-
Notifications
You must be signed in to change notification settings - Fork 460
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Merge branch 'refactoring-deployment-template-2' into refactoring-dep…
…loyment-template-3
- Loading branch information
Showing
108 changed files
with
13,596 additions
and
191 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
37 changes: 37 additions & 0 deletions
37
docs/user-guide/global-configurations/authorization/sso/github.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,37 @@ | ||
| # GitHub | ||
|
|
||
| ## Sample Configuration | ||
|
|
||
| 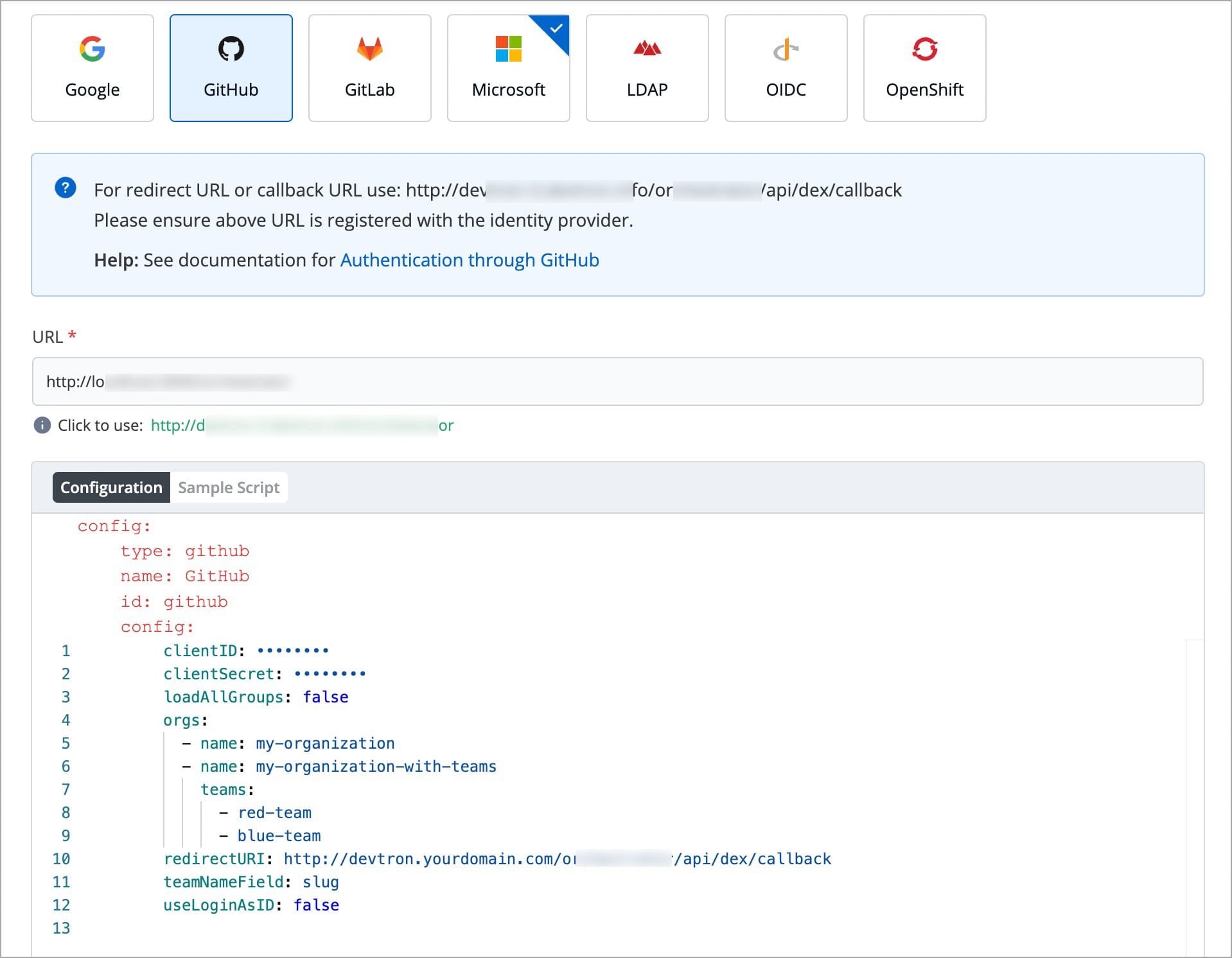 | ||
|
|
||
| --- | ||
|
|
||
| ## Values You Would Require at SSO Provider | ||
|
|
||
| Devtron provides a sample configuration out of the box. There are some values that you need to either get from your SSO provider or give to your SSO provider. | ||
|
|
||
| ### Values to Fetch | ||
|
|
||
| * clientID | ||
|
|
||
| * clientSecret | ||
|
|
||
|  | ||
|
|
||
| ### Values to Provide | ||
|
|
||
| * redirectURI (provided in SSO Login Services by Devtron) | ||
|
|
||
| 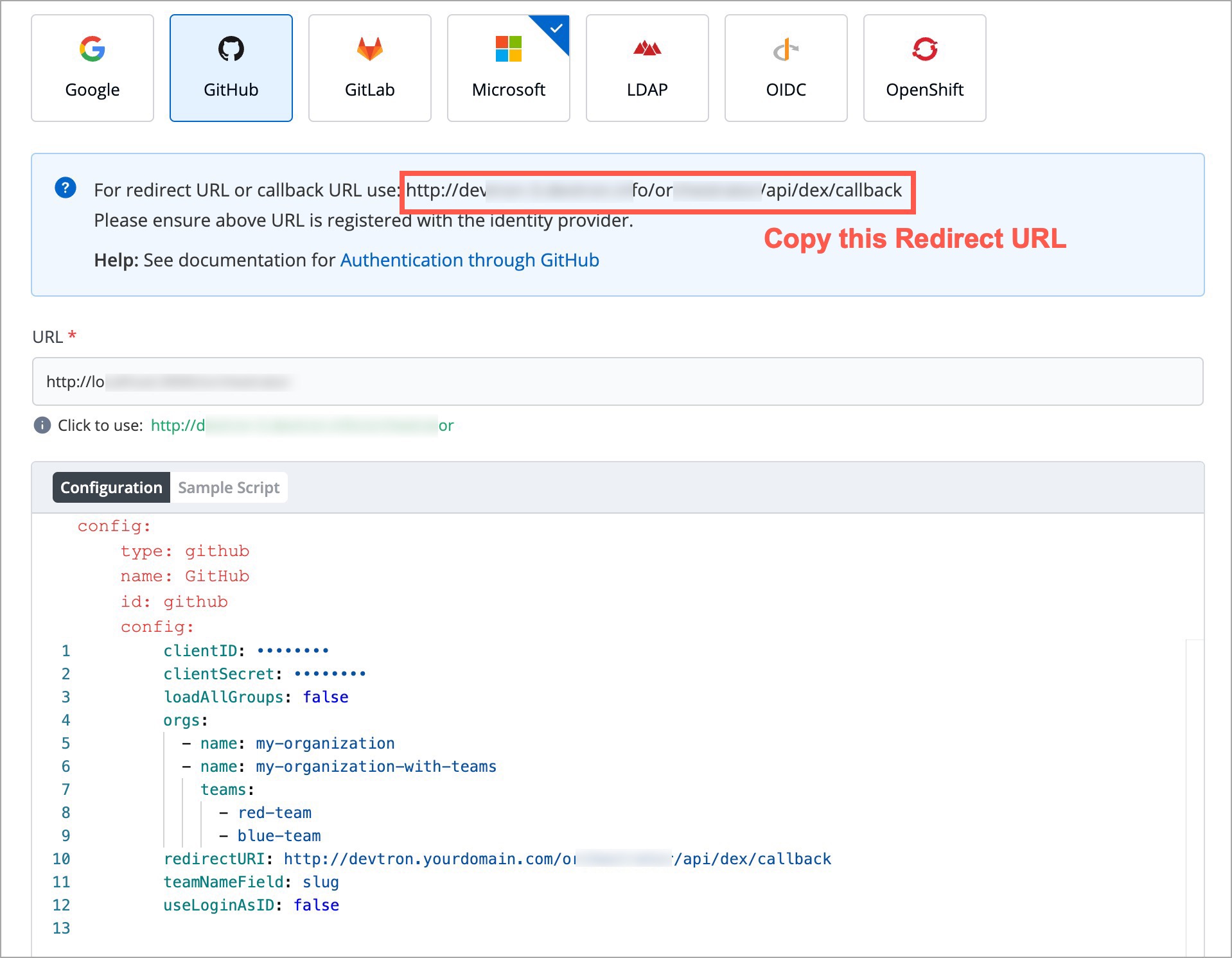 | ||
|
|
||
|  | ||
|
|
||
| --- | ||
|
|
||
| ## Reference | ||
|
|
||
| * [View GitHub Documentation](https://docs.github.com/en/apps/oauth-apps/building-oauth-apps/creating-an-oauth-app) | ||
|
|
||
| * [View Dex IdP Documentation](https://dexidp.io/docs/connectors/github/) | ||
|
|
||
|
|
35 changes: 35 additions & 0 deletions
35
docs/user-guide/global-configurations/authorization/sso/gitlab.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,35 @@ | ||
| # GitLab | ||
|
|
||
| ## Sample Configuration | ||
|
|
||
| 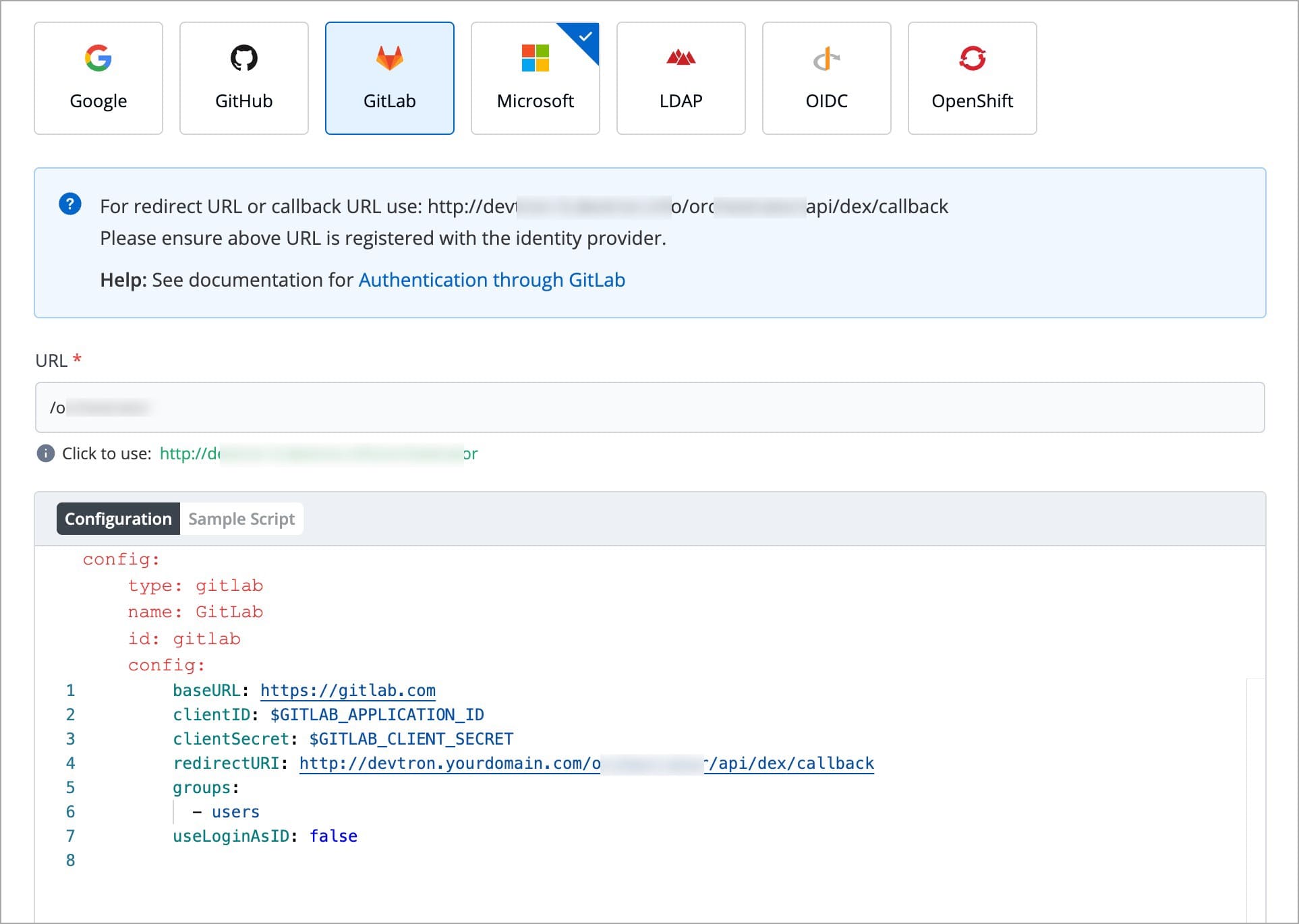 | ||
|
|
||
| --- | ||
|
|
||
| ## Values You Would Require at SSO Provider | ||
|
|
||
| Devtron provides a sample configuration out of the box. There are some values that you need to either get from your SSO provider or give to your SSO provider. | ||
|
|
||
| ### Values to Fetch | ||
|
|
||
| * clientID | ||
| * clientSecret | ||
|
|
||
| 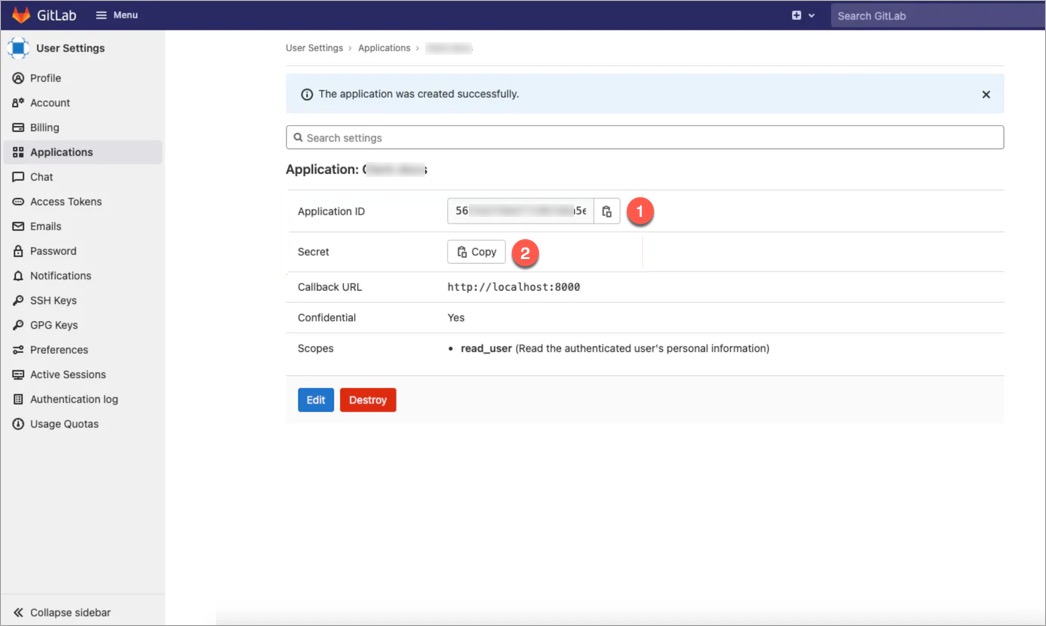 | ||
|
|
||
| ### Values to Provide | ||
|
|
||
| * redirectURI (provided in SSO Login Services by Devtron) | ||
|
|
||
| 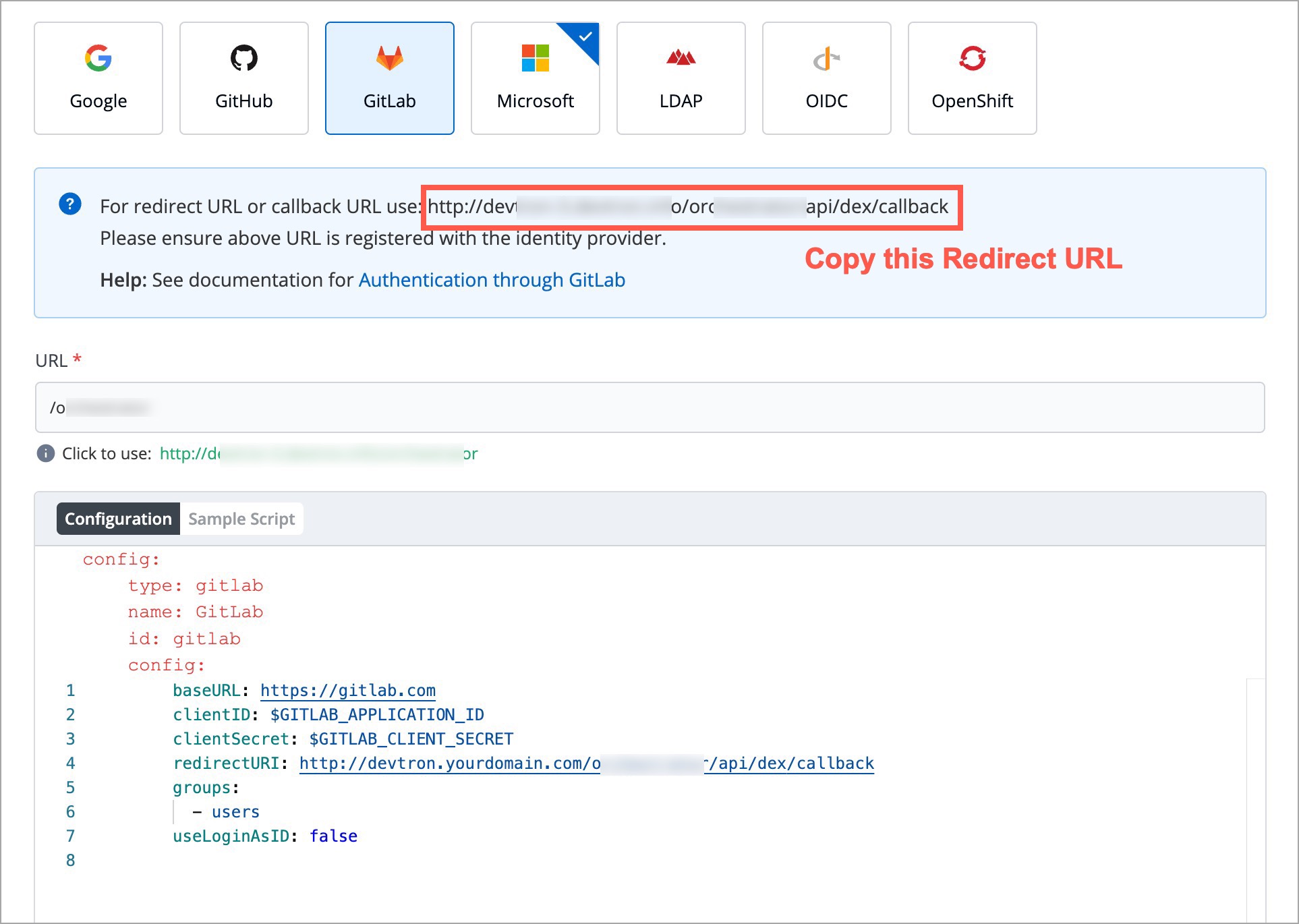 | ||
|
|
||
|  | ||
|
|
||
| --- | ||
|
|
||
| ## Reference | ||
|
|
||
| * [View GitLab Documentation](https://docs.gitlab.com/ee/integration/oauth_provider.html) | ||
|
|
||
| * [View Dex IdP Documentation](https://dexidp.io/docs/connectors/gitlab/) | ||
|
|
39 changes: 39 additions & 0 deletions
39
docs/user-guide/global-configurations/authorization/sso/google.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,39 @@ | ||
|
|
||
| ## Sample Configuration | ||
|
|
||
|  | ||
|
|
||
| --- | ||
|
|
||
| ## Values You Would Require at SSO Provider | ||
|
|
||
| Devtron provides a sample configuration out of the box. There are some values that you need to either get from your SSO provider or give to your SSO provider. | ||
|
|
||
| ### Values to Fetch | ||
|
|
||
| * clientID | ||
|
|
||
| * clientSecret | ||
|
|
||
| 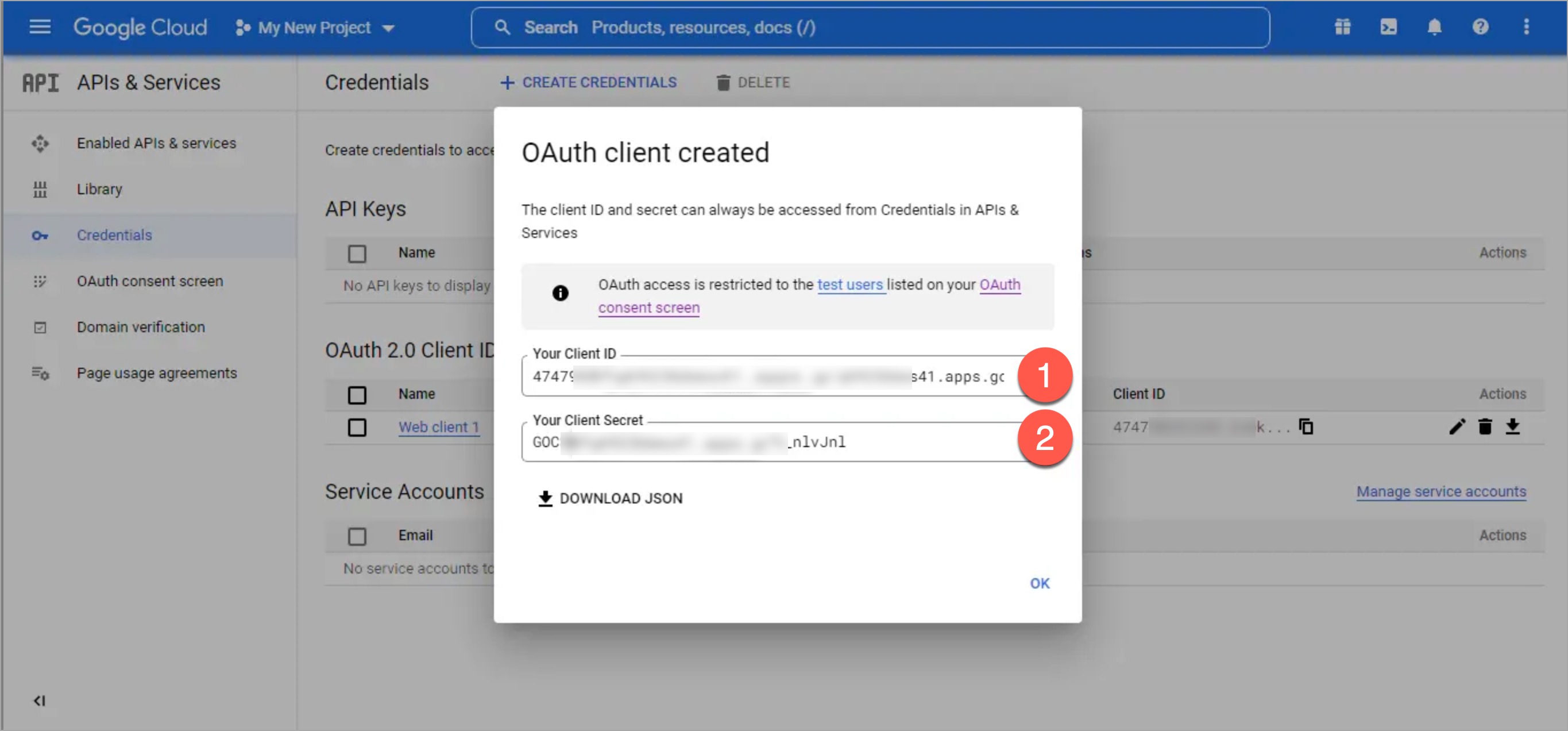 | ||
|
|
||
|
|
||
| ### Values to Provide | ||
|
|
||
| * redirectURI (provided in SSO Login Services by Devtron) | ||
|
|
||
| 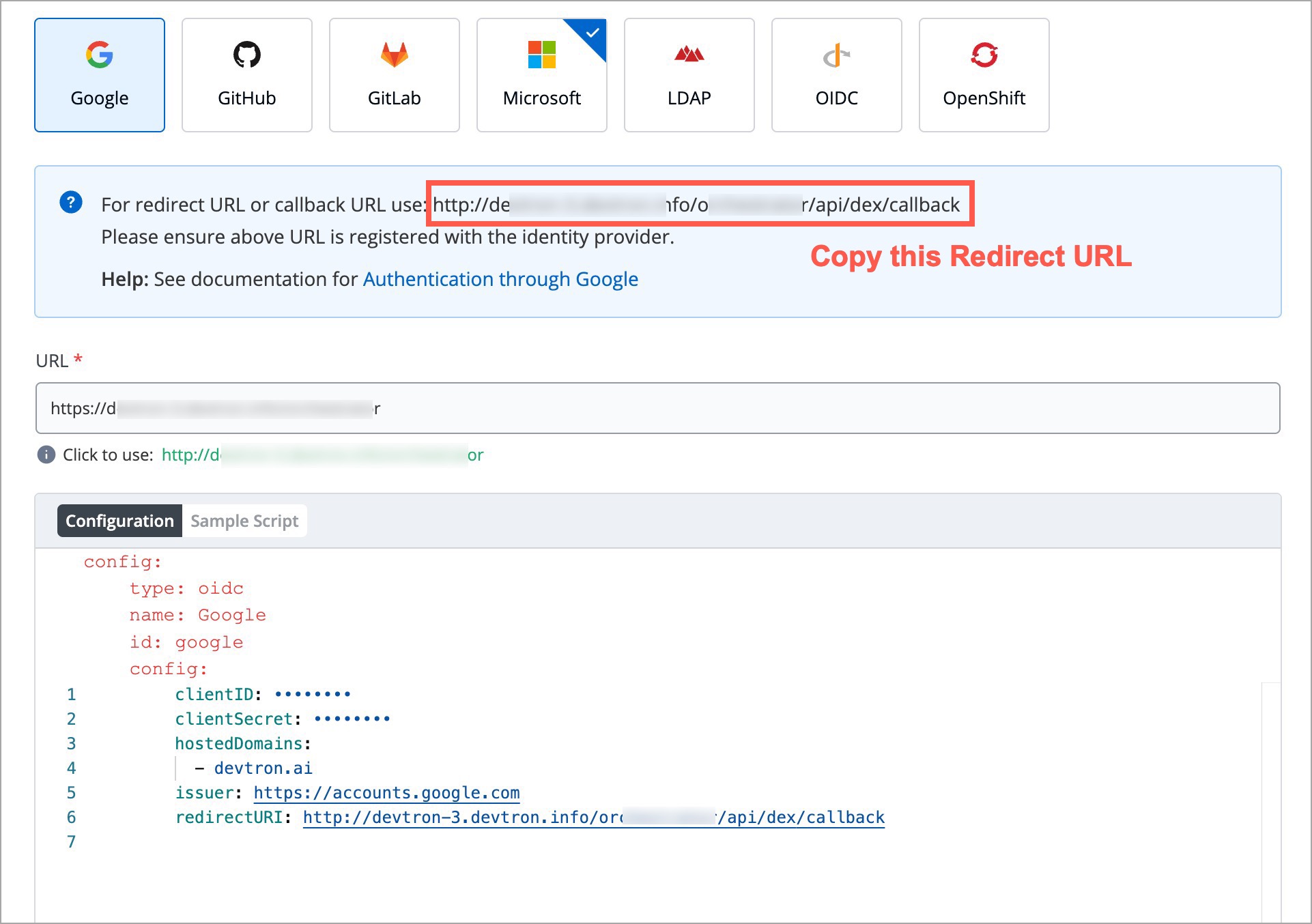 | ||
|
|
||
|  | ||
|
|
||
| --- | ||
|
|
||
| ## Reference | ||
|
|
||
| * [View Google Documentation](https://developers.google.com/identity/gsi/web/guides/get-google-api-clientid) | ||
|
|
||
| * [View Dex IdP Documentation](https://dexidp.io/docs/connectors/google/) | ||
|
|
||
|
|
||
|
|
50 changes: 50 additions & 0 deletions
50
docs/user-guide/global-configurations/authorization/sso/ldap.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,50 @@ | ||
| # LDAP | ||
|
|
||
| ## Sample Configuration | ||
|
|
||
|  | ||
|
|
||
| --- | ||
|
|
||
| ## Values to fetch from LDAP | ||
|
|
||
| Devtron provides a sample configuration out of the box. Here are some values you need to fetch from your LDAP. | ||
|
|
||
| * bindDN | ||
| * bindPW | ||
| * baseDN | ||
|
|
||
| --- | ||
|
|
||
| ## Reference | ||
|
|
||
| [What is LDAP](https://www.okta.com/identity-101/what-is-ldap/) | ||
|
|
||
| --- | ||
|
|
||
| ## Auto-assign Permissions [](https://devtron.ai/pricing) | ||
|
|
||
| Since LDAP supports creation of User Groups, this feature simplifies the onboarding process of organizations having a large headcount of users. It also eliminates repetitive permission assignment by automatically mapping your LDAP User groups to Devtron's [Permission Groups](../permission-groups.md) during single sign-on (SSO) login. | ||
|
|
||
| 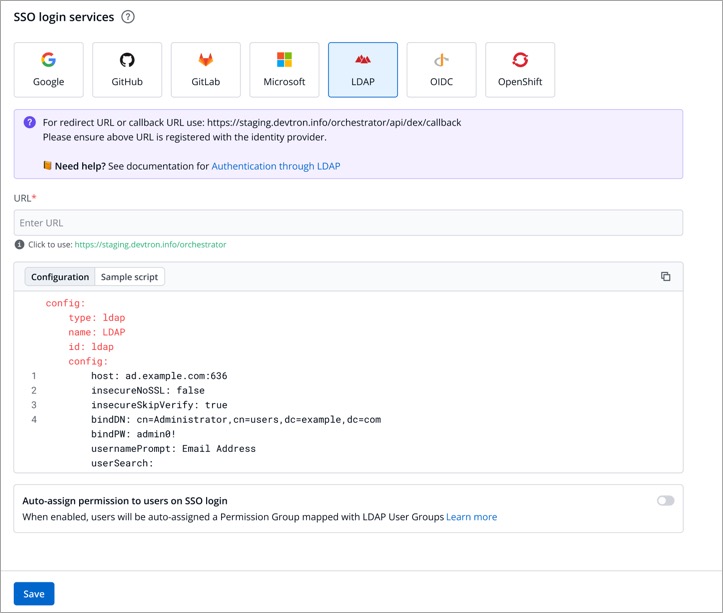 | ||
|
|
||
| If you've created user groups in LDAP, you can create corresponding permission groups in Devtron with the same names. When members of those user groups first log in to Devtron, they'll automatically inherit the permissions from their Devtron permission group. This means you can't manually adjust or add [individual permissions for users](../user-access.md) mapped to a permission group. | ||
|
|
||
| {% hint style="warning" %} | ||
| SSO login requires exact matching between Devtron permission group names and LDAP user groups. Any discrepancies or missing groups will prevent successful login. | ||
|
|
||
| Once you save the configuration with this auto-assign feature enabled, existing user permissions will be cleared and the future permissions will be managed through [Permission Groups](../permission-groups.md) linked to LDAP user groups. | ||
| {% endhint %} | ||
|
|
||
| {% hint style="info" %} | ||
| If you're missing some permissions that you know you should have, try logging out and signing back in to Devtron. This will refresh your permissions based on your latest LDAP user group. | ||
| {% endhint %} | ||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
Oops, something went wrong.