SimpleBouncer is an open source (Apache License, Version 2.0) Java network proxy. Do not require any external lib.
Current Stable Version is 1.5.3
- Machine-A (Client) init connection to Machine-B (Bouncer)
- Machine-B init connection to Machine-C (Server)
- Done: Machine-A is able to speak with Machine-C
- Machine-A (Client) may be in Internal network.
- Machine-B (Bouncer) may be in DMZ.
- Machine-C (Server) may be in External network.
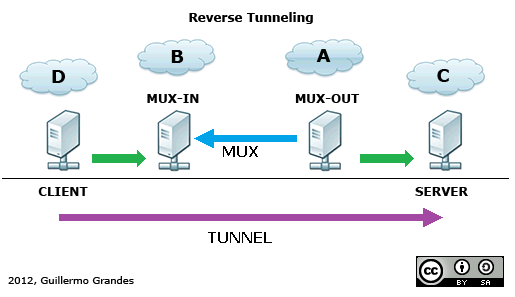
- Machine-A (MUX-OUT) init connection to Machine-B (MUX-IN)
- Machine-D (Client) init connection to Machine-B
- Machine-B request to Machine-A new SubChannel over MUX (Tunnel).
- Machine-A open connection to Machine-C (Server).
- Done: Machine-D is able to speak with Machine-C
- Machine-B (MUX-IN) should be in DMZ.
- Machine-A (MUX-OUT) and Machine-C (Server) may be in internal network.
# To redir stdout/stderr to (auto-daily-rotated) files you can use:
-Dlog.stdOutFile=/var/log/bouncer.out -Dlog.stdErrFile=/var/log/bouncer.err
# To log to stdout too:
-Dlog.stdToo=true
Filenames are a base-pattern, output files they will be: bouncer.xxx.YEAR-MONTH-DAY (bouncer.xxx.2012-12-31)
Config file must be in class-path, general format is:
# <left-addr> <left-port> <right-addr> <right-port> [options]
- Options for outgoing connections
- Loadbalancing/Failover (only one option can be used)
- LB=ORDER: active failover-only in DNS order
- LB=RR: active LoadBalancing in DNS order (round-robin)
- LB=RAND: activate LoadBalancing in DNS random order
- Loadbalancing/Failover (only one option can be used)
- Options for Simple Forward (rinetd)
- TUN=SSL: activate SSL tunneling (origin is plain, destination is SSL)
- Options for Reverse Tunneling (MUX)
- Select operation of MUX (only one option can be used)
- MUX=IN: activate input-terminator multiplexor
- MUX=OUT: activate output-initiator multiplexor
- Options for encryption (optional -AES or SSL or NONE-):
- MUX=AES: activate AES encryption in multiplexor (see AES=key)
- AES=key: specify the key for AES (no white spaces, no comma sign, no equals sign)
- MUX=SSL: activate SSL encryption in multiplexor (see SSL=xxx)
- SSL=server.crt:server.key:client.crt: specify files for SSL config (server/mux-in)
- SSL=client.crt:client.key:server.crt: specify files for SSL config (client/mux-out)
- MUX=AES: activate AES encryption in multiplexor (see AES=key)
- Select operation of MUX (only one option can be used)
- If use MUX=SSL
- Keys/Certificates are pairs, must be configured in the two ends (MUX-IN & MUX-OUT)
- files.crt are X.509 public certificates
- files.key are RSA Keys in PKCS#8 format (no encrypted)
- files.crt/.key must be in class-path like "bouncer.conf"
- be careful about permissions of "files.key" (unix permission 600 may be good)
- If use MUX=AES, you need to protect the "bouncer.conf" from indiscrete eyes (unix permission 600 may be good)
# <listen-addr> <listen-port> <remote-addr> <remote-port> [options]
0.0.0.0 1234 127.1.2.3 9876
127.0.0.1 5678 encrypted.google.com 443 LB=RR,TUN=SSL
Example config of Reverse tunnels (equivalent ssh -p 5555 192.168.2.1 -R 127.0.0.1:8080:192.168.1.1:80)
# <remote-addr> <remote-port> <remote-tun-addr> <remote-tun-port> MUX-OUT
192.168.1.1 80 192.168.2.1 5555 MUX=OUT
# <listen-tun-addr> <listen-tun-port> <listen-addr> <listen-port> MUX-IN
192.168.2.1 5555 127.0.0.1 8080 MUX=IN
# <remote-addr> <remote-port> <remote-tun-addr> <remote-tun-port> MUX-OUT
192.168.1.1 80 192.168.2.1 5555 MUX=OUT,MUX=SSL,SSL=peerA.crt:peerA.key:peerB.crt
# <listen-tun-addr> <listen-tun-port> <listen-addr> <listen-port> MUX-IN
192.168.2.1 5555 127.0.0.1 8080 MUX=IN,MUX=SSL,SSL=peerB.crt:peerB.key:peerA.crt
mkdir classes
javac -d classes/ src/net/bouncer/SimpleBouncer.java
# KeyGenerator compilation can output warnings about Sun proprietary API (you can safely ignore it)
javac -d classes/ src/net/bouncer/KeyGenerator.java
jar cvf bouncer-x.y.z.jar -C classes/ .
java -cp .:bouncer-x.y.z.jar net.bouncer.KeyGenerator <bits> <days> <CommonName> <filename-without-extension>
java -cp .:bouncer-x.y.z.jar net.bouncer.SimpleBouncer
- NIO?
- JMX?
- Multiple remote-addr (not only multi DNS A-record)?
- Use Log4J
- Limit number of connections
- Limit absolute timeout/TTL of a connection
- Configurable retry-sleeps
- Allow different tunnels over same MUX(IN/OUT)
- Reload config (v1.1)
- Thread pool/control (v1.2)
- Reverse tunnels (like ssh -R) over MUX (multiplexed channels) (v1.2)
- FlowControl in MUX (v1.3)
- Custom timeout by binding (v1.4)
- Encryption MUX/Tunnel (AES+PreSharedSecret) (v1.4)
- Manage better the read timeouts (full-duplex) (v1.4)
- Encryption MUX/Tunnel (SSL/TLS) (v1.5)
- Key Generator for MUX-SSL/TLS (v1.5)
- Audit threads / connections (v1.5)
- Improved FlowControl in MUX (v1.5)
- Allow redir stdout/stderr to File, with auto daily-rotate (v1.5.1)
Current harcoded values:
- Buffer length for I/O: 4096bytes
- IO-Buffers: 8
- TCP
SO_SNDBUF/SO_RCVBUF: BufferLength * IO-Buffers - Connection timeout: 30seconds
- Read timeout: 5minutes
- MUX Read timeout / keep-alive: 30seconds
- MUX-IN Error retry sleep: 0.5/1seconds
- MUX-OUT Error retry sleep: 5seconds
- Reload config check time interval: 10seconds
- Reset Initialization Vector (IV) for MUX-AES: { Iterations: 64K, Data: 16MB }
- For MUX-AES encryption/transformation are AES/CBC/PKCS5Padding
- For MUX-SSL supported Asymmetric Keys are RSA
- For MUX-SSL enabled Protocols are:
TLSv1SSLv3
- For MUX-SSL enabled CipherSuites are:
TLS_RSA_WITH_AES_256_CBC_SHA- For AES-256 you need JCE Unlimited Strength
TLS_RSA_WITH_AES_128_CBC_SHASSL_RSA_WITH_3DES_EDE_CBC_SHASSL_RSA_WITH_RC4_128_SHA
- Shutdown/Reload timeout: 30seconds
| Direct | Forward | MUX | MUX-AES | MUX-SSL | |
|---|---|---|---|---|---|
| Mbytes | 39.9 | 31.2 | 20.8 | 7.0 | 7.4 |
| Mbits | 319 | 249 | 166 | 56 | 59 |
Inspired in rinetd, stunnel and openssh, this bouncer is Java-minimalistic version.