This issue was moved to a discussion.
You can continue the conversation there. Go to discussion →
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Implementing custom oauth2 provider #12151
Comments
|
My best guess is the "refresh_token" is being rejected by the provider. If you could enable EDIT: I can actually see in the logs that the users "refresh_token" is being rejected by netexplorer. When an oauth provider rejects the "refresh_token" (by throwing the "invalid_grant" error) we try and get a new "refresh_token" by forcing the user to re-authenticate with So for some reason when calling your oauth provider with |
|
Thanks for helping, Edit: Getting logs... I noticed the behavior you described. When i am redirected for a first time to directus i am redirected back to netexplorer and finally back to directus after accepting everything. I never tried the code_challenge/code_challenge_method with them. I don't know if there is a way to disable that to have a more basic case? I was thinking of redoing the oauth2 myself with a customized endpoint if there is no solution. |
|
Really you shouldn't need to use a custom implementation. The issue is that the "refresh_token" is becoming invalidated at some point and netexplorer isn't sending us a new one. Directus will always update the "refresh_token" if the provider sends us one... we just need to figure out how to get a new "refresh_token" from the provider, or if the token they're sending us is even valid to begin with? If you could query netexplorer about those points it might help us address this issue. Right now the problem does appear to be on their side. |
|
Formatted some logs I'll contact them tomorrow and see what i can get. I'll come back there when it's done ! Thanks. |
|
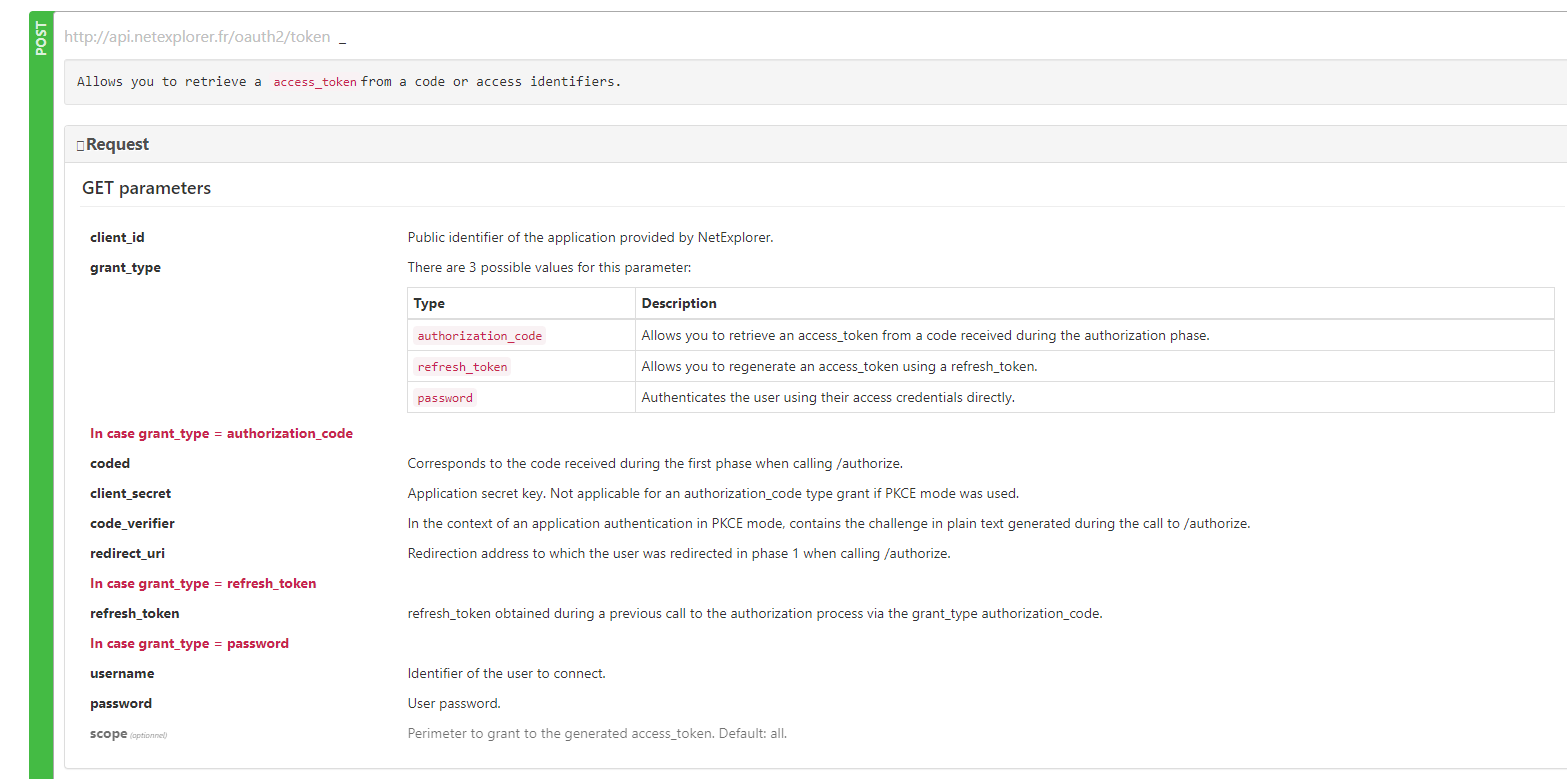
Looking at the detailed logs I can see that it's the initial token request that's failing. So for some reason the token endpoint just throws a grant error when we're trying to get the initial "access_token". 🤔 I notice in their docs it says the token endpoint expects the parameter "coded", but that's pretty non-standard. The library we use ("openid-client") sends the standard "code" parameter. Or maybe that's just google translate being weird? Otherwise we seem complaint. |
|
I can confirm it's google translate being weird. But i remember having this problem earlier with their API. |
|
Hi, I just simulated the directus integration with a custom made server in node.js. |
|
Unfortunately we don't currently offer any other oauth flows. We use PKCE as it is the recommended flow. If you really need it you could modify the oauth provider in a local build until NetExplorer fix their implementation. |
|
I'll move this to a discussion, as it's technically discussing a different/new oauth flow that's considered a new feature 👍🏻 |
This issue was moved to a discussion.
You can continue the conversation there. Go to discussion →
Preflight Checklist
Describe the Bug
Hi,
I am having trouble implementing oauth2 with a provider named "NetExplorer".
Everything looks good to me, but when i am redirected to directus, I get the following error : "INVALID_TOKEN".
I decided to enable "trace" mode in the logging system and i get this error : "Invalid grant".
I already used this API on a custom made nodeJS server and oauth2 was working fine.
(There was a 'Content-Type': 'application/x-www-form-urlencoded' header i don't know if it can change something)
I noticed that directus was also adding a parameter "access_type=offline" while not supported by Netexplorer. But except that nothing out of the ordinary.
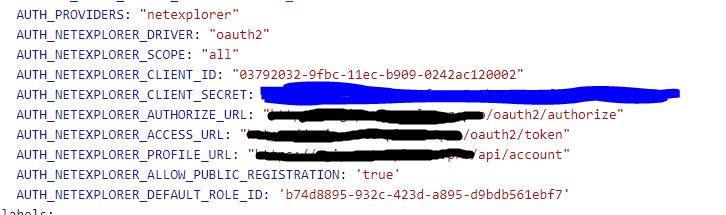
I linked my env and the documentation.
env
authorize


access
To Reproduce
Directus self hosted with docker
Created a redirect_uri in cooperation with NetExplorer (private api)
Try to use NetExplorer as a provider
Errors Shown
Error log on "trace" mode
After redirect from netexplorer to directus
What version of Directus are you using?
9.5.1
What version of Node.js are you using?
16.13.2
What database are you using?
postgre
What browser are you using?
chrome
What operating system are you using?
linux
How are you deploying Directus?
docker
The text was updated successfully, but these errors were encountered: