-
-
Notifications
You must be signed in to change notification settings - Fork 57
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
kvm: Windows 3.1 installation various crashes #1492
Comments
|
Does this have to do with the |
-D9+M as a start. |
No, just tested: with commit 1d8ca75 and a revert of 0db958a75d6082f847f421bcab1af1e311c1111a on top, this also occurs. |
|
Maybe you can bisect it then, please? :) |
|
Here is a log with But yeah a bisect is probably faster :) |
|
Maybe not, I'll look into the log a bit |
|
Please try native DPMI instead |
|
I've fixed something. |
|
Now dosemu2 crashed: |
|
There is something really weird |
|
You cannot reproduce it at all? I'm simply running the Windows 3.1 installation. |
|
Isn't native DPMI the default? I would say it needs about 2-3 times. |
|
No, its not default. |
|
Hehe indeed I'm getting closer to the point where the default was switch from native to KVM for DPMI :) I had totally missed or forgotten that was changed somehow. |
|
Yeah I cannot reproduce this with native DPMI. At least now it is clear what with KVM DPMI the issues pop up rather randomly. I hope this useful info! |
|
Could you please try the kvm_syn |
|
That one crashes before entering the graphical part with: |
|
OK, out of ideas, and it doesn't |
|
It almost seems like an out-of-sync |
We need that extension to be able to write to guest memory.
|
I applied some patch. |
May be needed because we frequently update LDT buffer from host. Guest should not cache it.
|
Now latest devel crashes for me each time before it would go in the graphical part as well: |
|
And if you just start windows, not install? |
|
That doesn't crash. |
|
Thanks for ssh. makes dosemu to not even start |
|
Without this change, KVM_SET_SREGS |
|
So is that a kernel problem? |
|
Could it also be a microcode bug? |
|
I very much suspect its an LDT |
This reverts commit 53ef318. KVM_CAP_SYNC_MMU description in kernel docs seems invalid. It says: --- When the KVM_CAP_SYNC_MMU capability is available, changes in the backing of the memory region are automatically reflected into the guest. --- But it seems like it is actually only needed when we mmap() that memory region to something else.
|
Could you please try this change? It will at least rule out the |
|
@sean-jc have suggested to disable Hope Sean can tell what to do next. :) |
|
@sean-jc I am getting mail rejects |
We don't use them (yet) as our guest does not do LTR or LLDT. But the proper GDT setup can avoid surprises in the future, for example if KVM adds more sanity checks.
|
This should now be fixed. If the problem persists please |
|
Now it crashes before entering the graphical part, I'll open another ticket. |
|
Cool, with this fix the KVM tests pass for me locally for the first time in many months. Thank you! |
|
So we ruled out invalid guest state |
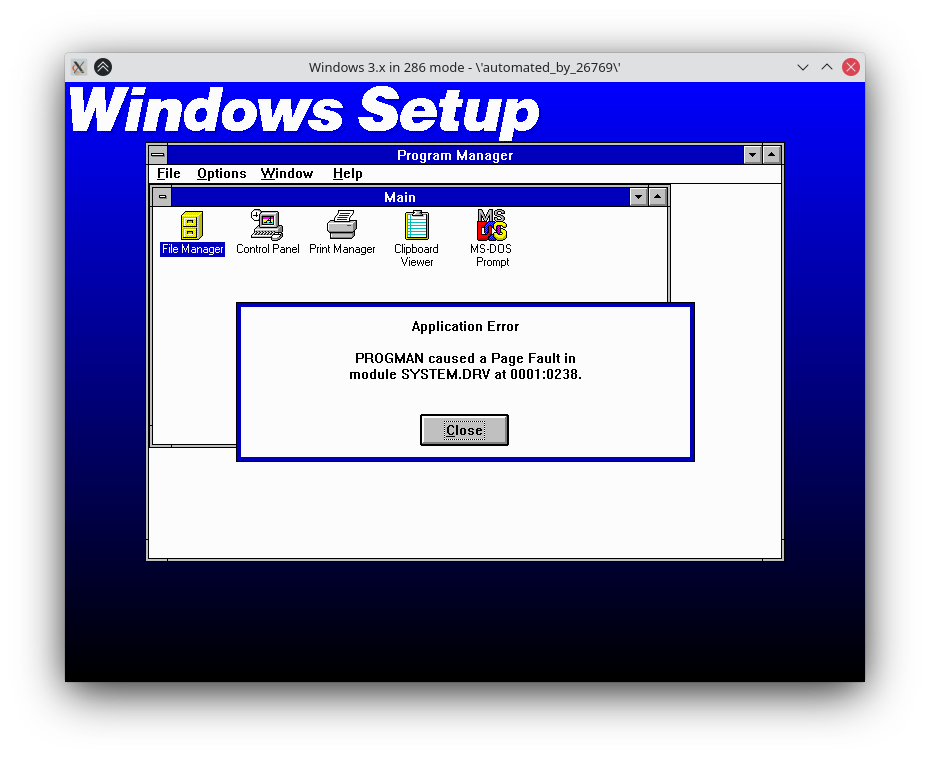
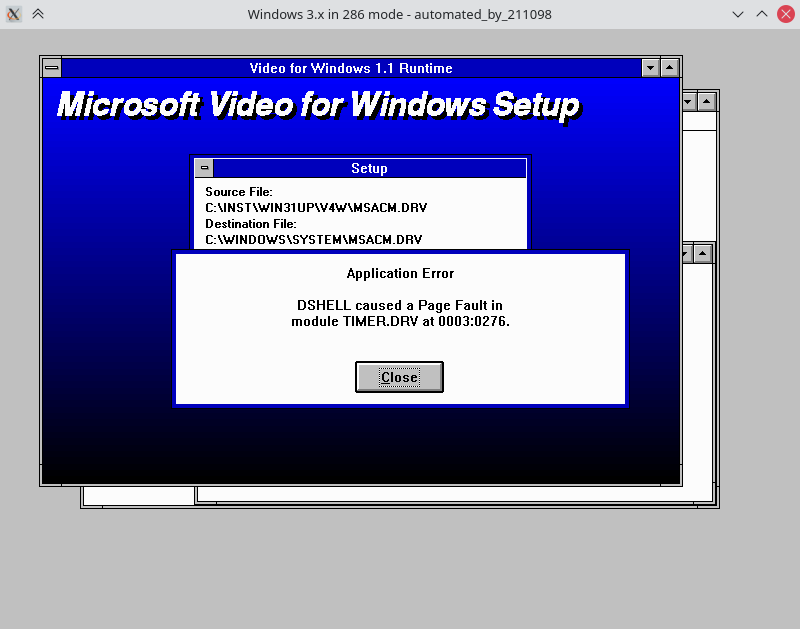


Describe the bug
When I try to install Windows 3.1 multiple times in a row:
To Reproduce
Steps to reproduce the behavior:
There will be different issues each time. My script still automates enough that I can do many installations in a row within 10-15 to test variants.
Attach the log
What would make sense here that I post sets of screenshots plus logs? Which debug options should I supply to start with? There is nothing notable in the default logs when this occurs now.
A regression?
It was more stable in the past. I could do many installations without running into any issues.
Additional info
This is with MS-DOS 6.22.
One variant that occurred right after playing the first sound when installing SB16 drivers after the Windows installation:

Another variant in the middle of the Windows installation:

The text was updated successfully, but these errors were encountered: