-
Notifications
You must be signed in to change notification settings - Fork 82
PHPRedirector
Whenever a user consents to an OAuth app their browser sends a request to a specified redirect URI to provide an authorization code. The PHPRedirector folder contains code that can be hosted on a web server to capture an OAuth authorization code as well as complete the OAuth flow.
Start by creating your web server of choice. I personally like to use Azure App Services for this piece. You can spin up an Azure App Service site for free that gets a .azurewebsites.net address. With Azure App Services, the web root is located at /home/site/wwwroot/. Copy the files in the PHPRedirector folder from this repo to the web root and then move the AutoOAuthFlow.py script to /home/.
This is the main file that writes any OAuth codes received in web requests sent to the server. Codes get written to a codes.txt file as well as codes-bak.txt. When the AutoOAuthFlow.py script is running it watches the codes.txt file and then completes the OAuth flow with any codes written to it.
Redirects to "https://outlook.office365.com" by default. You can modify this if you want to redirect the user somewhere else.
Main landing page that loads ip.php and login.php. Nothing to change here.
In situations where the user that is consenting to an app is remote you may want to automatically complete the OAuth flow and obtain access and refresh tokens. This script facilitates this ability while writing any access tokens to a file on disk called access_tokens.txt. This is why it is very important to not run this in the web root. If you do so you may expose access tokens on a public web server.
Install dependencies:
apt-get install python3-pip
pip install watchdog requestsThe script requires that you pass it 4 parameters. These parameters are listed below. The client ID and secret are for the OAuth app (service principal) itself, not the App Service. If you ran Invoke-InjectOAuthApp these are provided in the output.
--OPTIONS--
client-id - The Client ID (AppID) of the App
secret - The Secret of the App
redirect-uri - The Redirect URI used in the authorization request
scope - Permission scope of the app "Mail.Read openid etc"
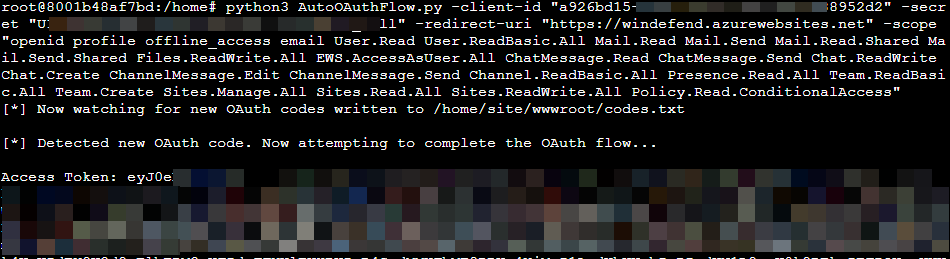
When you are ready to capture codes you can run AutoOAuthFlow.py to watch for new OAuth codes and complete the flow using your App credentials. Whenever a web request is sent to the web server that contains an OAuth code it will be written to codes-bak.txt and will be used to attempt OAuth flow completion to obtain access tokens. If successful, the access tokens will be written to access_tokens.txt in the same directory as the Python script.
python3 AutoOAuthFlow.py -client-id "13483541-1337-4a13-1234-0123456789ABC" -secret "v-Q8Q~fEXAMPLEEXAMPLEDsmKpQw_Wwd57-albMZ" -redirect-uri "https://<your azure app>.azurewebsites.net" -scope "openid profile offline_access email User.Read User.ReadBasic.All Mail.Read"