-
Notifications
You must be signed in to change notification settings - Fork 465
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
doc: HashiCorp external secret operator #3608
Changes from 2 commits
File filter
Filter by extension
Conversations
Jump to
Diff view
Diff view
There are no files selected for viewing
| Original file line number | Diff line number | Diff line change |
|---|---|---|
|
|
@@ -2,7 +2,7 @@ | |
|
|
||
| To add secrets from **AWS Secrets Manager**, we need to create a generic Kubernetes secret for AWS authentication. | ||
|
|
||
| Create a Kubernetes secret in the namespace in which the application is to be deployed using base64 encoded AWS access-key and secret-access-key. You can use devtron generic chart for this. | ||
| Create a Kubernetes secret in the namespace in which the application is to be deployed using base64 encoded AWS access-key and secret-access-key. You can use Devtron generic chart for this. | ||
|
|
||
| **Note:** You don't have to create the Kubernetes secret everytime you create External Secret for the respective namespace. | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Note: You don't have to create the Kubernetes secret every time you create an external secret for the respective namespace. |
||
|
|
||
|
|
||
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,59 @@ | ||
| # HashiCorp Vault | ||
|
|
||
| To incorporate secrets from **HashiCorp Vault**, you need to create a generic Kubernetes secret that will be used for vault authentication. This involves creating a Kubernetes secret in the specific namespace where your application will be deployed. | ||
| The secret should store the base64-encoded password or token obtained from vault. To simplify the process, you can utilize the Devtron generic chart. An example yaml is given below: | ||
|
|
||
| ```yaml | ||
| apiVersion: v1 | ||
| kind: Secret | ||
| type: Opaque | ||
| data: | ||
| token: <vault-password> | ||
| metadata: | ||
| name: vault-token | ||
| namespace: <namespace> | ||
| ``` | ||
|
|
||
| **Note:** Please note that you don't need to create the Kubernetes secret every time you create an External Secret for the corresponding namespace. | ||
|
|
||
| Once you have created the generic secret, follow these steps in the application's Secrets section: | ||
|
|
||
| **1. Create a new secret.** | ||
|
|
||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. 1. Create a new secret |
||
| To add a new secret to the application, go to the `App Configuration` section of the application. Then, navigate to the left pane and select the `Secrets` option and click on the `Add Secret` button. | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. To add a new secret to the application, go to the |
||
|
|
||
| 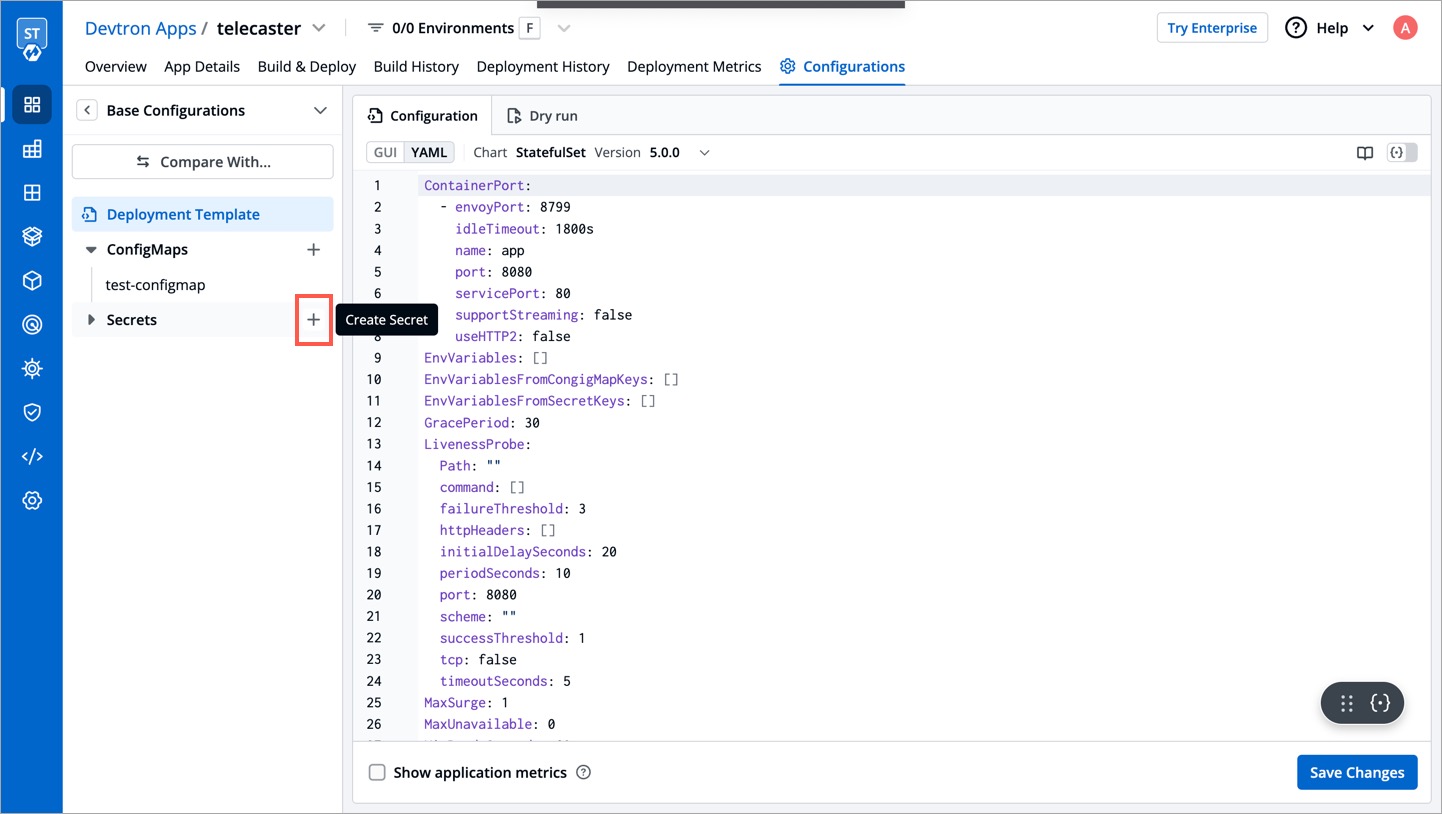 | ||
|
|
||
| **2. Select `HashiCorp Vault` as the External Secret Operator** | ||
|
|
||
| After clicking on the `Add Secret` button, select `HashiCorp Vault` from the dropdown menu for the `Data type` option. Provide a name for the secret you are creating, and then proceed to configure the external secret as described in the next step. | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. After clicking the Add Secret button, select |
||
|
|
||
| 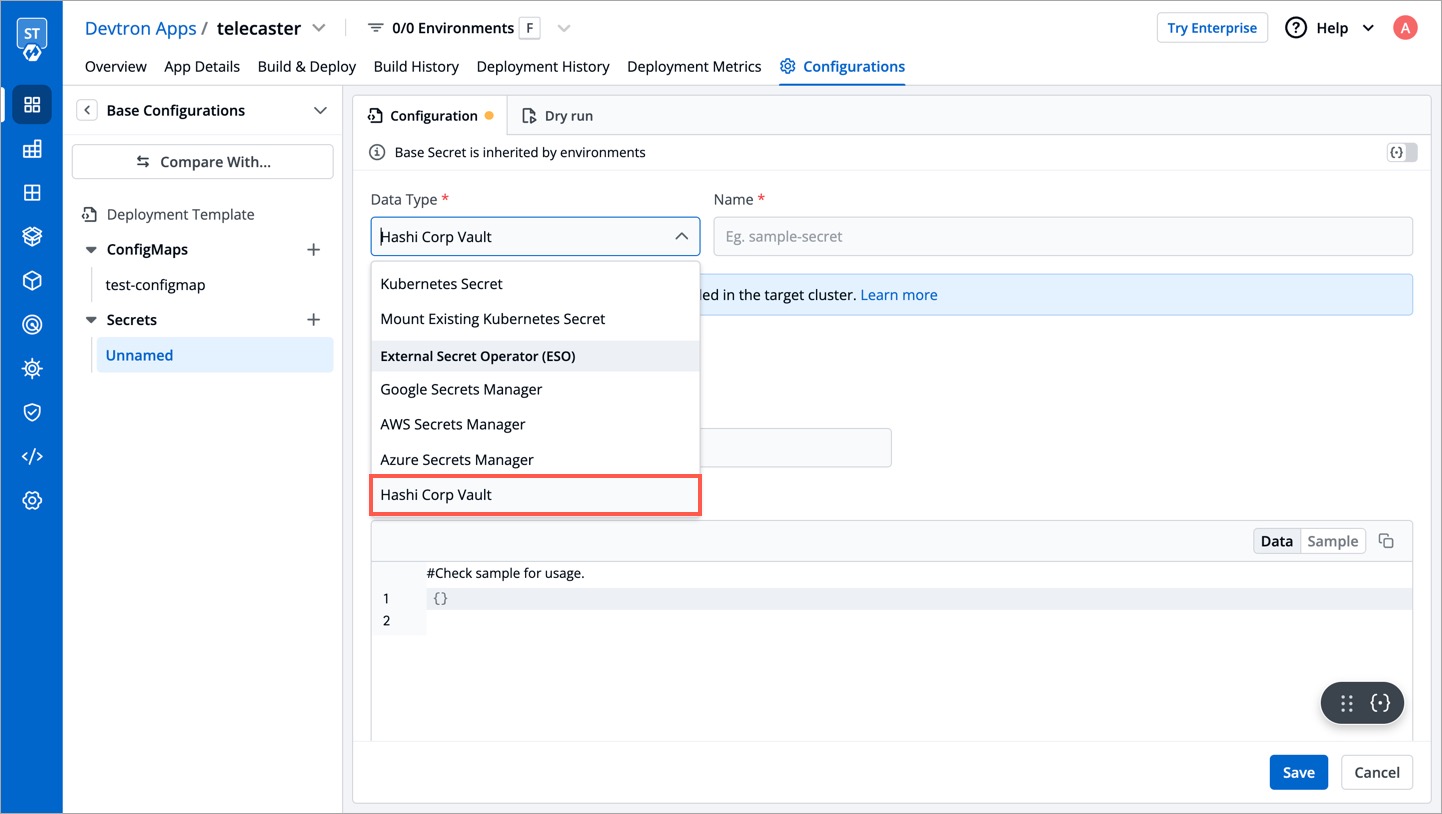 | ||
|
|
||
| **3. Configure secret:** | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. 3. Configure the secret |
||
|
|
||
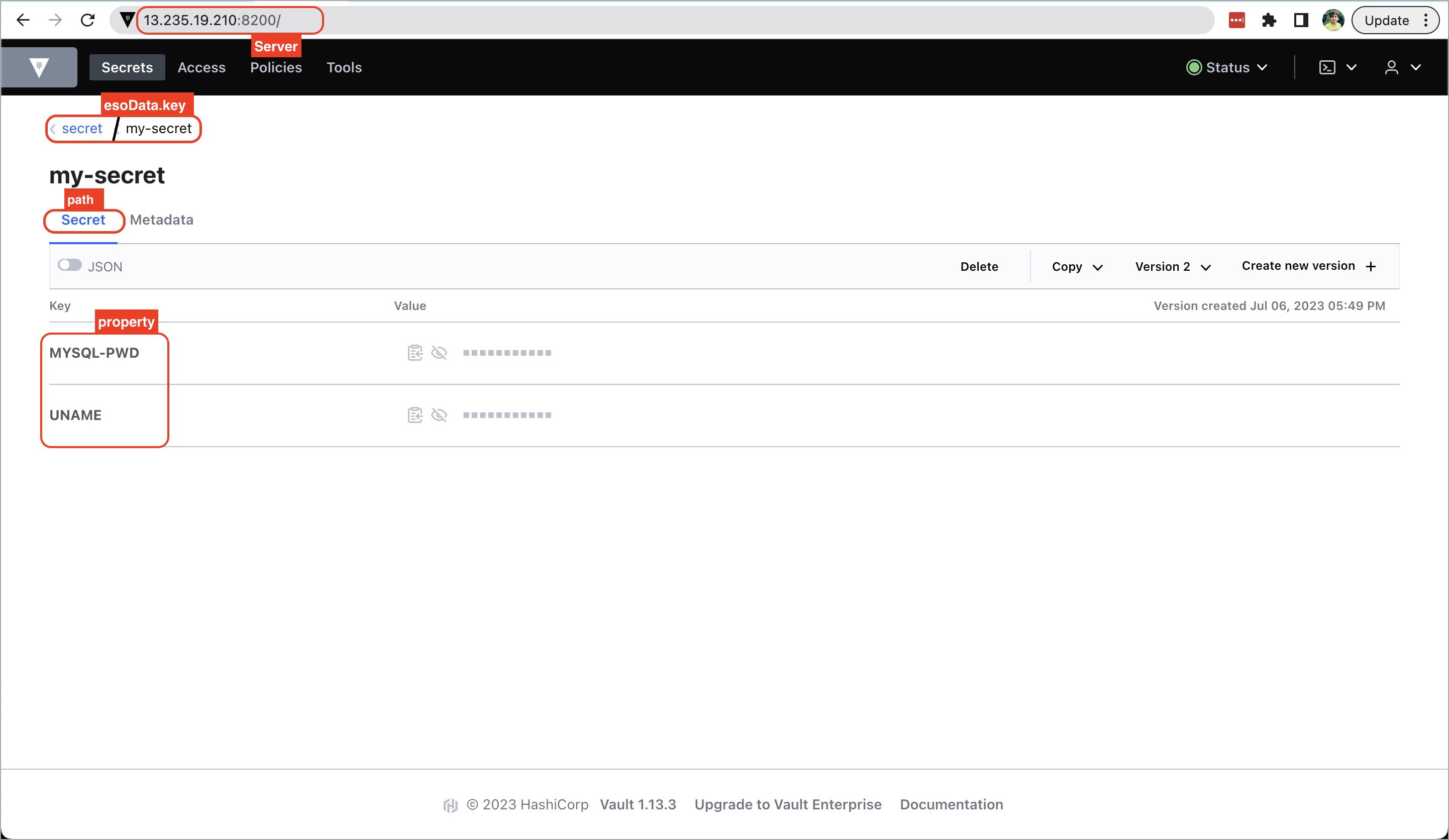
| To configure the external secret that will be fetched from HashiCorp Vault for your application, you will need to provide specific details using the following key-value pairs: | ||
|
|
||
| 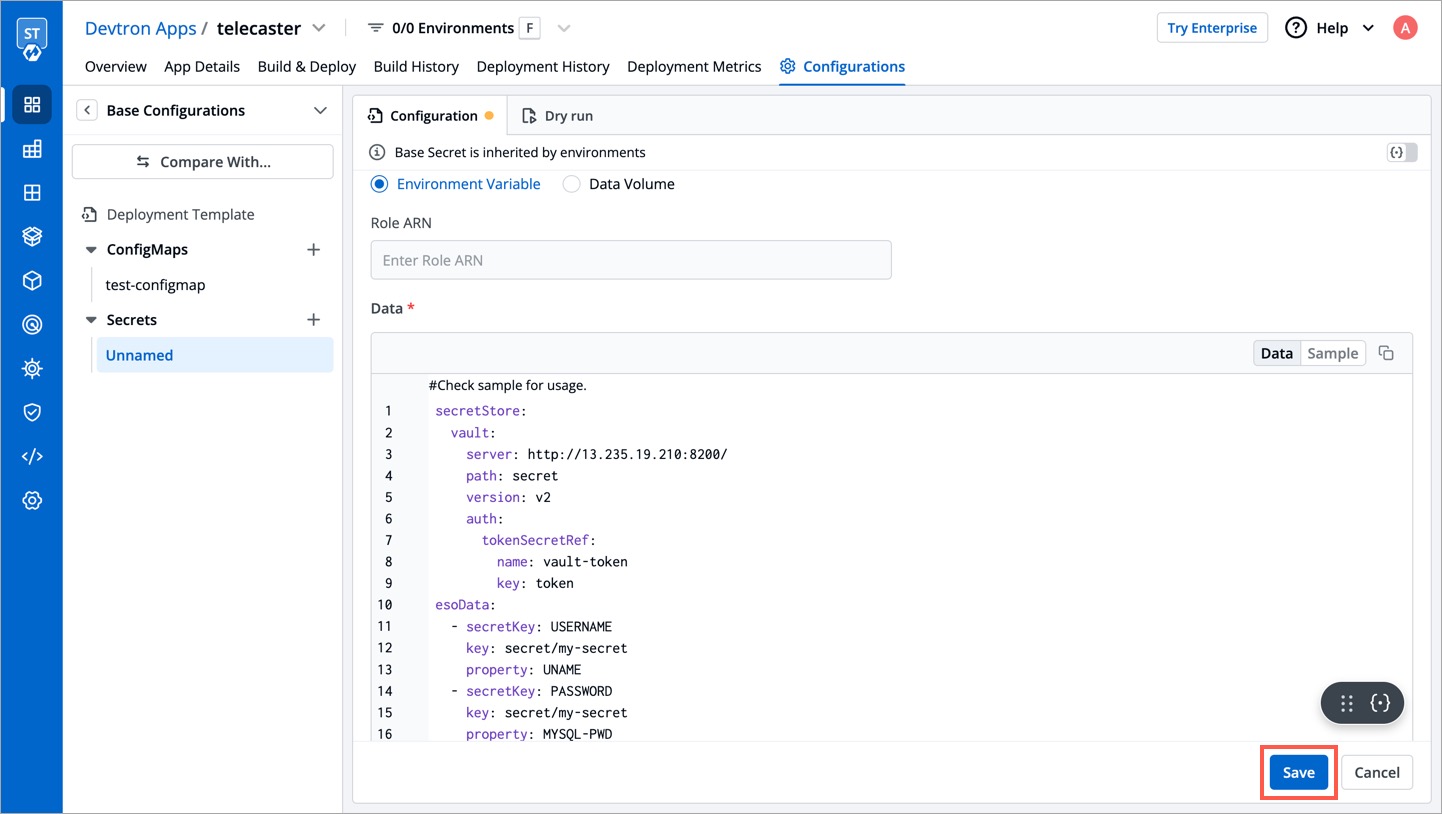 | ||
|
|
||
|
|
||
| | Key | Description | | ||
| | :--- | :--- | | ||
| | `vault.server` | Server is the connection address for the Vaultserver, e.g: "https://vault.example.com:8200". | | ||
| | `vault.path` | Specify the path where the secret is stored in Vault. | | ||
| | `tokenSecretRef.name` | Enter the name of the secret that will be used for authentication. | | ||
| | `tokenSecretRef.key` | Specify the key name within the secret that contains the token. | | ||
| | `secretKey` | Provide a name for the secret in Kubernetes. | | ||
| | `key` | Enter the name of the secret in Vault. | | ||
| | `property` | Specify the key within the Vault secret. | | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Remove full-stop after each one-liner description in the table |
||
|
|
||
| 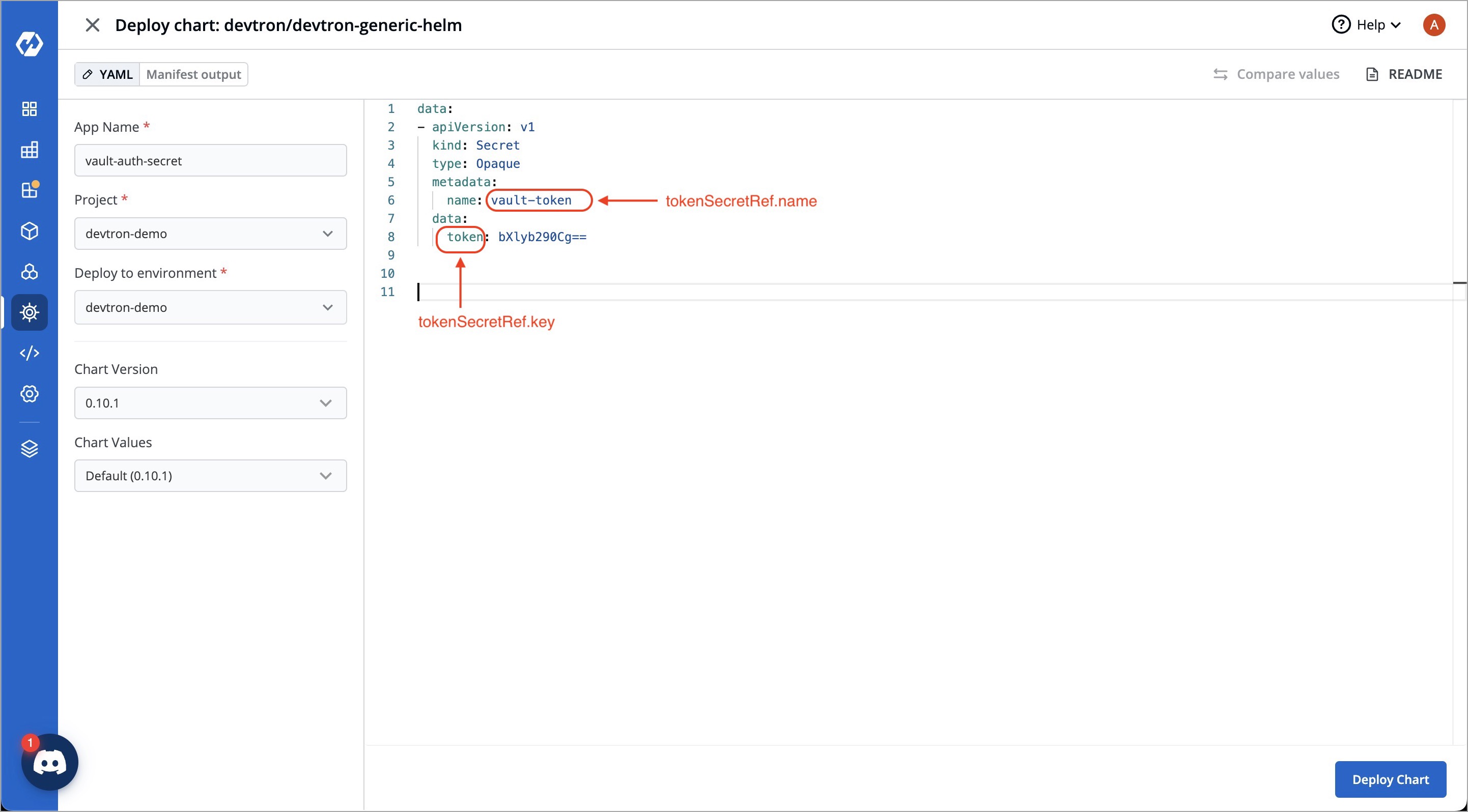 | ||
|
|
||
|  | ||
|
|
||
| **4. Save secret.** | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. 4. Save the secret |
||
|
|
||
| After configuring the external secret from HashiCorp Vault, proceed to save the secret by clicking on the `Save` button. | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. After configuring the external secret from HashiCorp Vault, proceed to save the secret by clicking the Save button. |
||
|
|
||
| By following the steps mentioned above and configuring these values correctly, you can seamlessly fetch and utilize external secrets from HashiCorp Vault within your application environment by deploying the application. | ||
|
|
||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Create a Kubernetes secret in the namespace in which the application is to be deployed using base64 encoded AWS access-key and secret-access-key. You can use a Devtron generic chart for it.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
You can use a Devtron generic chart for to achieve it. ?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@Shubham9t9, I have changed the sentence.