viscosity. The message for that event instructs all verifying parties to overwrite the main number with a new one. Now those catching up have access to periodic verification as if they ran through the entire chain.)
- Disposable sessions without breaking trust (let's say some service had published a single number beforehand, and serves one million users on their network years later. Each user requested in simultaneity and demanded authentication for each and every byte. Here, the service's number is not modified per user since that would require all users to catch up on verification as they wait their turn with the service. Instead, the service modifies its main number once with a message containing the sha256sum of a text file of specified size uploaded separately. This text file contains one million new numbers--each disposable and dedicated to one user. Meanwhile, the service's new main number awaits future visitors who were forced to verify only once so far. Those without access to the public file for this main event may ask the service to modify a slower number--as done in the previous point.)
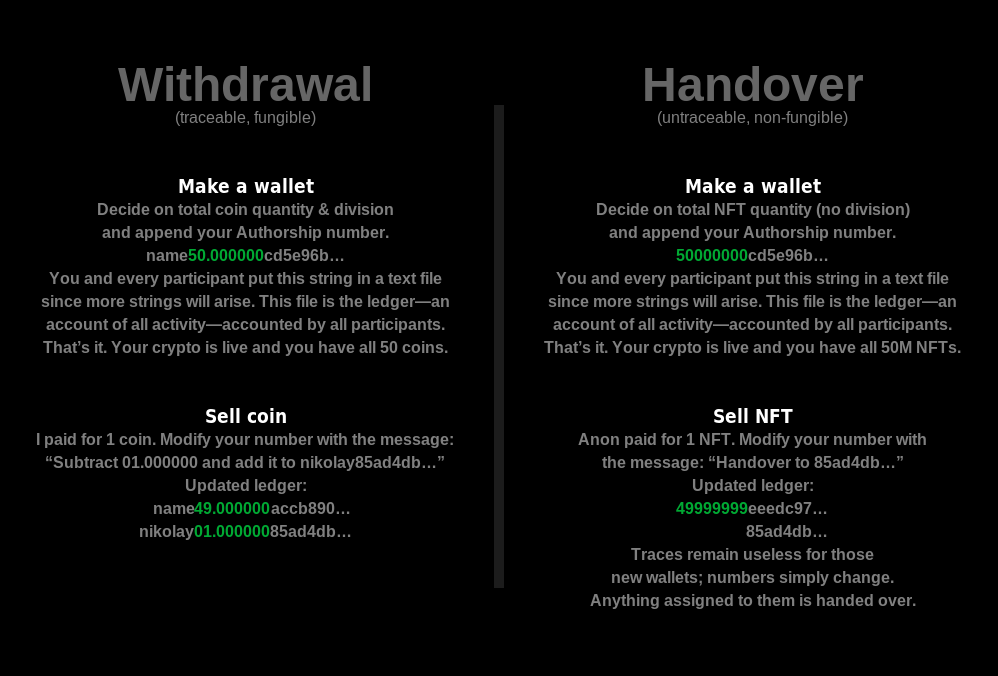
- And cryptocurrency:
I discovered Authorship December 2019, which would not have been possible without direct inspiration from my personal heroes who sacrificed their freedom and demonstrated beautifully the need for publicly accessible AND comprehensible cryptographic evidence--Julian Assange and Edward Snowden--this is for you!
Авторство - отримай номер який тільки ти міняєш, яке всякий провірє. Вставляй повідомлень 9kB. (Нескінченна автентифікація даних незалежно від типу чи симетрії шифрування.)